Background: What is Apache Airflow used for?
Apache Airflow is an open-source tool to programmatically author, schedule, and monitor workflows. It is one of the most robust platforms used by Data Engineers for orchestrating workflows or pipelines. You can easily visualize your data pipelines’ dependencies, progress, logs, code, trigger tasks, and success status.
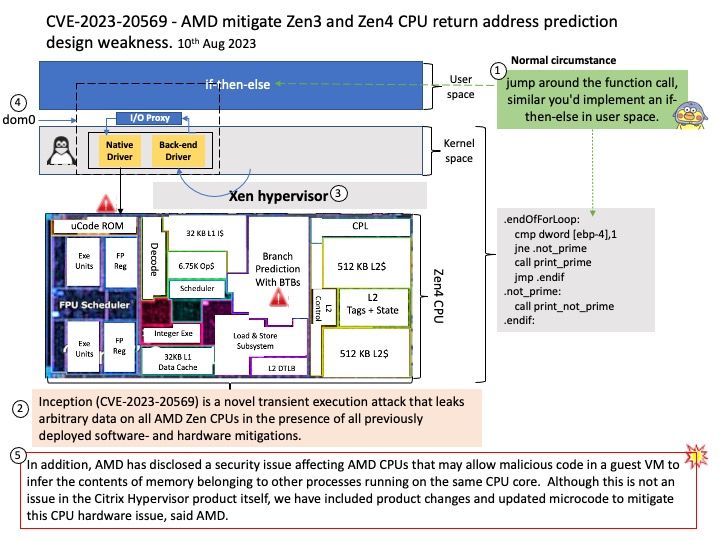
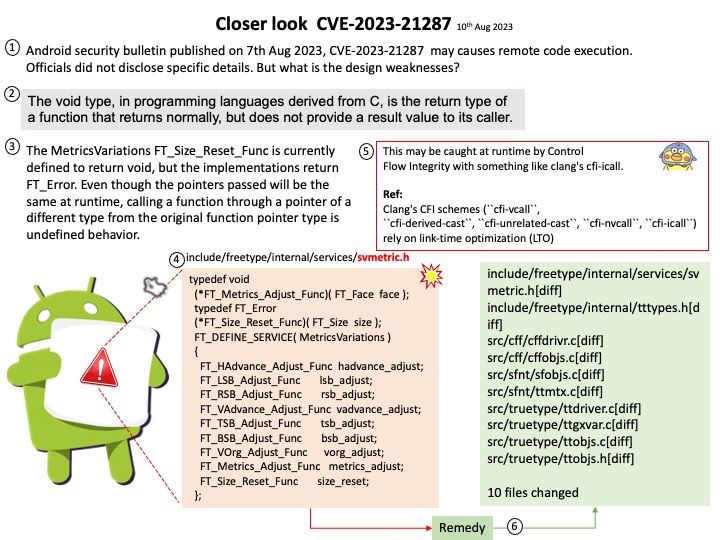
What is the difference between extras and providers in Airflow?
Extras are standard Python setuptools feature that allows to add additional set of dependencies as optional features to “core” Apache Airflow. One of the type of such optional features are providers packages, but not all optional features of Apache Airflow have corresponding providers.
Providers can contain operators, hooks, sensor, and transfer operators to communicate with a multitude of external systems, but they can also extend Airflow core with new capabilities. You can install those provider packages separately in order to interface with a given service.
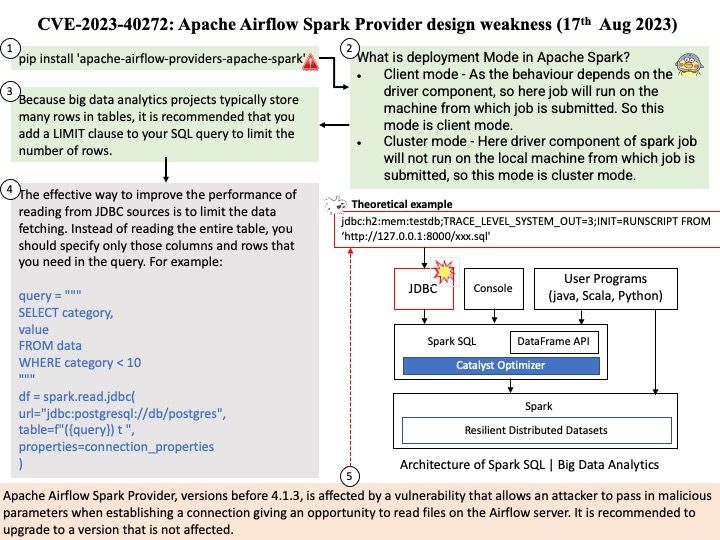
What is deployment Mode in Apache Spark?
- Client mode – As the behavior depends on the driver component, so here job will run on the machine from which job is submitted. So this mode is client mode.
- Cluster mode – Here driver component of spark job will not run on the local machine from which job is submitted, so this mode is cluster mode.
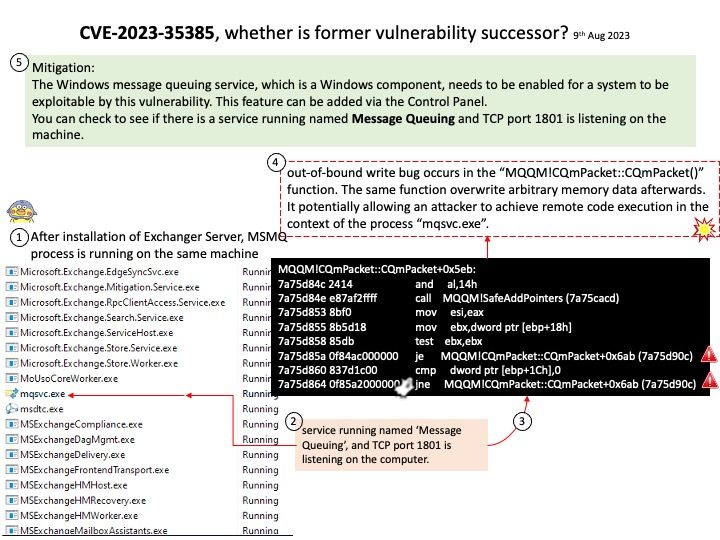
Vulnerability Details: Apache Airflow Spark Provider, versions before 4.1.3, is affected by a vulnerability that allows an attacker to pass in malicious parameters when establishing a connection giving an opportunity to read files on the Airflow server. It is recommended to upgrade to a version that is not affected.
Affected versions: Apache Airflow Spark Provider before 4.1.3
Remedy: Patched versions 4.1.3
Official announcement: For details, please refer to link – https://nvd.nist.gov/vuln/detail/CVE-2023-40272