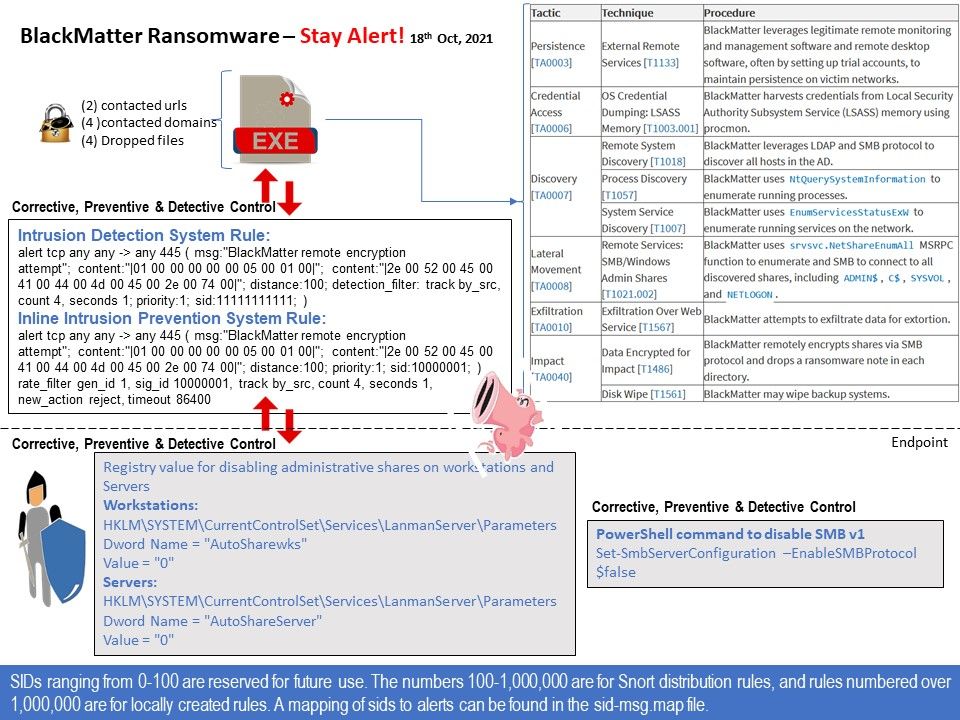
Preface: Ransomware common deploying malicious actions is the automatically propagation. Their target will be included ADMIN$, C$, SYSVOL, and NETLOGON default setup.
Common infection technique: Believe it or not, quite a lot of ransomware developers will use simple technique.
Deploy encryptors across the environment using Windows batch files (mount C$ shares, copy the encryptor, and executed it with PsExec tool).
Please refer to the official website for details – https://us-cert.cisa.gov/ncas/alerts/aa21-291a
Strengthen your prevention, detection and corrective control: If PsExec is utilized in an environment, disabling the admin (ADMIN$) share can restrict the capability for this tool to be utilized to remotely interface with endpoints. In addition, you should perform system hardening. For example. Modify the registry value to disable administrative sharing on workstations and servers.
Perhaps BlackMatter ransomware not use this technique. But this is a baseline protection. According to the suggestion by US-cert. Define new rules in your IDS is the effective way to mitigate the risk. Please refer to attached diagram for details.
Since it is hard to avoid design limitation. For example: Disabling PowerShell Remoting does not prevent local users from creating PowerShell sessions on the local computer or for sessions destined for remote computers. As a result, it provides a way for attackers.
Long time ago, SIEM vendor (Splunk) recommend using sysmon to detect ransomware attack. I agree that this is the effective solution. The concept is shown as below:
System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time. By collecting the events it generates using Windows Event Collection or SIEM agents and subsequently analyzing them, you can identify malicious or anomalous activity and understand how intruders and malware operate on your network.