Preface: Ransomware infection not merely boots by vulnerability of the windows OS and or products components. Web site programming technique is the accomplice. Perhaps we can say, how successful of ransomware attacks will depends on the total number of compromised web server. What I call the trigger point.
Background: Ransomware is often spread through phishing emails that contain malicious attachments or through drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website and then malware is downloaded and installed without the user’s knowledge.
Ransomware is a type of malware attack. The encryption process will performs a key exchange with the Command and Control Server, using the encryption key to scramble all files discovered during the Execution step. It also locks access to the data. For cyber criminals view point, it is not possible to rent a web hosting service. Therefore, the possible way is find the online web portal which contained vulnerability. If they can compromised the online web. They can setup the phishing attack and evade traditional domain black list filter. So they can do their job silently.
Traditional corrective control not address the problem in effective way: A corrective control is an aftermath of detective and preventive. You can only restore from a backup after an incident. According to historical of attack, ransomware will be exploit operation system and or component vulnerability to conducting the infection. So traditional full backup may not use here because victim will be concerning what is exact time they receiving the attack. As a matter of fact, the correct way to proceed the restore procedure is wait for the digital forensic investigation result. Till today such attack still bother the whole world.
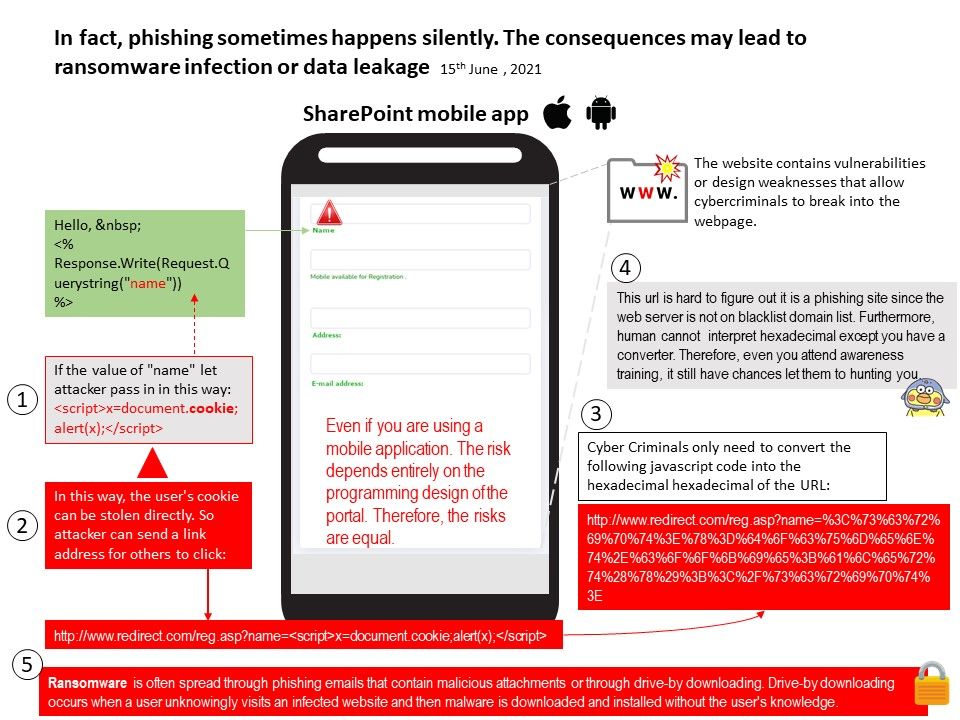
Maybe when something happens, the term phishing is on your side. See if you can learn more with the attached diagram.