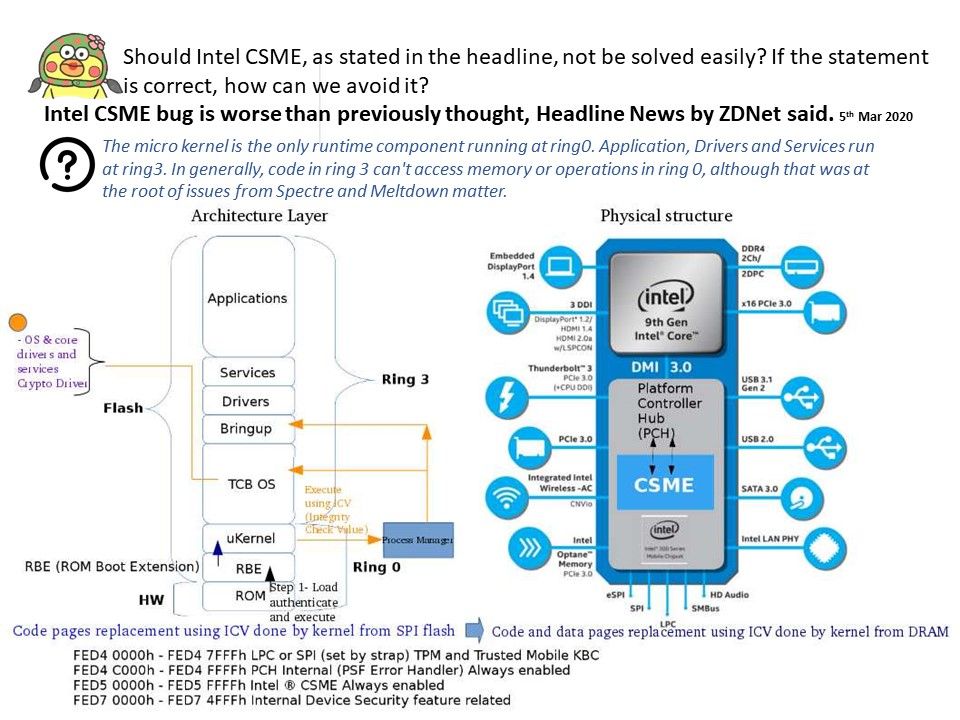
Background: CVE-2019-0090 told that Insufficient access control vulnerability in subsystem for Intel(R) CSME before version 12.0.35, Intel(R) SPS before version SPS_E3_05.00.04.027.0 may allow unauthenticated user to potentially enable escalation of privilege via physical access. On 5th Mar, 2020, cyber security expert firm has following findlings.Intel CSME firmware in the boot ROM first initializes the page directory and starts page translation. IOMMU activates only later. Therefore, there is a period when SRAM is susceptible to external DMA writes (from DMA to CSME, not to the processor main memory), and initialized page tables for Intel CSME are already in the SRAM.
Impact: Nonlinear write will bypass stack protector!
Remedy: When Stack-Protector XORed with Return address implemented, the Nonlinear write to bypass stack protector become difficult.
Current status: Please do the patching even though it is not perfect – https://www.intel.com.au/content/www/au/en/support/articles/000025694/processors/intel-core-processors.html