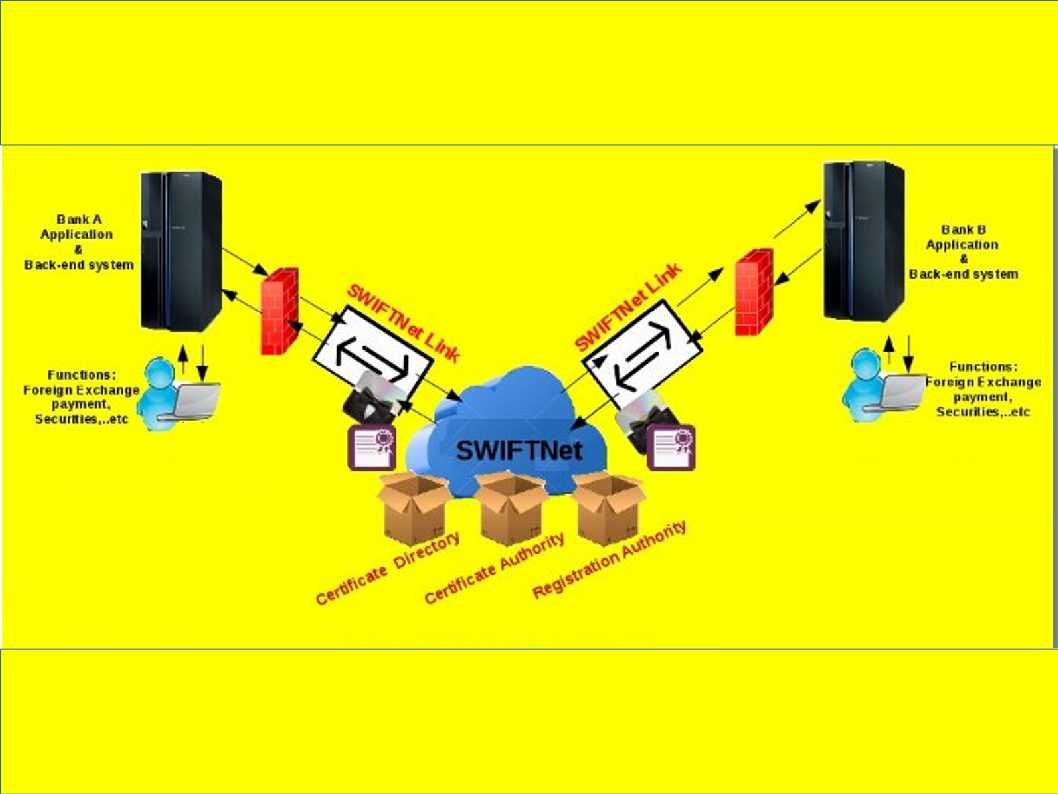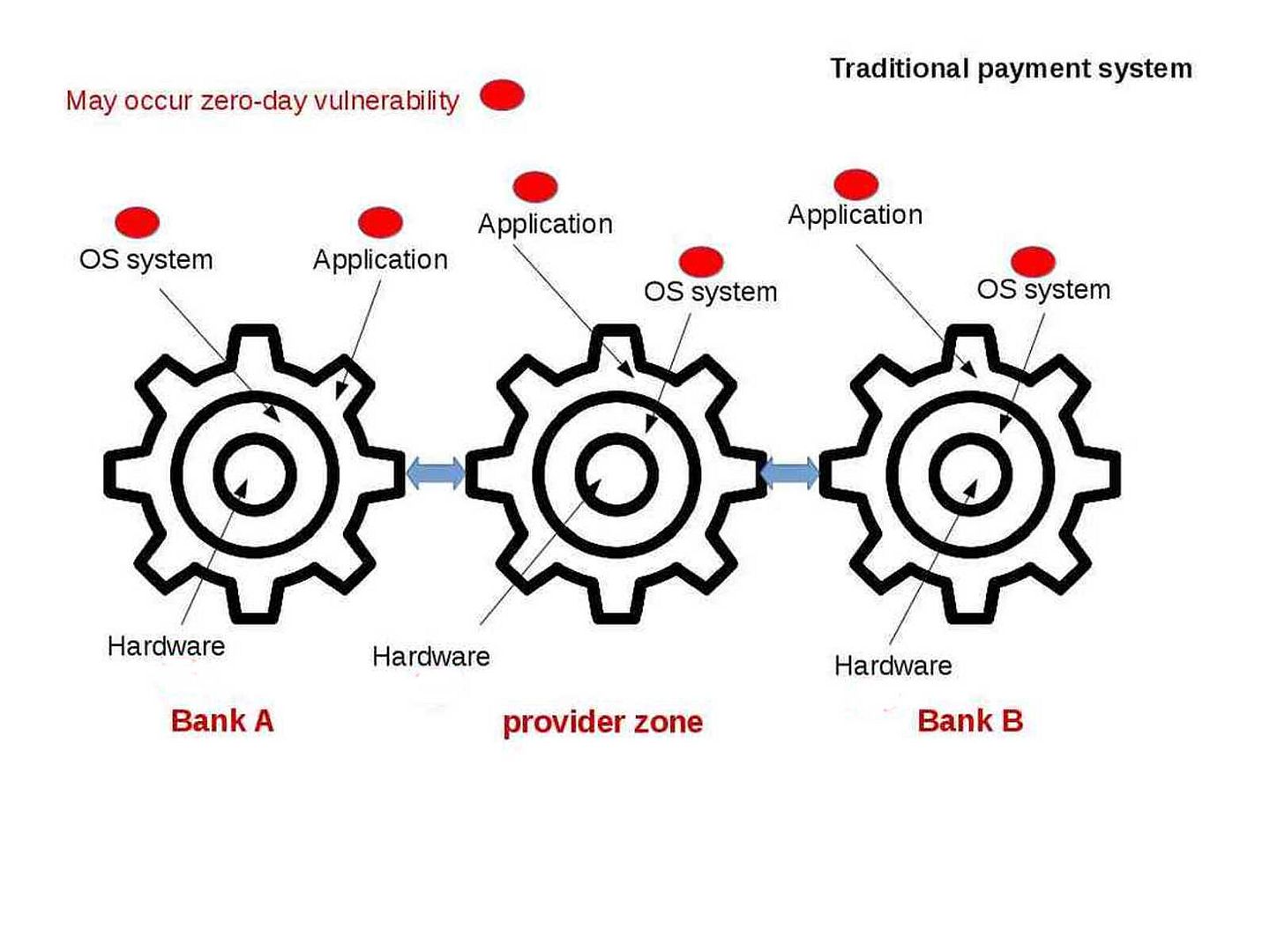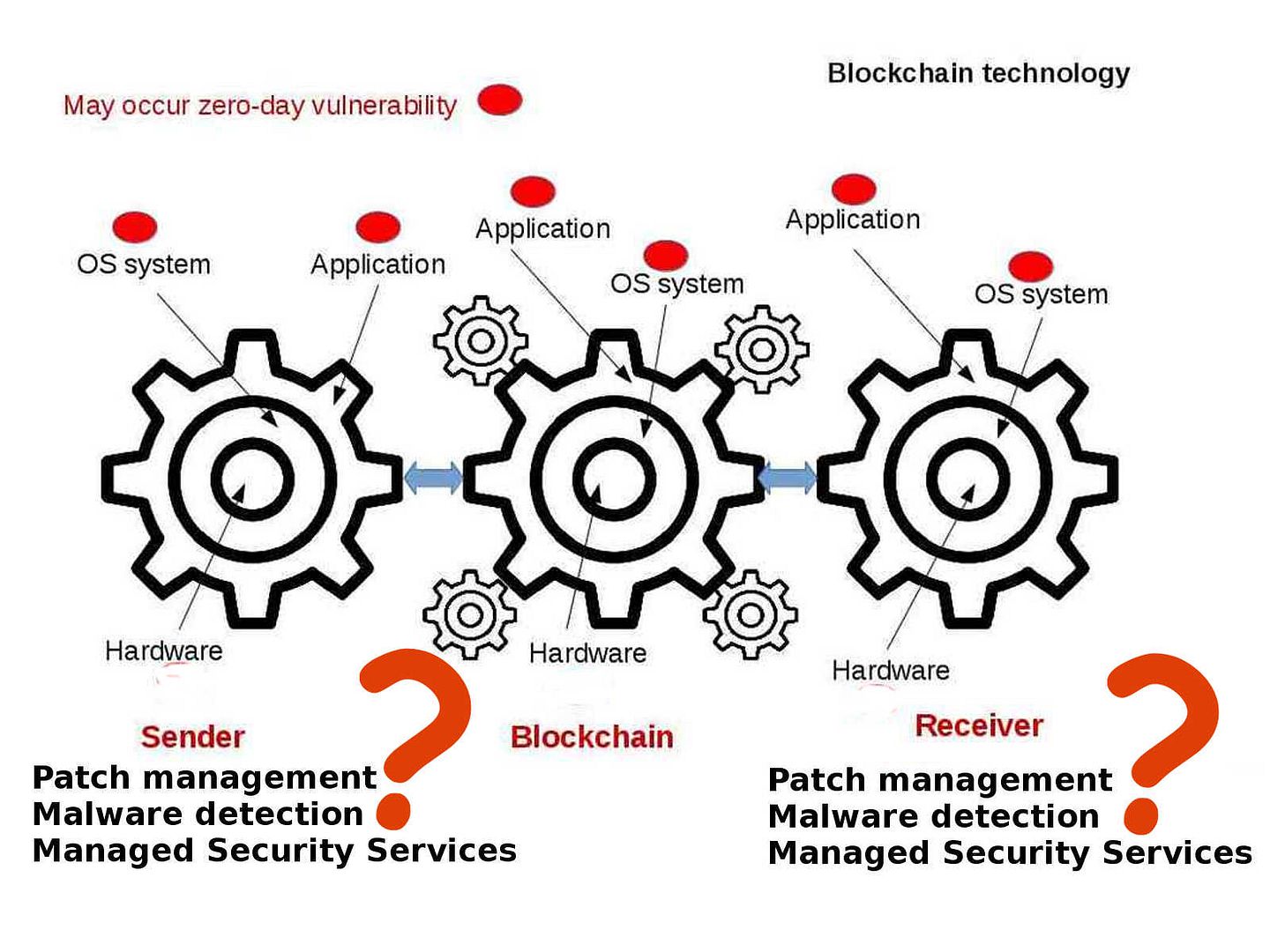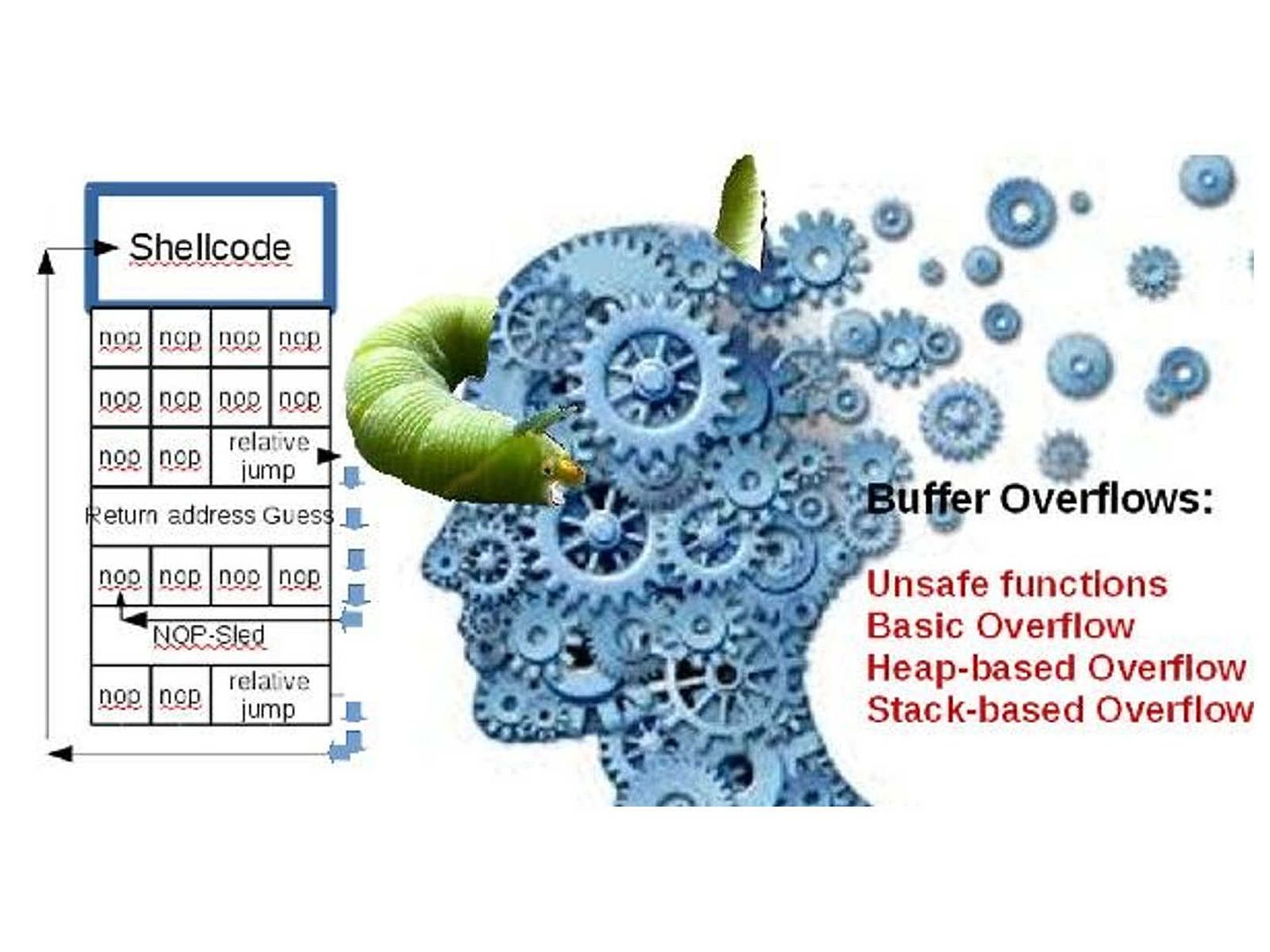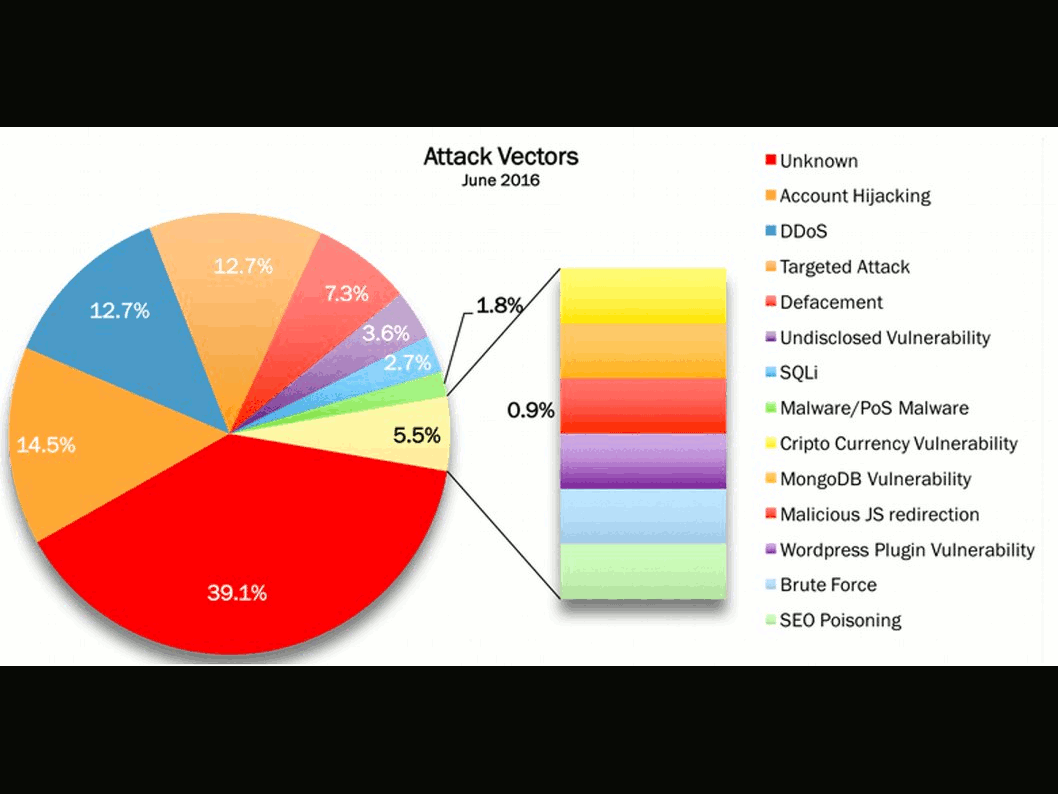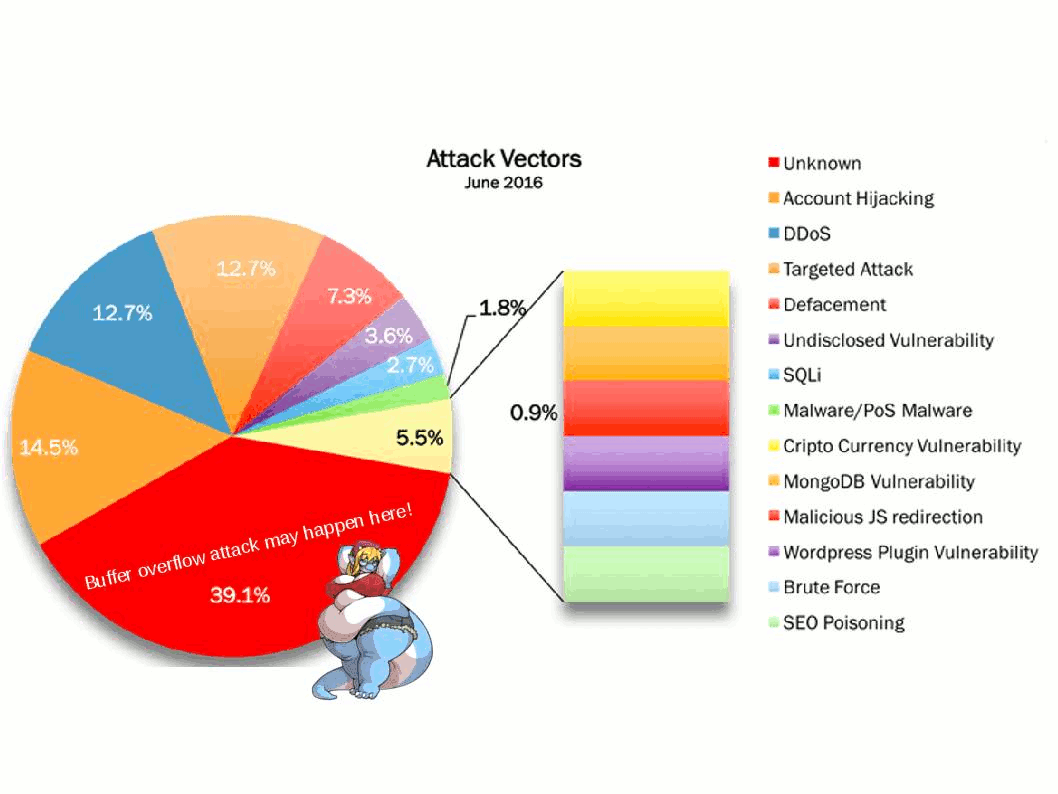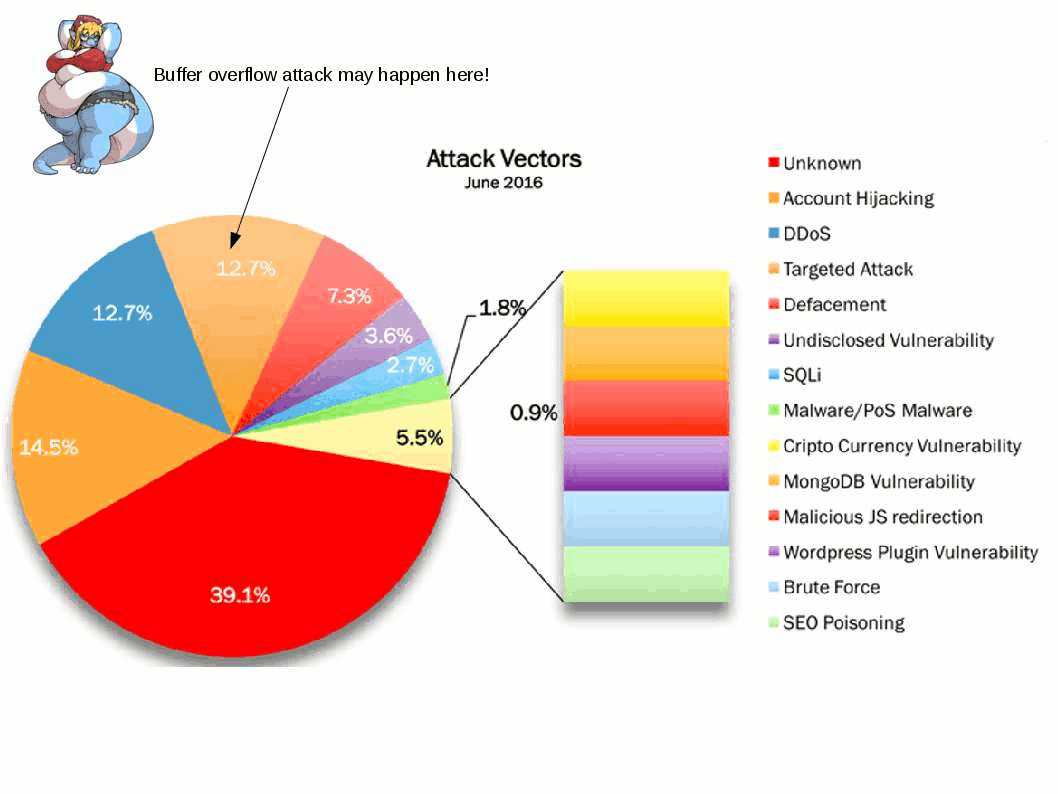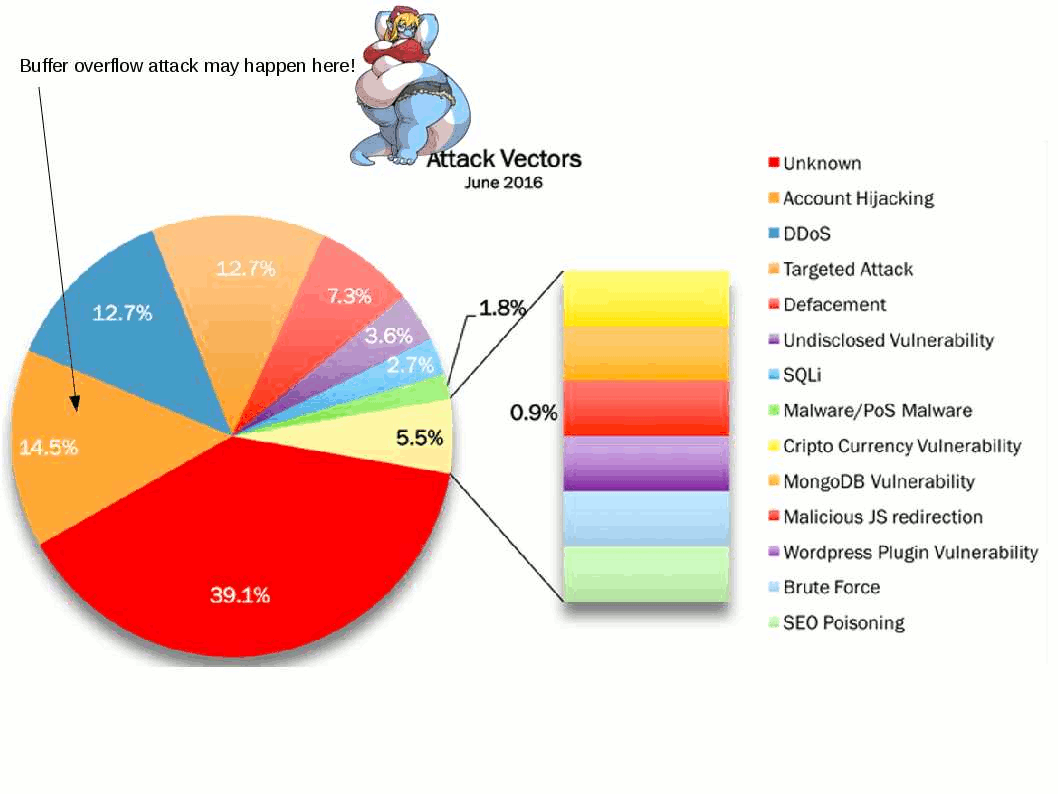
Stuxnet a famous malware to sabotage Iran’s nuclear program. From technical of view, malware change the shape of computers in the world convert to a cyber weapon. Who’s the team take responsibility? For sure that is not you and me.
Stunext attack scenario:
