Preface: Modern Cyber Defense solution without difficulties detect malicious activities. For instance, applications need approved permissions before installation; and security software can scan files to be written, read, and/or executed to check for known signatures. But we still heard data breach incident occurred. Why?
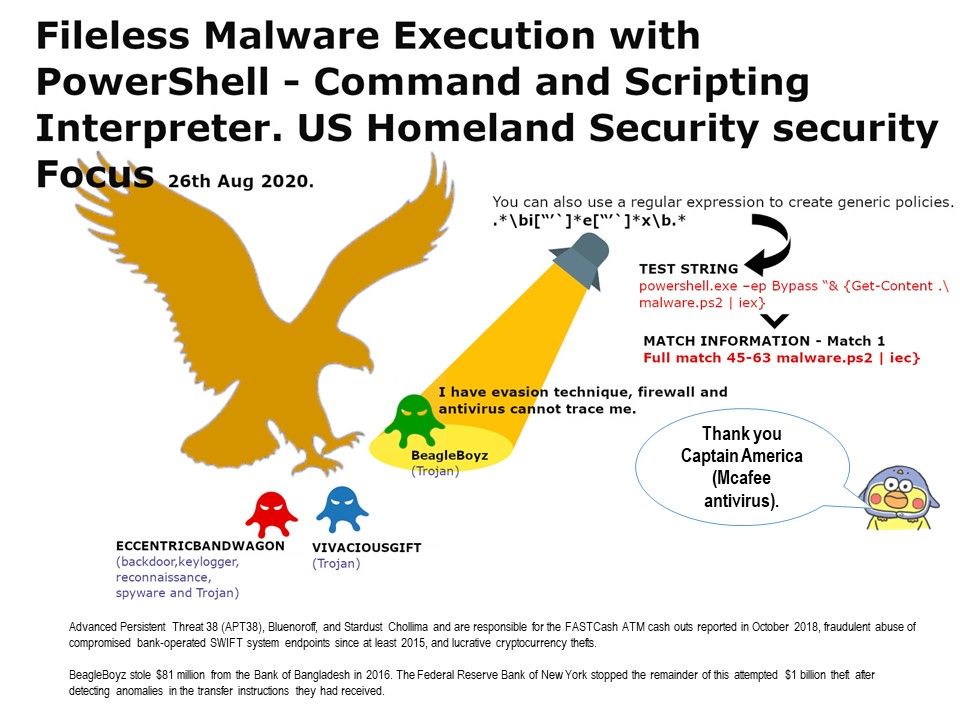
Detail description: On 26th Aug, 2020, US Homeland security published articles to urge public that at least three different types of malware on the way to approaching banking finance, business and computer end user. By this chance, we are going to focus a malware named “BeagleBoyhz”. The BeagleBoyz use a variety of techniques to run their code on local and remote victim systems. Quite a lot of cyber security services vendor observe that Fileless Malware Execution with PowerShell Is Easier to evade antivirus and firewall. In order to avoid their activities detected by defense mechanism. Attacker will abuse Command and Scripting Interpreter technique to executing arbitrary commands.Meanwhile, this is the security focus highlighted by the Department of Homeland Security. As a large number of articles describe different types of malware. If you want to read the details, please refer to the website link.
https://us-cert.cisa.gov/ncas/alerts/aa20-239a
https://us-cert.cisa.gov/northkorea
Remedy: If your current cyber defense solution capable to support regular expression filter function. You can create generic policies to deny the unknown PowerShell script. For example:
.\bi[“’]*e[“’]x\b.*
blocks Invoke-Expression.
At the end, I would like to thanks for McAfee providing this effective solution.