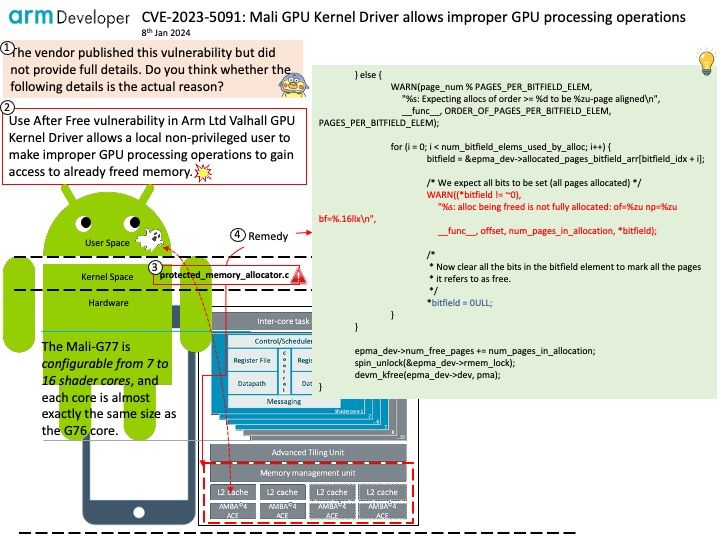
This Qualcomm security bulletin was originally published on 1st January 2024.
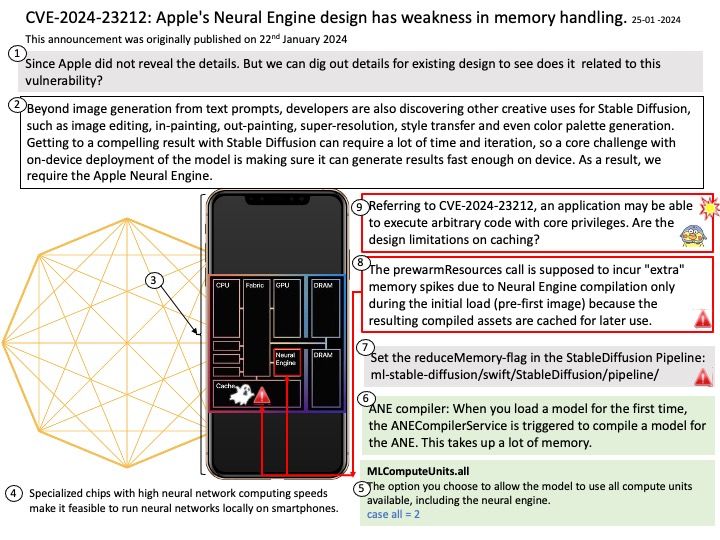
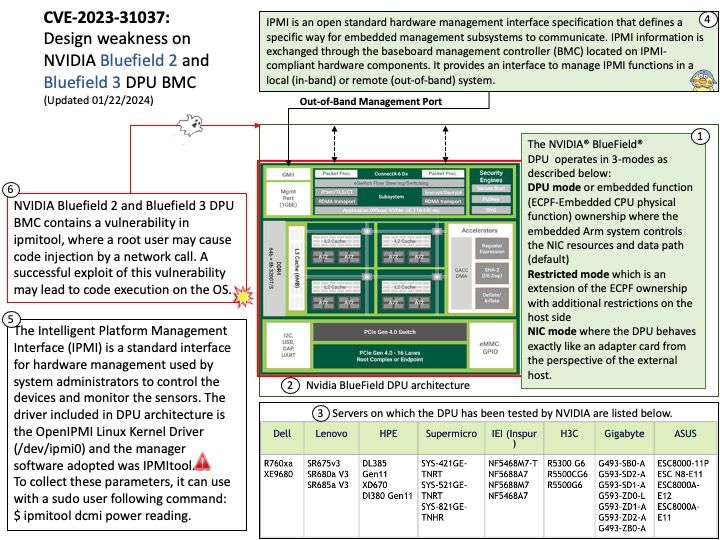
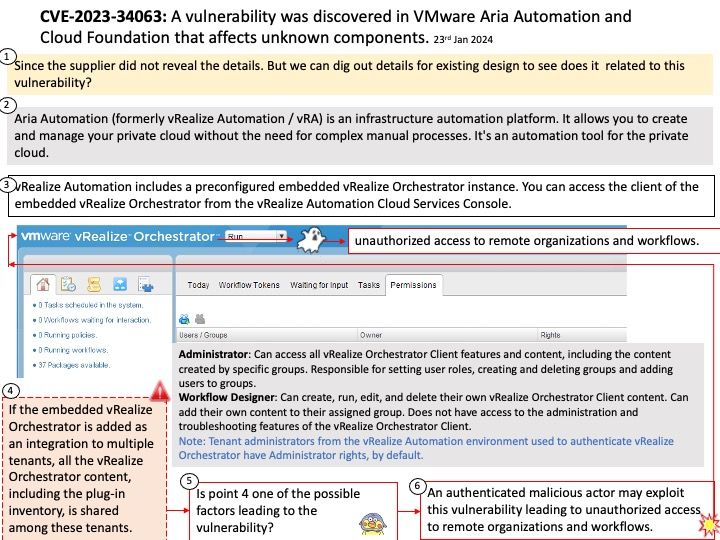
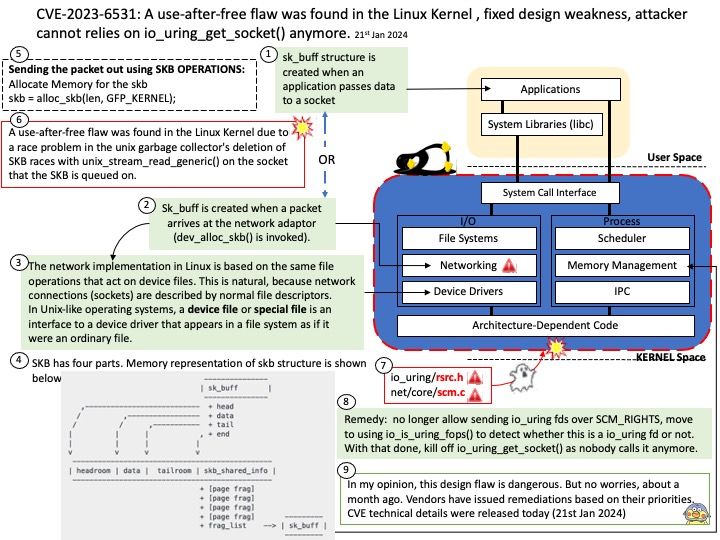
Preface: One method of conducting these PDoS attacks is commonly referred to as phlashing. During such an attack, an attacker bricks a device or destroys firmware, rendering the device or an entire system useless. This is one method to exploit vulnerabilities and replace a device’s basic software with a corrupt firmware image.
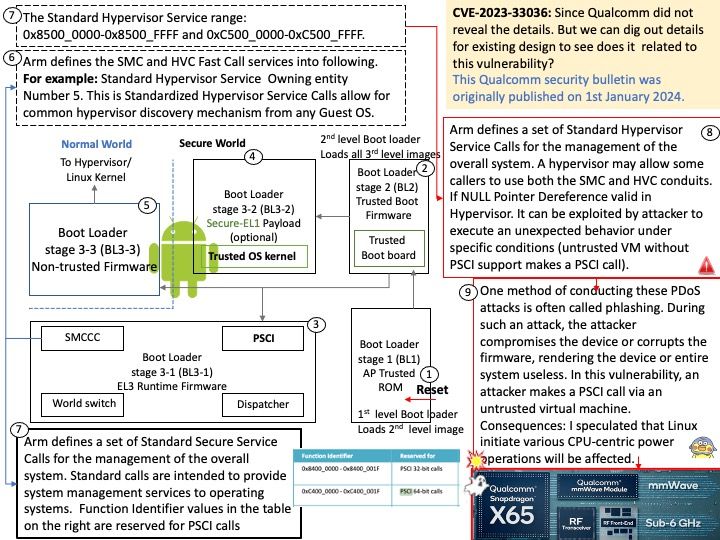
Background: The ARM Trusted Firmware implements a subset of the Trusted Board Boot Requirements (TBBR) Platform Design Document (PDD) for ARM reference platforms. The TBB sequence starts when the platform is powered on and runs up to the stage where it hands-off control to firmware running in the normal world in DRAM. This is the cold boot path.
The ARM Trusted Firmware also implements the Power State Coordination Interface (PSCI) PDD as a runtime service. PSCI is the interface from normal world software to firmware implementing power management use-cases (for example, secondary CPU boot, hotplug and idle). Normal world software can access ARM Trusted Firmware runtime services via the ARM SMC (Secure Monitor Call) instruction.
Vulnerability details: Permanent DOS in Hypervisor while untrusted VM without PSCI support makes a PSCI call.
Vulnerability Type : CWE-476 NULL Pointer Dereference
My observation: I speculated that Linux initiate various CPU-centric power operations will be affected.
Official announcement: Please refer to the link for details – https://docs.qualcomm.com/product/publicresources/securitybulletin/january-2024-bulletin.html