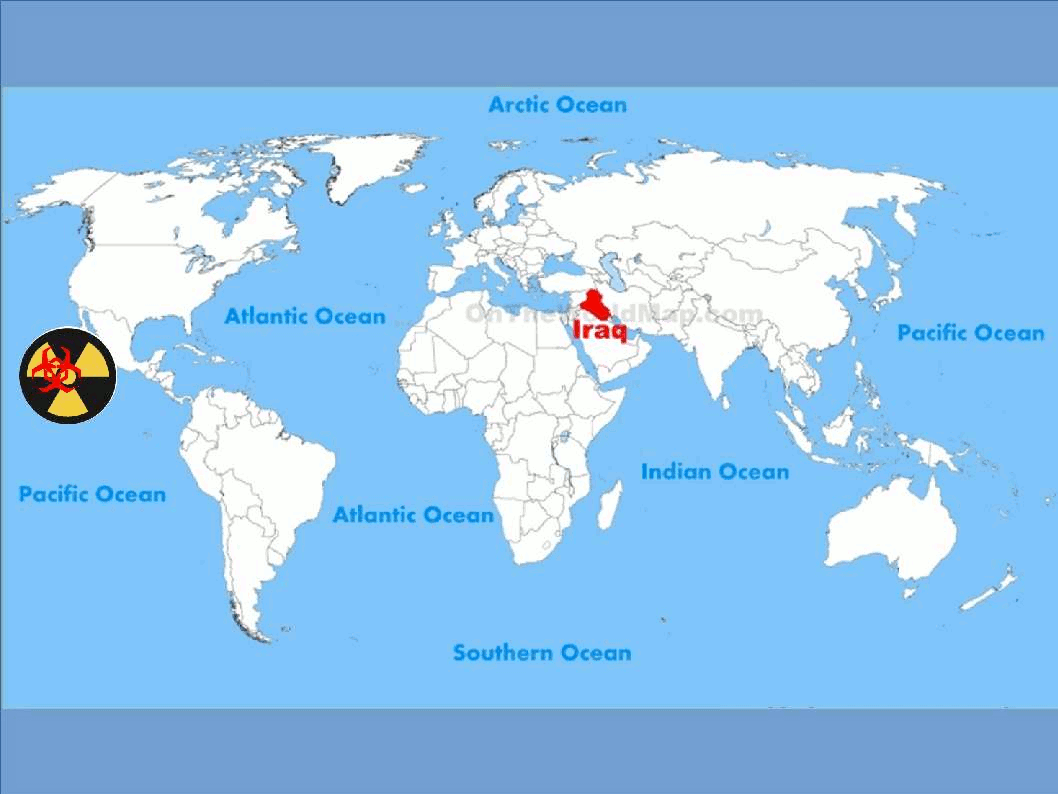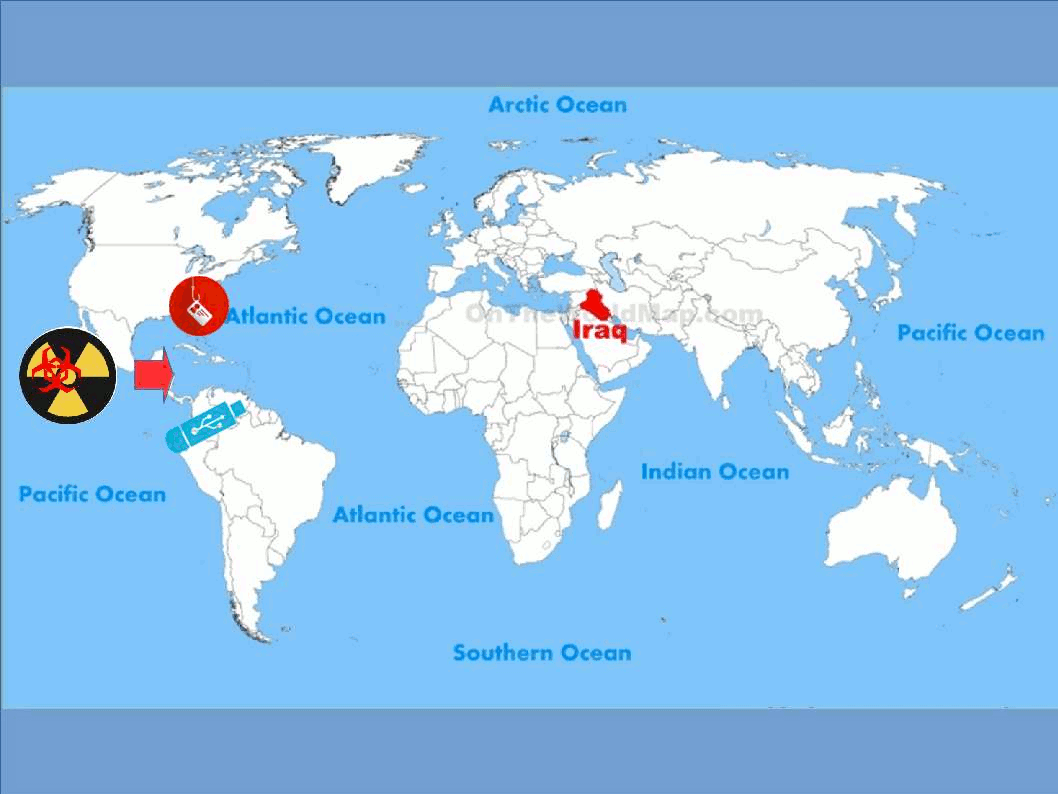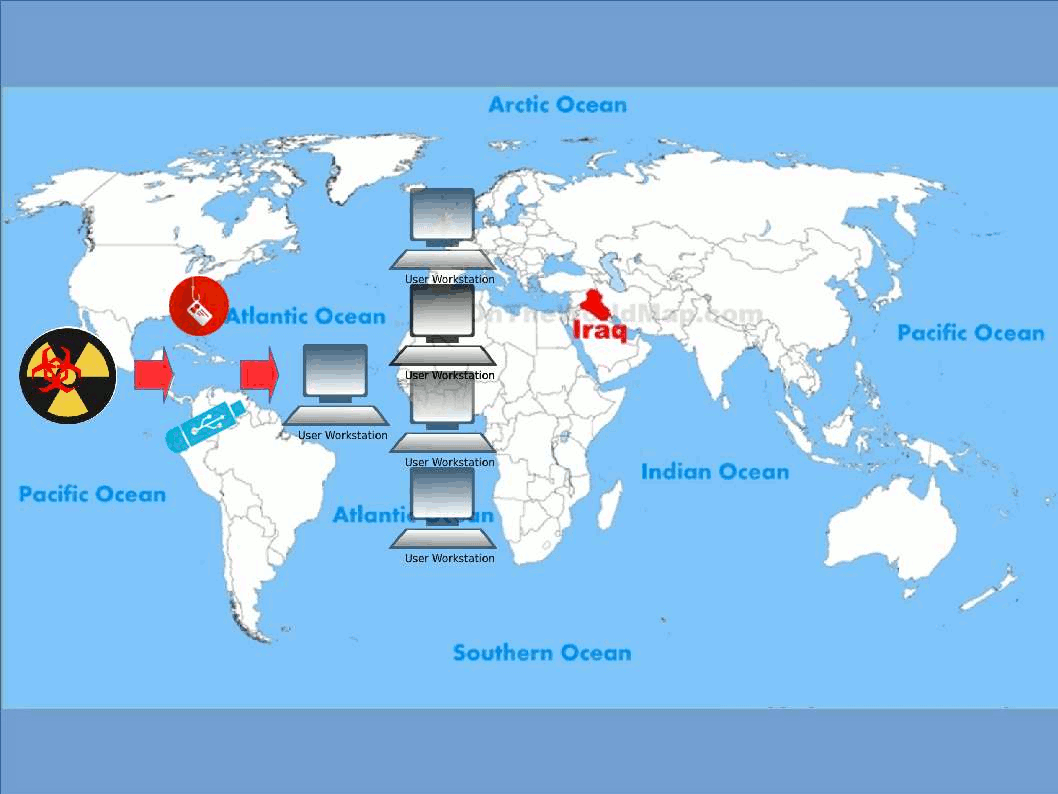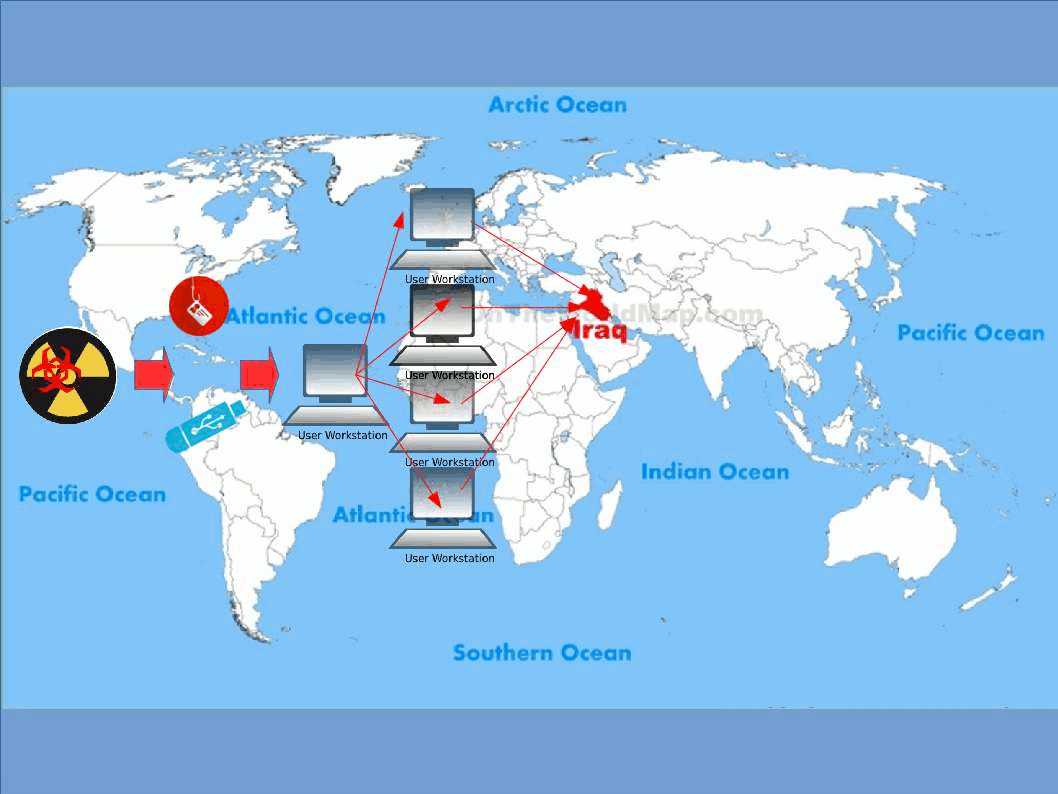
Heard that malware activities in South Korea run serious recently. Headline news were told the military defense of south Korea was hacked. Regarding to the articles the goal of such malware attack focus South Korean nuclear facility. We don’t have related information and not going to predict who is the attacker of this incident. But malware focus nuclear power facilities not only occurs today. Stuxnet, Duqu, and Flame are categories hardcore type malware. The hardcore type malware usually achieve the following actions.
