Preface: Different HPC compilers allow the coder to make use of these tools for better performance and capability. For example, using HPC compilers allow for easier coding to run a parallel job. Compilation is the process of converting C language source code into executable program code. Running is the process of executing executable code. Compilation only needs to be completed once to produce executable code. The resulting executable code can be run multiple times.
Background: XML parser for C++ determines whether an XML document is well-formed and optionally validates it against a DTD. A DTD is a Document Type Definition. A DTD defines the structure and the legal elements and attributes of an XML document. The parser constructs an object tree that can be accessed through a DOM interface or operates serially through a SAX interface. SAX defines an abstract programmatic interface that models the XML information set (infoset) through a linear sequence of familiar method calls.
Validating an XML document determines whether the structure and content of the document conform to a set of rules. Xerces-C++ is a validating XML parser written in a portable subset of C++.
Remark: SAX-type parsing performance of Fast Infoset is also much faster than parsing performance of XML 1.0.
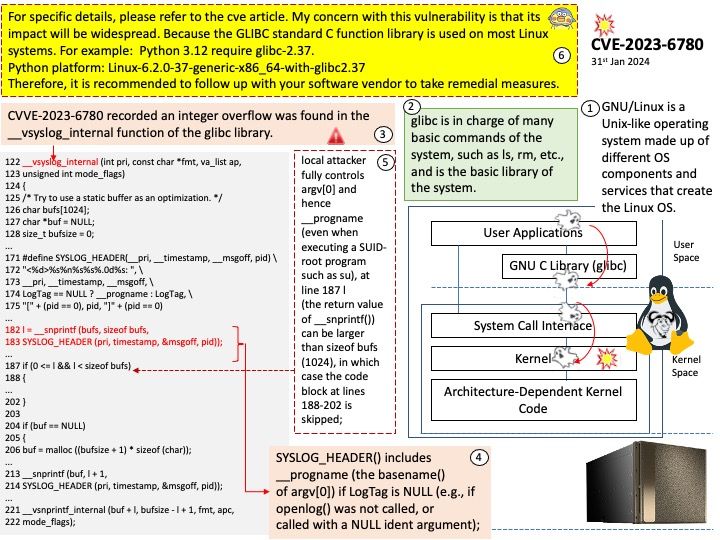
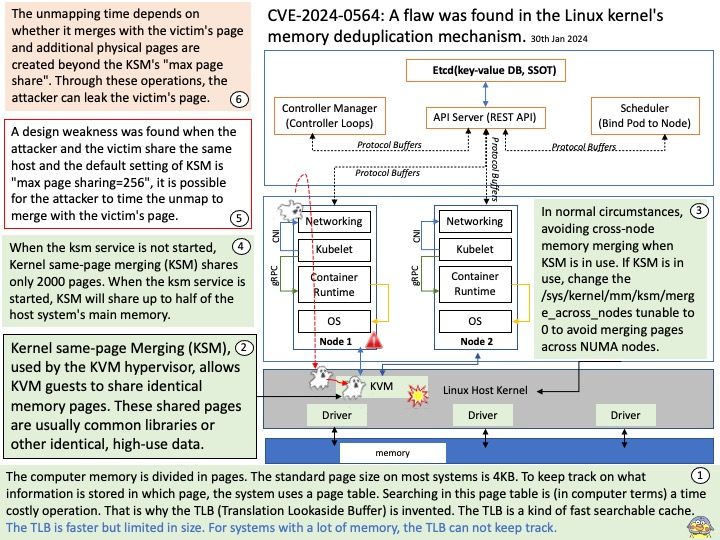
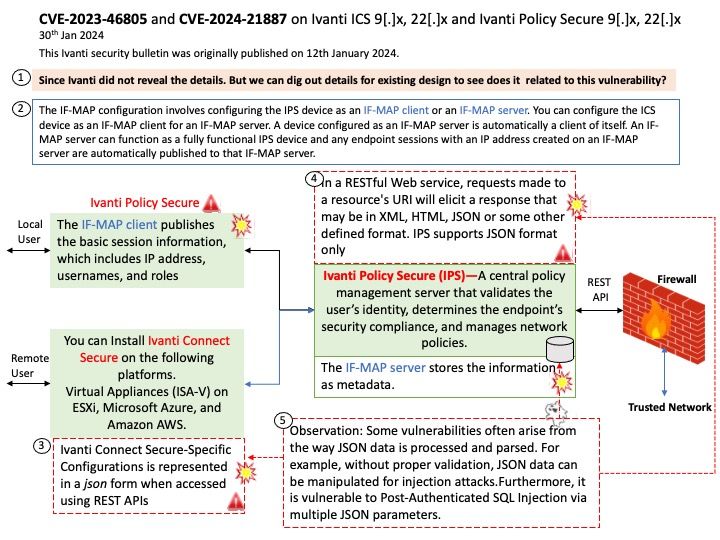
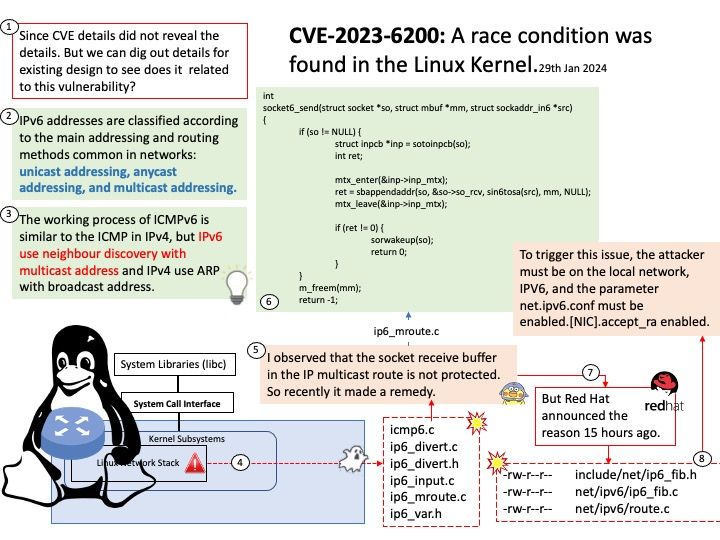
Vulnerability details: A use-after-free vulnerability was found in xerces-c in the way an XML document is processed via the SAX API. Applications that process XML documents with an external Document Type Definition (DTD) may be vulnerable to this flaw. A remote attacker could exploit this flaw by creating a specially crafted XML file that would crash the application or potentially lead to arbitrary code execution.
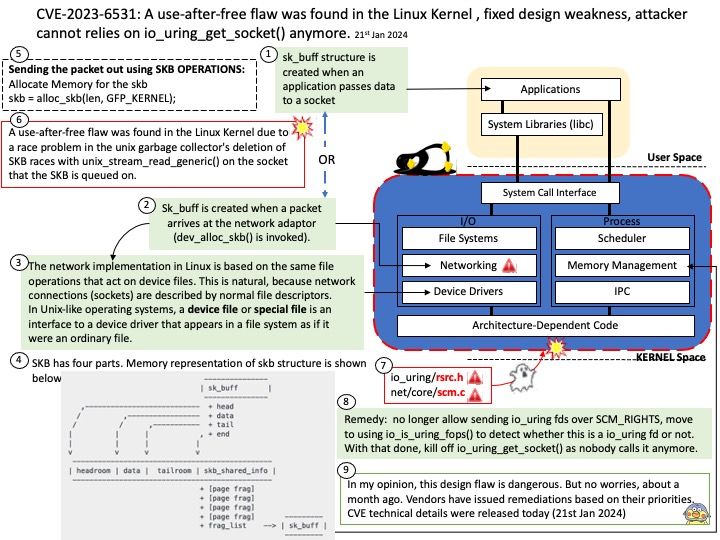
Ref: To understand the twists and turns of this story, please refer to the pictures attached to this article.
Official details: Please refer to the link for details – https://www.suse.com/support/update/announcement/2024/suse-su-20240299-1/