Preface: Sometimes while designing a software, you might have a requirement to hold some data (for reprocessing at later stage) for some duration. Some software do it within the memory in which they are running while others may create a temporary file for this purpose.
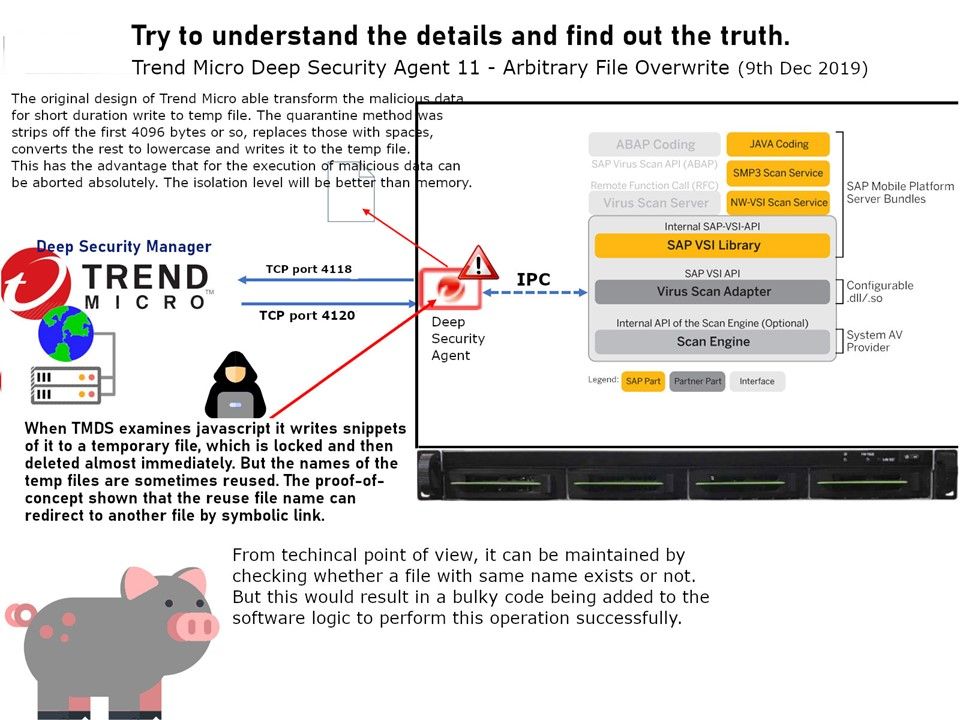
Technical background: The original design of Trend Micro able transform the malicious data for short duration write to temp file. The quarantine method was strips off the first 4096 bytes or so, replaces those with spaces, converts the rest to lowercase and writes it to the temp file. This has the advantage that for the execution of malicious data can be aborted absolutely. The isolation level will be better than memory. Vulnerability details: When TMDS examines javascript it writes snippets of it to a temporary file, which is locked and then deleted almost immediately. But the names of the temp files are sometimes reused. The proof-of-concept shown that the reuse file name can redirect to another file by symbolic link.
Official announcement, please refer to the link: https://success.trendmicro.com/solution/000149495