In 80’s our daily life without any electronic type social media involves. But we understood that we are avoid to talk to the stranger. As time goes by, internet social media fine tune our mind. As a result we make friend and relies on this communication platform.
Since this is a popular open platform. It is hard to avoid scam activities. As a result, the risk factor will growth in such circumstances. Even though you have security awareness . But who can garantee the threat actor only focus to attack the indiviual instead of the social media vendor.
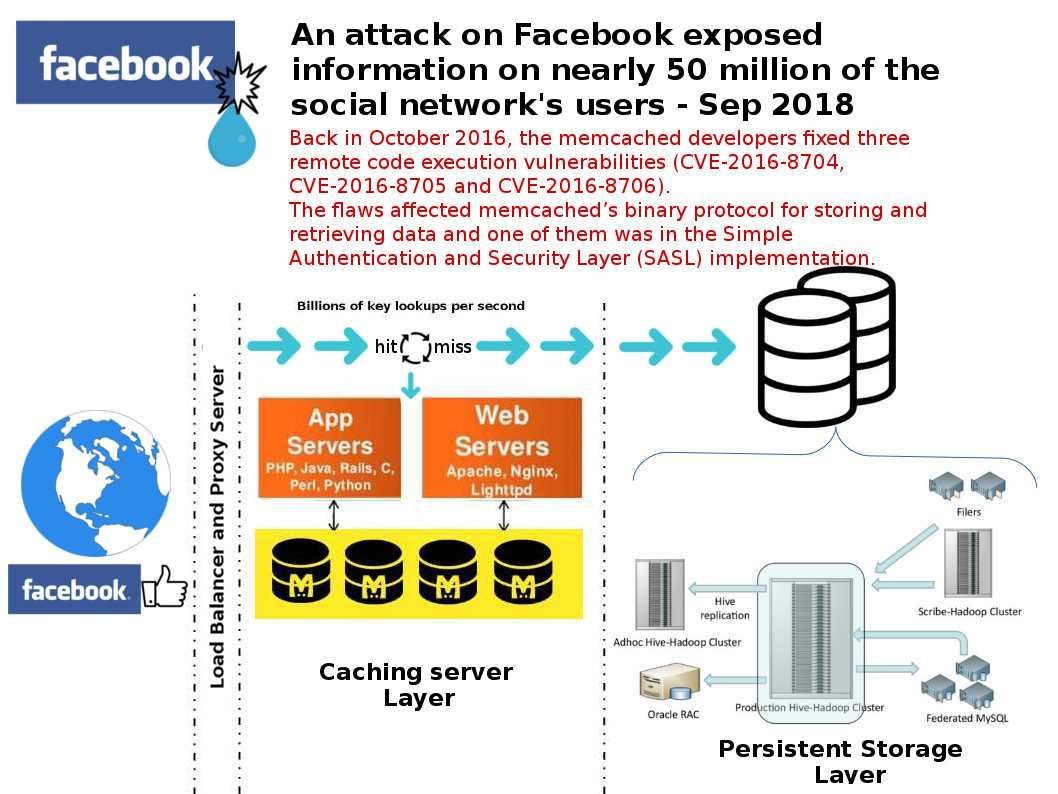
Back in October 2016, the memcached developers fixed three remote code execution vulnerabilities (CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706). The flaws affected memcached’s binary protocol for storing and retrieving data and one of them was in the Simple Authentication and Security Layer (SASL) implementation.
Remark: CVE-2016-8704 – An integer overflow in the process_bin_append_prepend function in Memcached, which is responsible for processing multiple commands of Memcached binary protocol, can be abused to cause heap overflow and lead to remote code execution.
Do you think the data breaches announced by Facebook yesterday whether it happen earlier last year but nobody know?