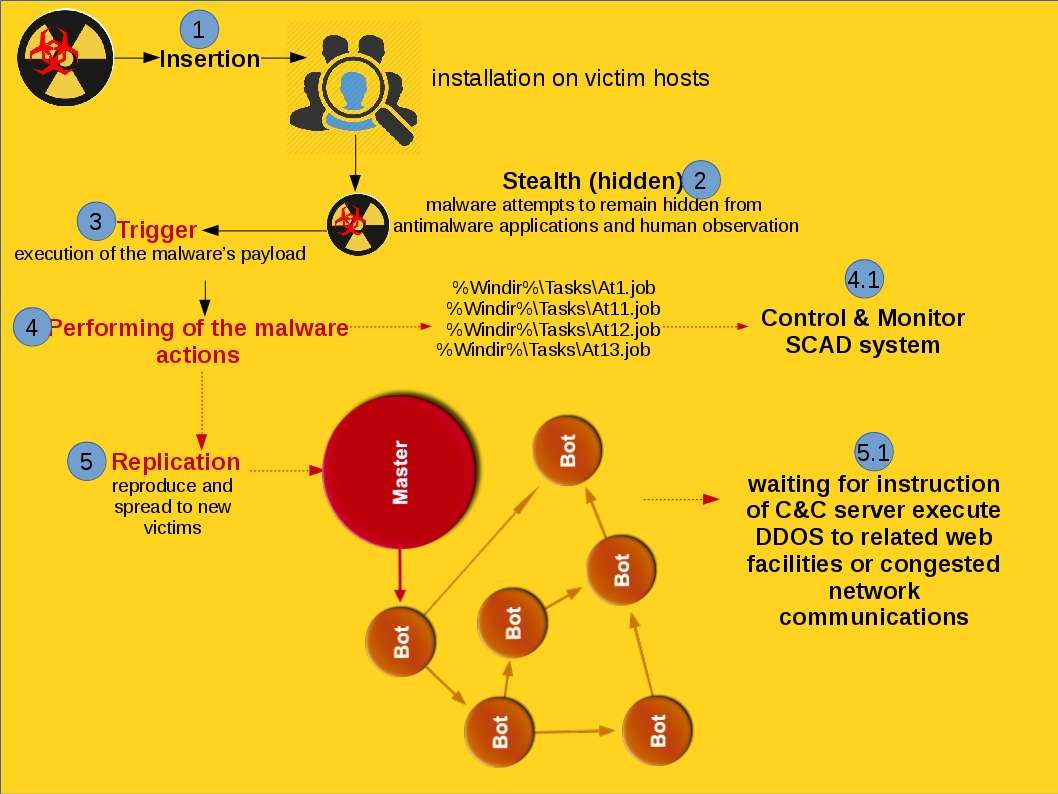
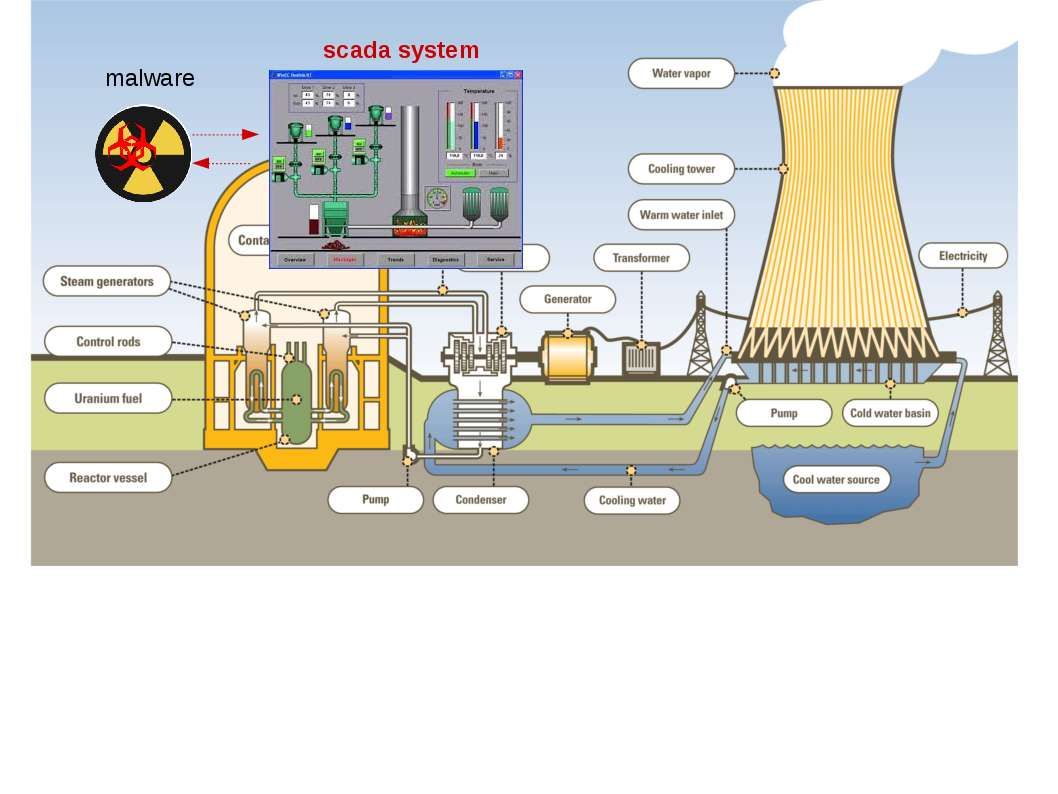
Do you think SCADA system is the culprit of attack on nuclear power system?
What is SCADA?
SCADA is an acronym for Supervisory Control And Data Acquisition, which is a computer system for gathering and analyzing real-time data.
Where is SCADA used?
SCADA systems are used to automate complex industrial processes where human control is impractical. The SCADA systems benefits to control and monitor processes. Thereby it used in large applications such as monitoring and controlling a nuclear power plant.
