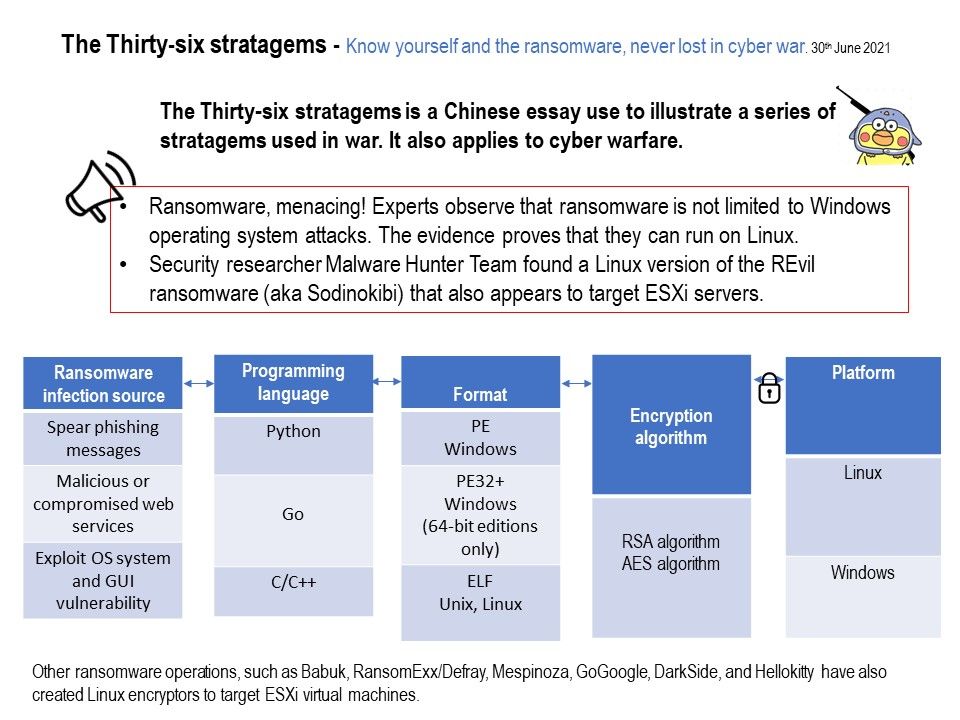
Preface: The Thirty-six stratagems is a Chinese essay use to illustrate a series of stratagems used in war. It also applies to cyber warfare.
Background: Kernel-based Virtual Machine (KVM) is an open source virtualization technology built into Linux®. Specifically, KVM lets you turn Linux into a hypervisor that allows a host machine to run multiple, isolated virtual environments called guests or virtual machines (VMs).
KVM is part of Linux. VMware relied on Linux during its early history. The early version of its hypervisor, called ESX, included a Linux kernel
(the central part of an OS that manages the computer hardware). When VMware released ESXi, it replaced the Linux kernel with its own.
Security Focus: Security researcher MalwareHunterTeam found a Linux version of the REvil ransomware (aka Sodinokibi) that also appears to target ESXi servers.
Ransomware, menacing! Experts observe that ransomware is not limited to Windows operating system attacks. The evidence proves that they can run on Linux. Other ransomware operations, such as Babuk, RansomExx/Defray, Mespinoza, GoGoogle, DarkSide, and Hellokitty
have also created Linux encryptors to target ESXi virtual machines.
Reference:
- HelloKitty targeted a UK Healthcare organisation
- DarkSide target multiple large, high-revenue organizations resulting in the encryption and theft of sensitive data and threats to make it publicly available if the ransom demand is not paid.
- GoGoogle is a malicious program designed to encrypt data and demand ransom payments for decryption. During the encryption process, all affected files are renamed according to this pattern: original filename, unique ID, cyber criminals’ email address and the “.google” extension.
- Mespinoza TheMespinozaransomware was first used in October 2018 at least. The first versions produced encrypted filescarrying the «.locked» extension, common to many ransomwares. Since December 2019, a new version ofMespinozais documented in open sources. This version is often calledPysabecause it produces encrypted fileswith the «.pysa» extension.
Staying alert!