Preface: XSS attack can be either server-side or client-side.
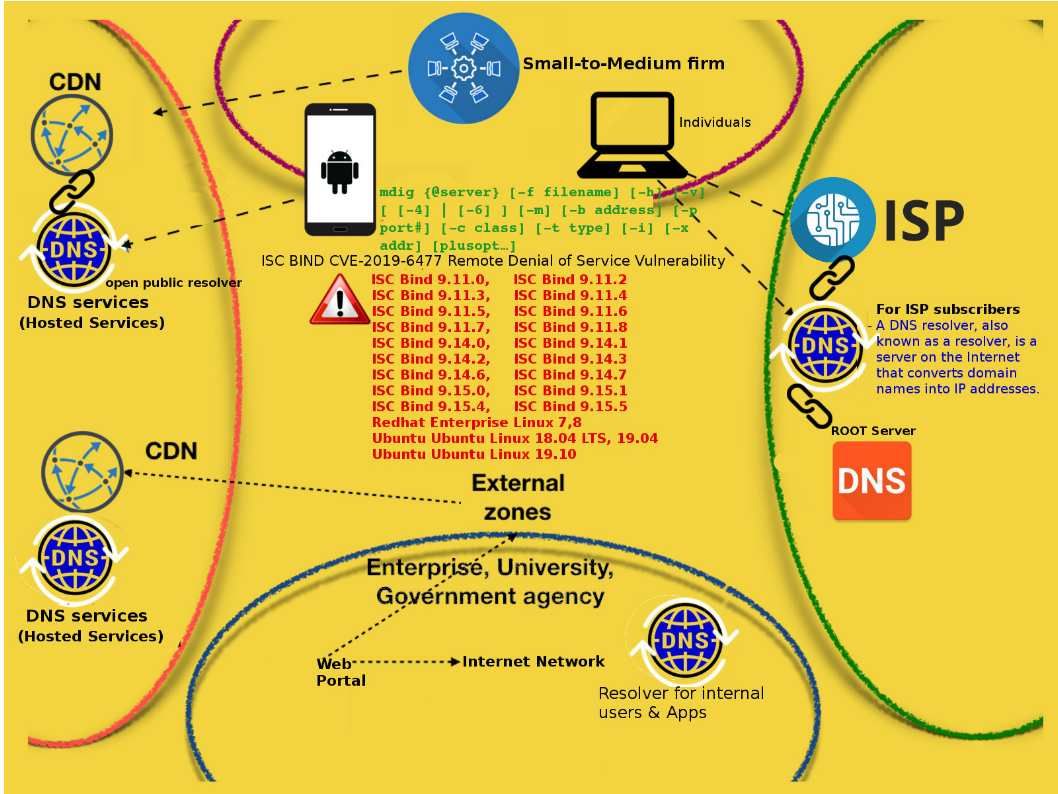
Vulnerability details: A vulnerability occurs on Outlook for Android that would allow an attacker to perform cross-site scripting (XSS) attacks on the affected systems and run scripts in the security context of the current user. The official announcement did not described in details. So my earlier attention focus in TaintTracking Configuration. However it looks that it is incorrect. The best way to fix DOM based cross-site scripting is use the right output method (sink). From technical point of view, XSS occurs when attacker inject client side script into web pages. So in order to fix this vulnerability. it should do a sanitization of user-supplied data.
Remedy: The security update addresses Microsoft Outlook for Android parses specially crafted email messages. Please refer to following URL for details – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1460