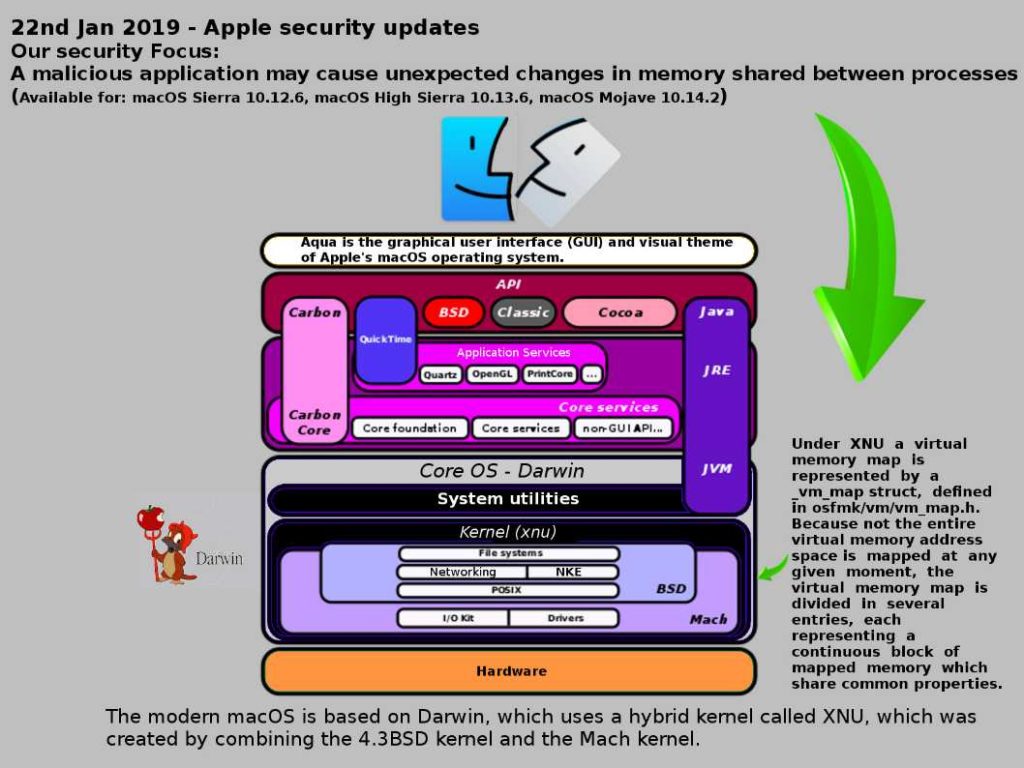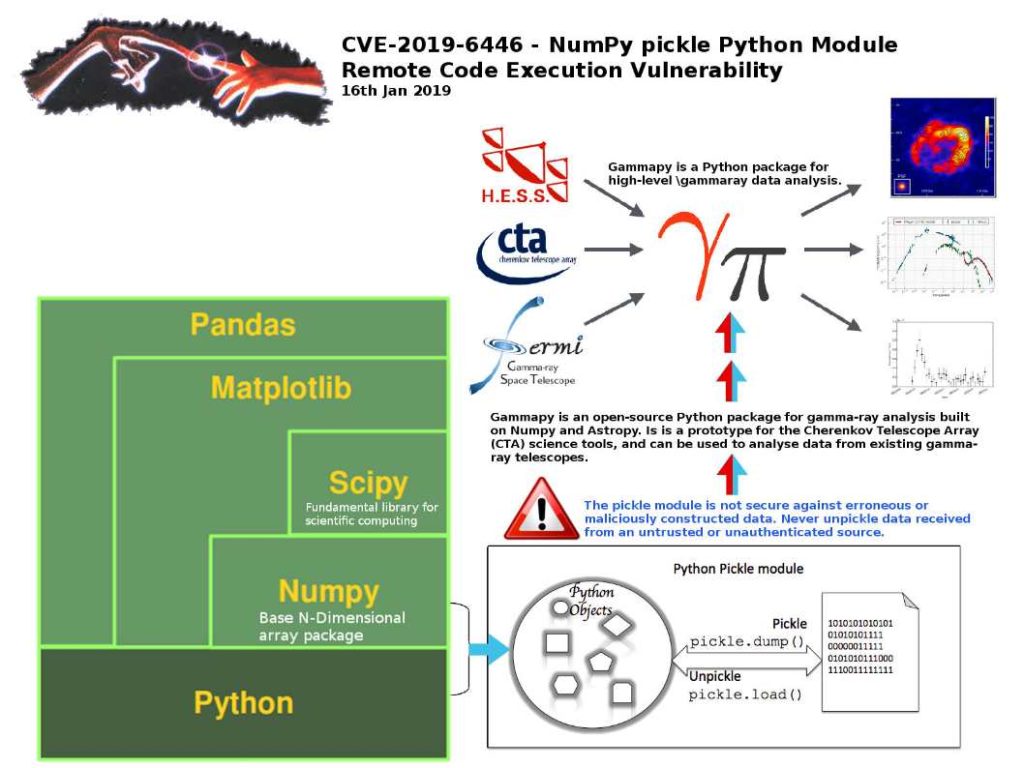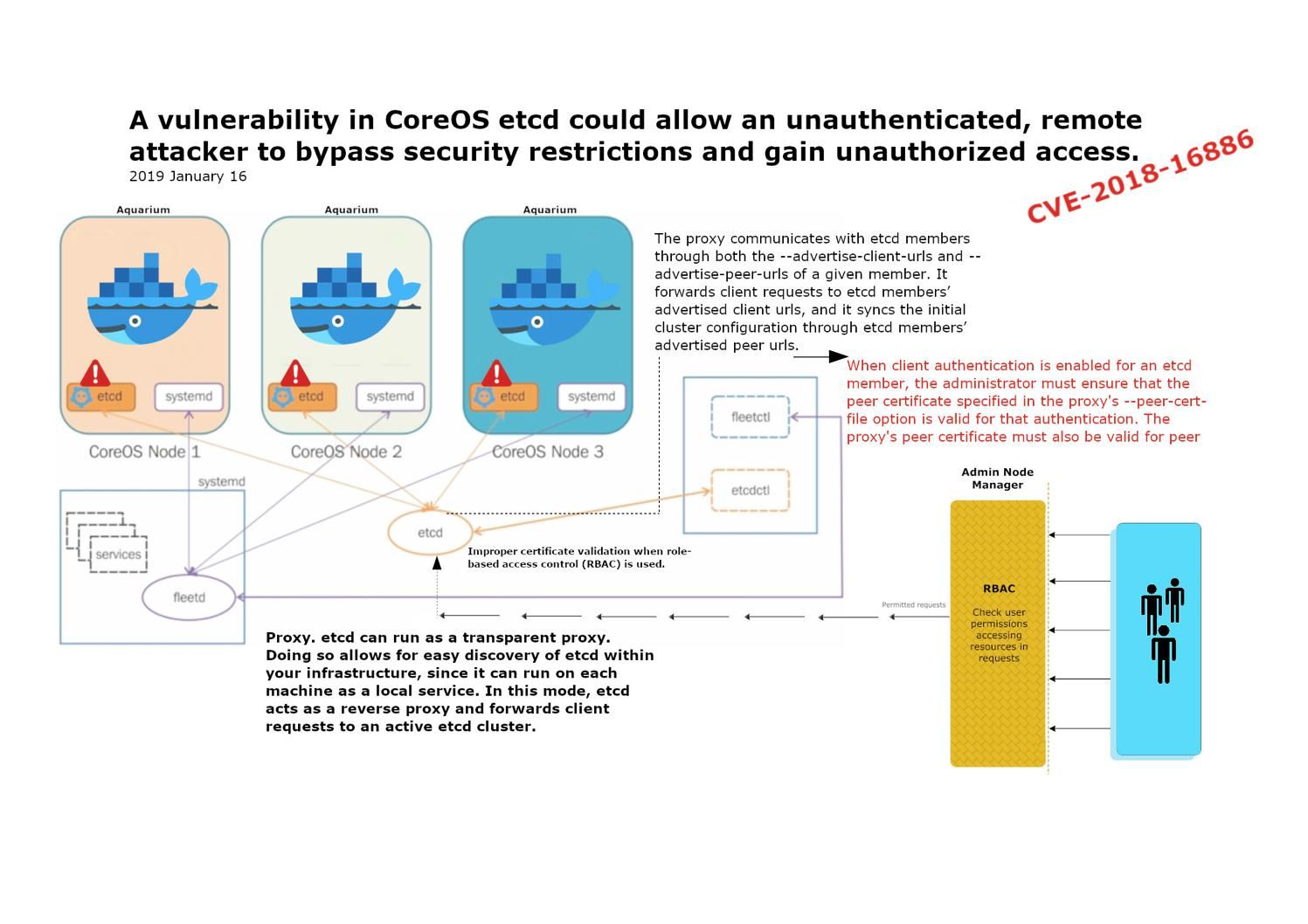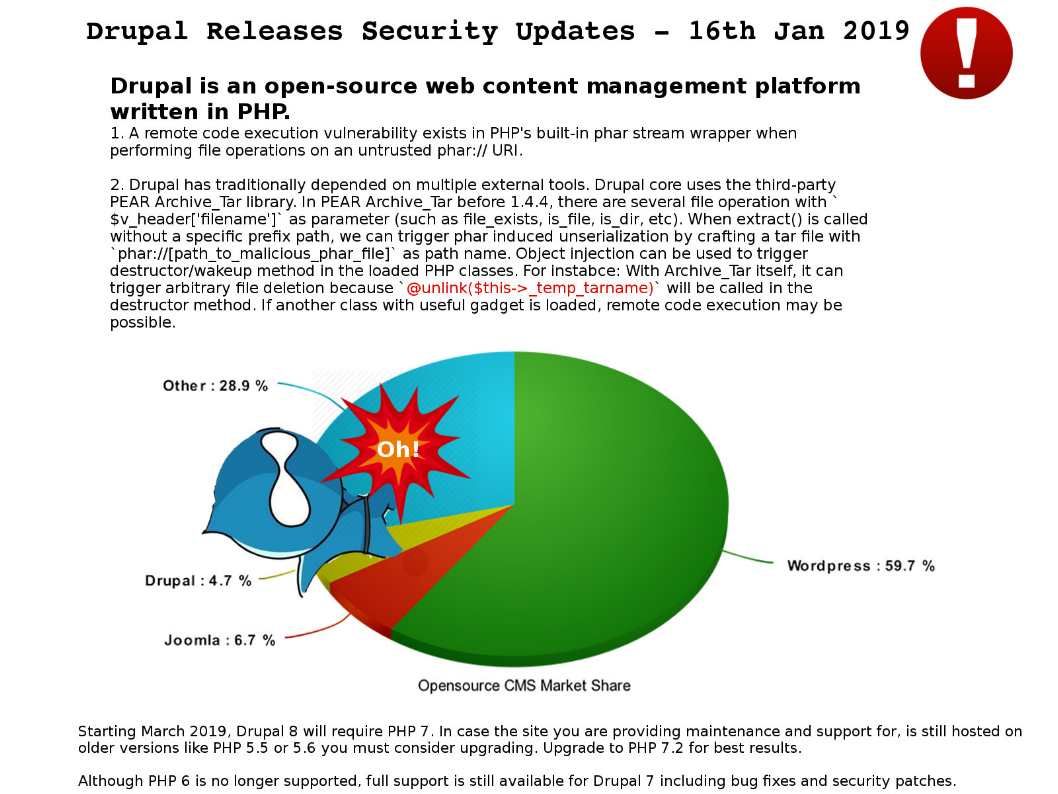
Preface: phpMyAdmin is a free software tool written in PHP, intended to handle the administration of MySQL over the Web.
Description: Phpmyadmin sometimes similar is a gadget. It can help you reset your WordPress password. It seems to be very useful, but this time the vulnerability is equivalent to the Swiss Army Knife, thus breaking your defense mechanism.
