Background: Linux pam originated from the open source implementation of the software DCE-RFC of Sun, a well-known manufacturer later acquired by Oracle. PAM is called Pluggable Authentication Modules, which can be inserted into authentication modules. Various authentication modules and plug-ins can be dynamically introduced for authentication without reloading the system, very flexible.
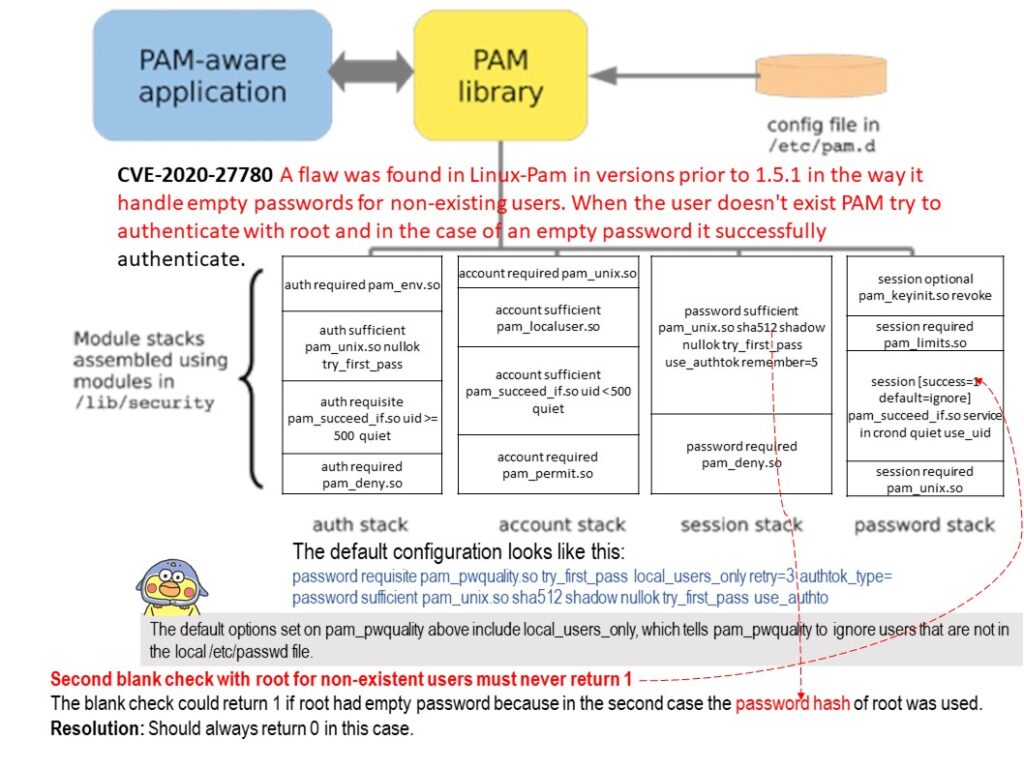
Vulnerability details: When the user doesn’t exist PAM try to authenticate with root and in the case of an empty password it successfully authenticate.
Reason: The default options set on pam_pwquality above include local_users_only, which tells pam_pwquality to ignore users that are not in the local [/]etc[/]passwd file. However, the blank check could return 1 if root had empty password
because in the second case (refer to diagram) the password hash of root was used.
Remediation: https://github.com/linux-pam/linux-pam/releases