SCADA application:
WinCC (Siemens Simatic HMI WinCC v7.3 (x86/x64)) provides all the functionality of SCADA for Windows for all industries.
Historical incident record:
June 2010 – Stuxnet relies on MS zero day implant malware granted control and monitor functions in SCADA system.
Malware attack triggered by Microsoft Zero day (MS08-067, MS10-046 & MS10-061)
Malware relies on vulnerability (CVE-2010-2772) and execute privileges escalation on database of WinCC MSSQL server. As a result hacker allow to view information on SCADA system.
Oct 2011 – Duqu executables share injection code with the Stuxnet worm. The Duqu design was based on the same source code as Stuxnet. The similarity of features shown as below:
- Duqu use XOR based encryption for strings (key: 0xAE1979DD)
- Decrypted DLLs are directly injected into system processes instead of dropped to disk.
- Rootkit to hide its activities
May 2012 – Flame malware targeted cyber espionage in Middle Eastern countries.
The researchers say that Flame may be part of a parallel project created by contractors who were hired by the same nation-state team that was behind Stuxnet and its sister malware, DuQu.
The number and geographical location of Flame infections detected by Kaspersky Lab on customer machines.
- Iran = 189
- Israel Palestine = 98
- Sudan = 32
- Syria = 30
- Lebanon = 18
- Sudi Arabia = 10
- Egypt = 5
Apr 2016 – Virus:Win32/Ramnit.A, German nuclear plant infected with computer virus. As Reuters reports, viruses with names like “W32.Ramnit” and “Conficker” where found in a computer system that deals with data visualization.
The virusesWin32/Ramnit.A is a file infector with IRCBot functionality which infects .exe, and .HTML/HTM files, and opens a back door that compromises your computer.
- File MD5: 0x5CC31D49CAFC508238259616583332A2
- File SHA-1: 0xC775A22B4B150989F57AB129591F4DA328F52B7C
Aug 2016 – Virus:Win32/Ramnit.A (checksum changed)
- File MD5: 0x25C1DE8838ADBC0DCFF61E6B44458CF4
- File SHA-1: 0xDF6B04BA2103B2EB43B51EBDFB705A37BE5F28A9
1st Oct 2016 – Headline News: Rep. Kim Jin-pyo, a lawmaker of the main opposition Minjoo Party of Korea, told Yonhap News Agency in a telephone interview that the hacking targeted the “vaccine routing server” installed at the cyber command.
Interim summary:
SCADA systems are used to automate complex industrial processes where human control is impractical. The SCADA systems benefits to control and monitor processes. Thereby it used in large applications such as monitoring and controlling a nuclear power plant. WinCC (Siemens Simatic HMI WinCC v7.3 (x86/x64)) provides all the functionality of SCADA for Windows for all industries. Since zero-day vulnerability found each week especially Miscrosoft products. Do you think SCADA system is the culprit of attack on nuclear power system?
The project development of Nuclear power budget huge amount of money and covered with disaster recovery plan. Do you think current disaster recovery plan will cover up Zero day attack on SCADA system? What do you think?