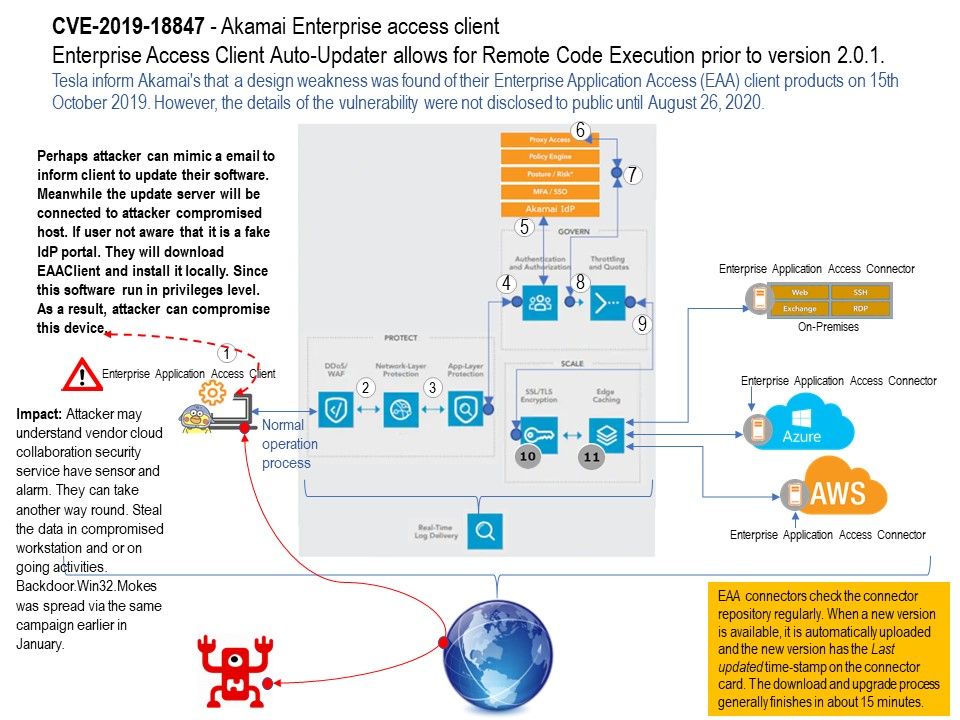
Preface: On October 15, 2019, Tesla discovered, and responsibly disclosed, a vulnerability within Akamai’s Enterprise Application Access (EAA) client that allows privilege escalation and remote code execution (RCE) when an attacker is within privileged locations on a network.
Vulnerability details: Enterprise Access Client Auto-Updater allows for Remote Code Execution prior to version 2.0.1.
Possible ways: Perhaps attacker can mimic a email to inform client to update their software. Meanwhile the update server will be connected to attacker compromised host. If user not aware that it is a fake IdP portal. They will download EAAClient and install it locally. Since this software run in privileges level. As a result, attacker can compromise this device.
Impact: Attacker may understand vendor cloud collaboration security service have sensor and alarm. They can take another way round. Steal the data in compromised workstation and or on going activities.
Backdoor[.]Win32[.]Mokes was spread via the same campaign earlier in January.
Official announcement: August 25, 2020 9:45 AM – https://blogs.akamai.com/2020/08/enterprise-application-access-client-eaa-vulnerability-cve-2019-18847.html