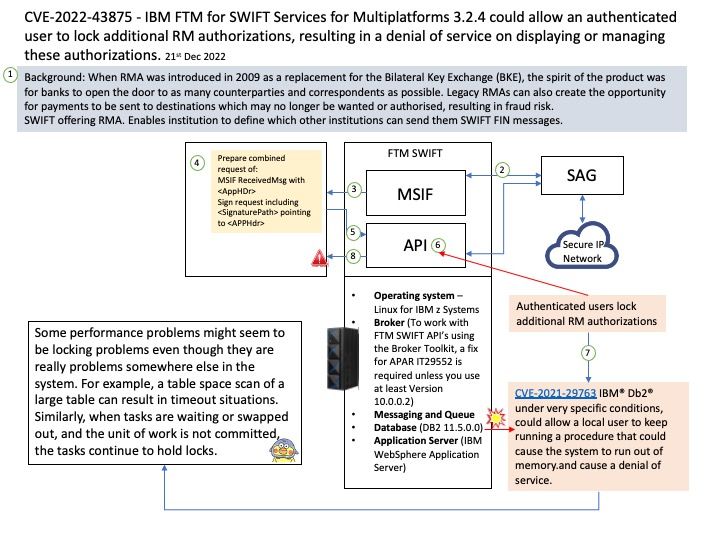
Preface: The Global Positioning System (GPS) employs trilateration to calculate the coordinates of positions at or near the Earth’s surface. Trilateration refers to the trigonometric law by which the interior angles of a triangle can be determined if the lengths of all three triangle sides are known.
I have a set of coordinates, that I receive from GPS. Query to calculate the travelled distance:
ST_length(ST_Transform(st_makeline(points), 26986)) AS distance_travelled
Background: GPSD is a service daemon that monitors one or more GPSes or AIS receivers attached to a host computer through serial or USB ports, making all data on the location/course/velocity of the sensors available to be queried on TCP port 2947 of the host computer.
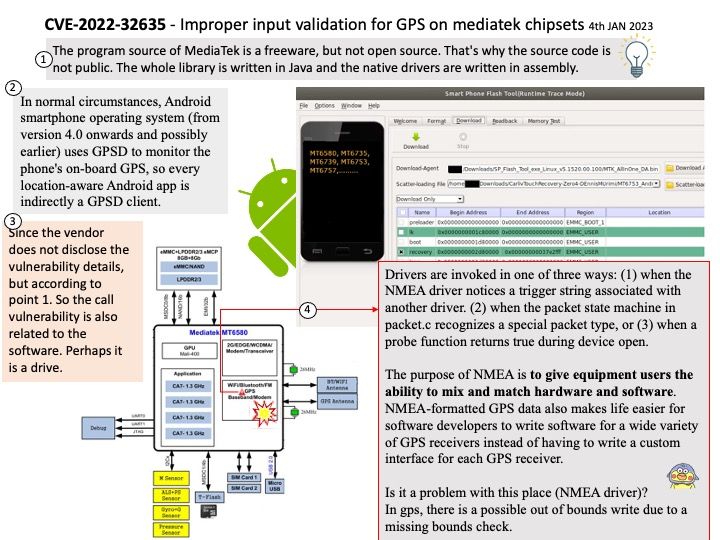
In normal circumstances, Android smartphone operating system (from version 4.0 onwards and possibly earlier) uses GPSD to monitor the phone’s on-board GPS, so every location-aware Android app is indirectly a GPSD client.
MediaTek, along with Qualcomm, is one of the most important third-party chipmakers in the Android smartphone ecosystem.
The program source of MediaTek is a freeware, but not open source. That’s why the source code is not public. The whole library is written in Java and the native drivers are written in assembly.
Vulnerability details: In GPS, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Affected Chipsets: MT6580, MT6735, MT6739, MT6753, MT6757, MT6761, MT6762, MT6763, MT6765, MT6768, MT6769, MT6771, MT6779, MT6781, MT6785, MT6789, MT6833, MT6853, MT6853T, MT6855, MT6873, MT6875, MT6877, MT6879, MT6891, MT6893, MT6895, MT6983, MT8167, MT8168, MT8173, MT8185, MT8321, MT8362A, MT8365, MT8385, MT8666, MT8667, MT8675, MT8765, MT8766, MT8768, MT8786, MT8788, MT8789, MT8791, MT8791T, MT8797
Affected Software Versions: Android 10.0, 11.0, 12.0, 13.0
Official announcement: For details, see the link –
Mediatek – https://corp.mediatek.com/product-security-bulletin/January-2023
Android – https://source.android.com/docs/security/bulletin/2023-01-01