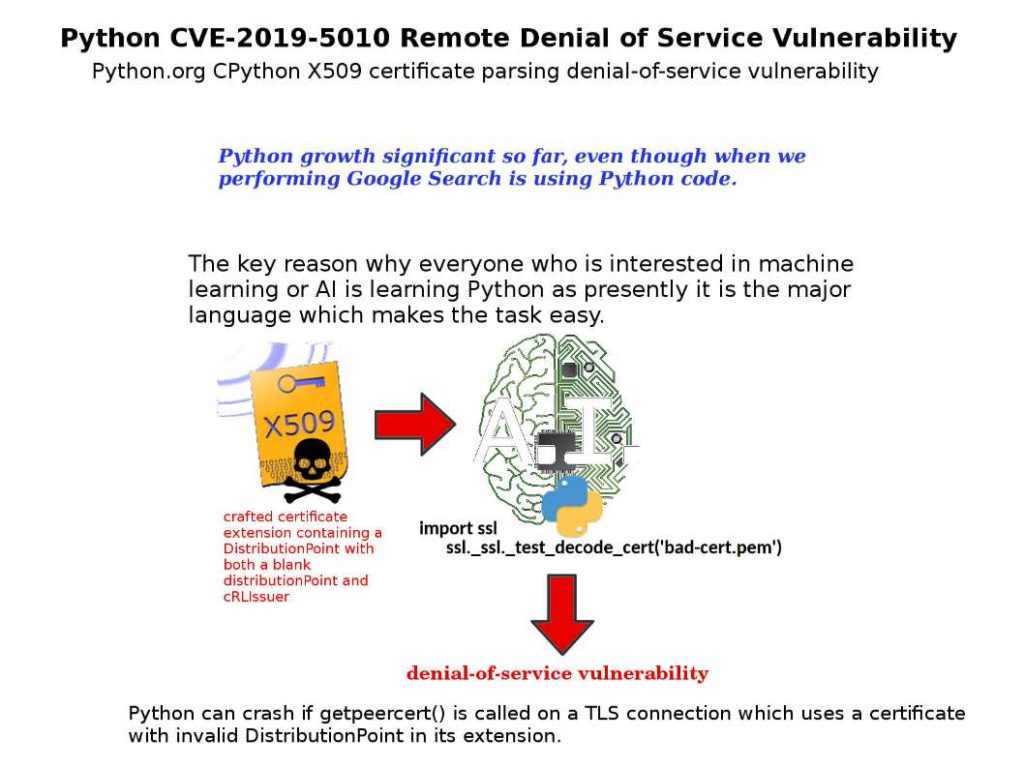
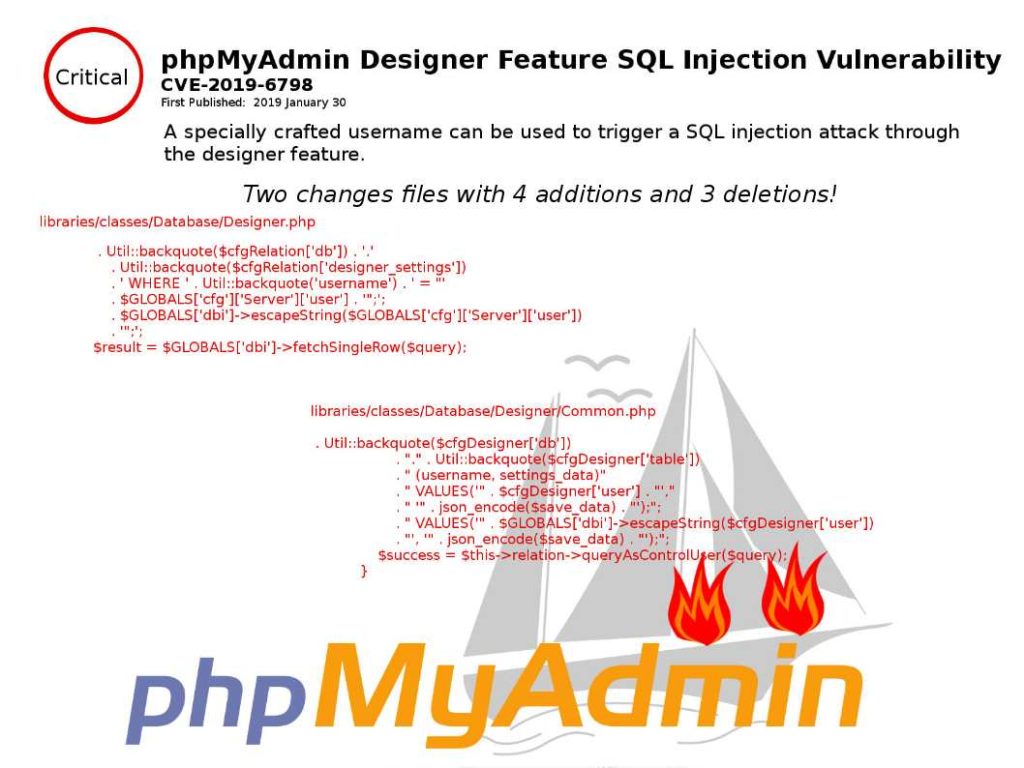
Vulnerability detail: An issue was discovered in phpMyAdmin before 4.8.5. A vulnerability was reported where a specially crafted username can be used to trigger a SQL injection attack through the designer feature.
Official reference: https://www.phpmyadmin.net/security/PMASA-2019-2/