Preface: ThinPrint technology offload the print burden on all virtual and physical desktops, and keeps all client hardware free of printer drivers.
Background: VMware Workstation is a type 2 hypervisor. Type 2 hypervisors are essentially treated as applications because they install on top of a server’s OS. If the host gets cracked, the hypervisor gets cracked. If the hypervisor gets cracked, it depends on the host will have vulnerability let hacker to be use. From technical point of view, it is difficult but it may possible.
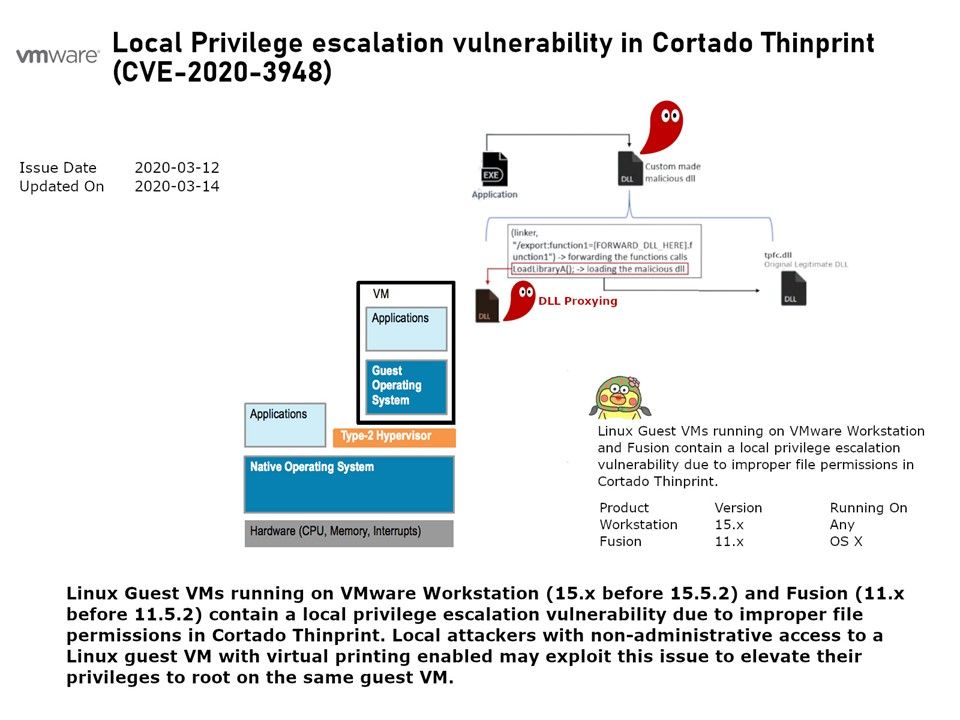
Vulnerability details: Linux Guest VMs running on VMware Workstation (15.x before 15.5.2) and Fusion (11.x before 11.5.2) contain a local privilege escalation vulnerability due to improper file permissions in Cortado Thinprint. Local attackers with non-administrative access to a Linux guest VM with virtual printing enabled may exploit this issue to elevate their privileges to root on the same guest VM. For the details of attack. Please refer to diagram.
Official announcement – https://www.vmware.com/security/advisories/VMSA-2020-0004.html