Preface: Microsoft has released a security advisory to address a remote code execution vulnerability (CVE-2020-0796) in Microsoft Server Message Block 3.1.1 (SMBv3) on 11th Mar 2020.
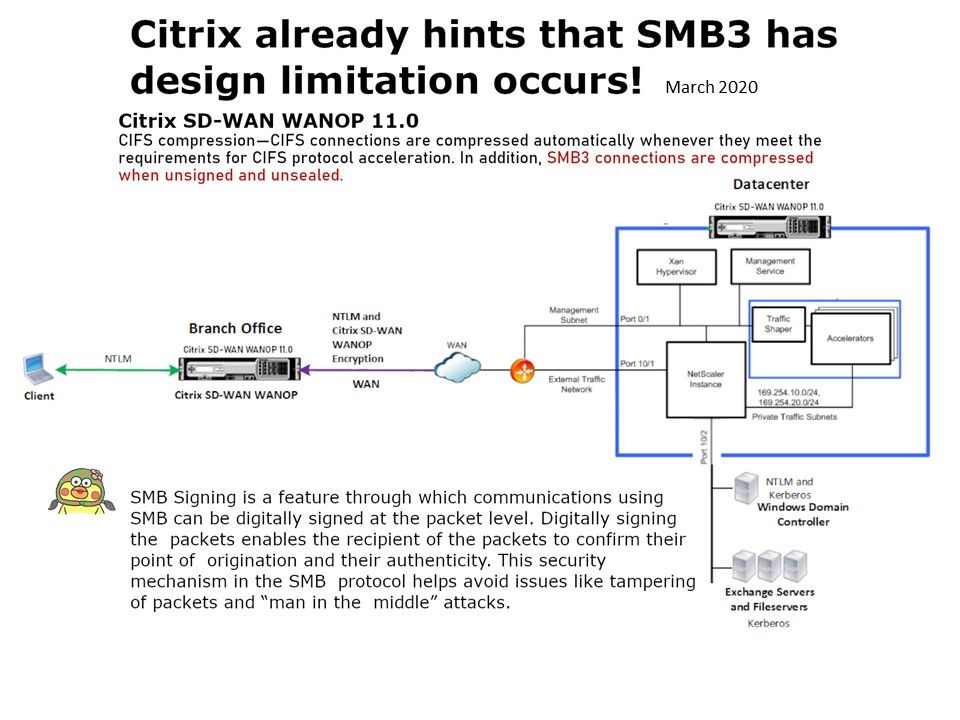
Vulnerability details: A remote attacker can exploit this vulnerability (CVE-2020-0796) to take control of an affected system. A “potentially wormable” vulnerability exists in SMBv3 and specifically the compression. Citrix already hints that SMB3 has design limitation occurs (see below):
CIFS compression—CIFS connections are compressed automatically whenever they meet the requirements for CIFS protocol acceleration. In addition, SMB3 connections are compressed when unsigned and unsealed.
Why is it dangerous? SMB Signing is a feature through which communications using SMB can be digitally signed at the packet level. Digitally signing the packets enables the recipient of the packets to confirm their point of origination and their authenticity. This security mechanism in the SMB protocol helps avoid issues like tampering of packets and “man in the middle” attacks.
Remedy solution by Microsoft – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/adv200005