Preface: According on 2020 market statistic, FireFox market share only 9.25%. But Chrome has 68.11% coverage. However I like FireFox.
How Firefox’s memory allocator works?
Firefox uses a memory allocator called moz jemalloc. There are two properties which focus by cyber security expert so far!
[PSJ] – In essence, a chunk is broken into several runs.
– Each run holds regions of a specific size. [TSOF]
– The feature of jemalloc is that it operates in a last-in-first-out (LIFO) manner, a free followed by a garbage collection and a subsequent allocation request for the same size, most likely ends up in the freed region.
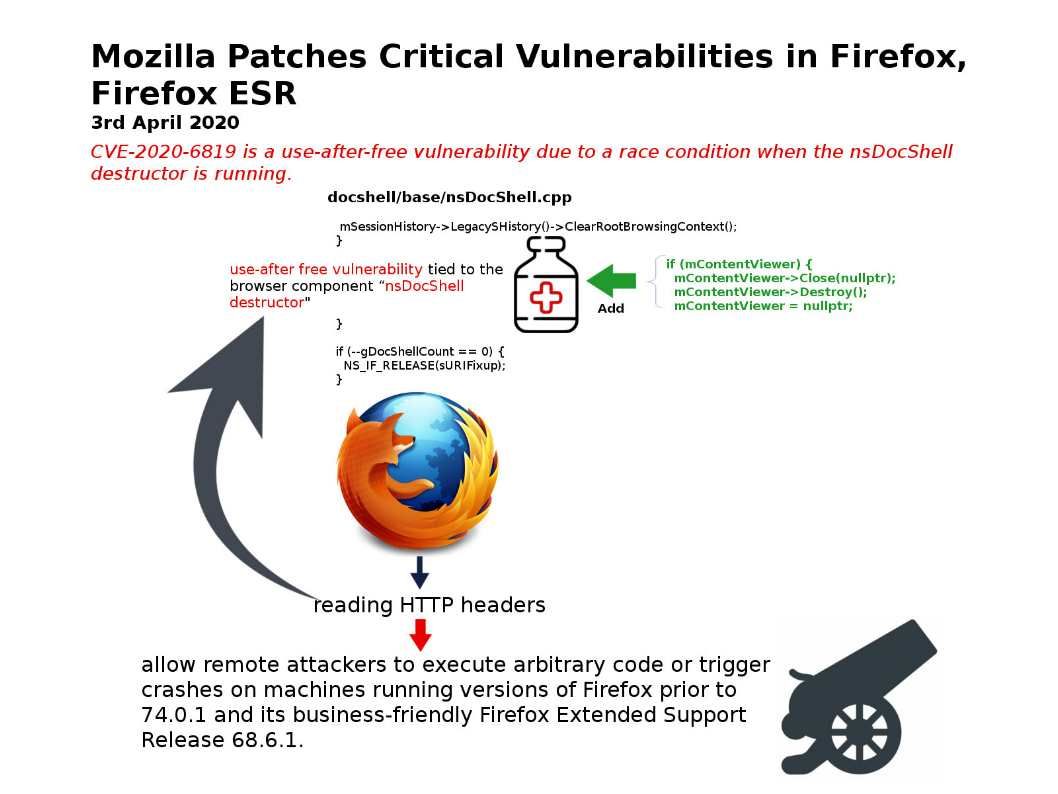
Vulnerability details: CVE-2020-6819 is a use-after-free vulnerability due to a race condition when the nsDocShell destructor is running. CVE-2020-6820 is a use-after-free vulnerability due to a race condition in the ReadableStream class, which is used to read a stream of data.
Official announcement – https://www.mozilla.org/en-US/security/advisories/mfsa2020-11/

.jpg)