Preface: A conspiracy was leaked this week, someone ambitious to spying the world.
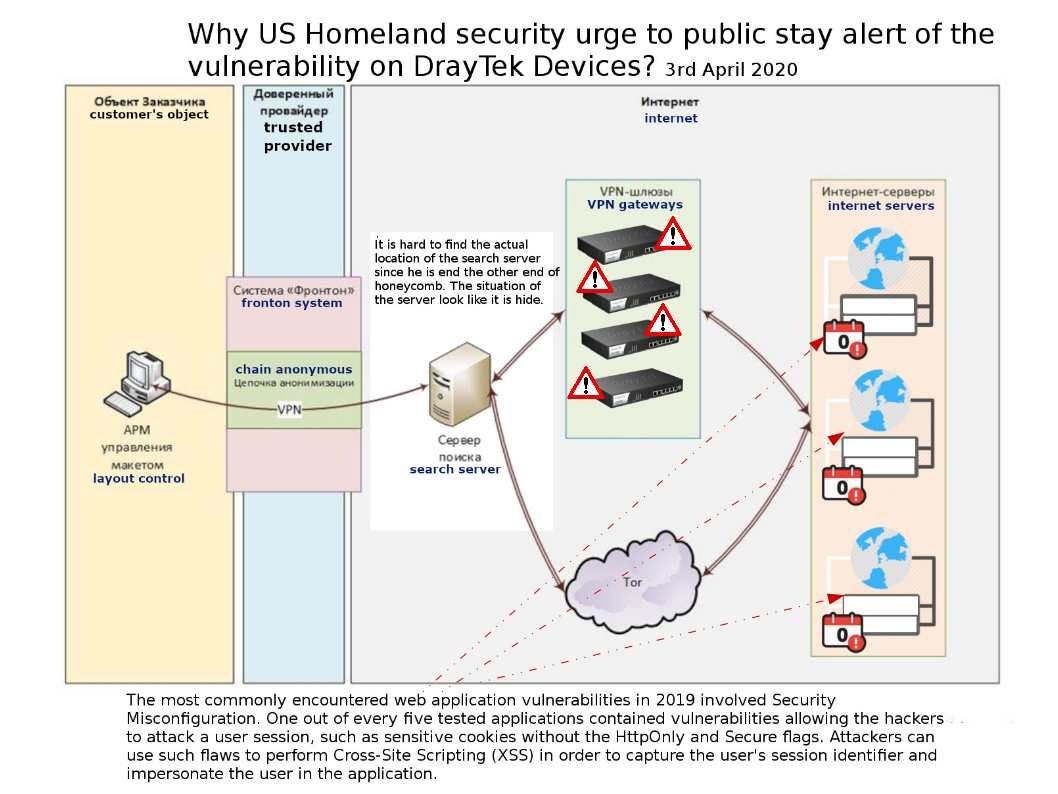
Details: The espionage activities will be exploit computer technology as 1st approach in today. It is merely relies on design weakness. Yes, it is the vulnerability. When I read the conspiracy details, I was wonder that if the formulation of this design (see attached diagram) goals to do a DDoS. Perhaps this is no a perfect way. However when US Homeland security urge to US citizen staying alert of the vulnerability found in DrayTek Devices. As everyone knows, today’s Tor network cannot perfectly hide the whereabouts of hackers. Because law enforcement already shutdown the proxy servers on the network. Besides, attacker also worries that does the proxy server has monitoring function. From attacker view point, they should perfectly hide itself. Refer to attached diagram, the new formulation of botnet technique will be exploited the new vulnerability found on IoT as a component. It looks like a plug-in module.
There are two types of operating system that sit under the SDK. Low cost and lower specification routers will select the RTOS. Since low end router cannot fulfill their requirement. Perhaps the VPN Router is the correct target because when compromised VPN router form a bot net group can compensate the current resources outage in Tor network.
Immediate action: Multiple vulnerabilities have been discovered in DrayTek devices which could allow for arbitrary code execution. If you are customer of DrayTek. Please do the upgrade immediately. https://www.draytek.com/about/security-advisory/vigor3900-/-vigor2960-/-vigor300b-router-web-management-page-vulnerability-(cve-2020-8515)