Preface:
Any idea from you in regards to cryptocurrencies security features at this moment? From technical point of view, blockchain technology is able to protect the data in the block. Thus hacker is hard to modify the data. It looks a prefect system. As far as we know, crypto currencies platform not secure as expected. But what is the actual problem ?

Refer to above diagram, it explicitly show the design weakness of Ethereum design. Since both smart contract and ethereum wallet has critical vulnerabilities occurred. Since a design weakness occurred in the end point (Ethereum wallet). In additional of the smart contract has vulnerability occurred. And therefore it provides a gut feeling to people crypto currency not indeed safe.
Known Attack
Integer Overflow and Underflow
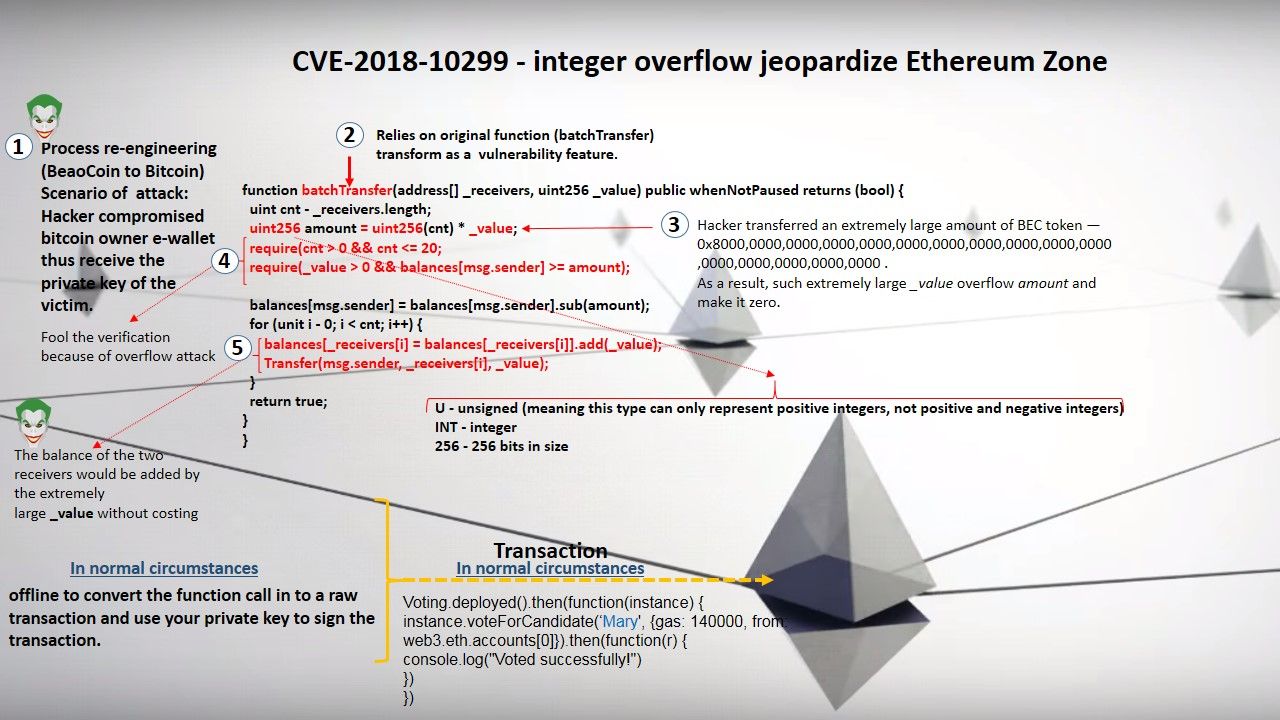
Definition of integer overflow – If a balance reaches the maximum uint value (2^256) it will circle back to zero. Since the uint variable changes state, If any user can call functions which update the uint value, it’s more vulnerable to attack.
We understand that web3.js is a collection of libraries which allow you to interact with a local or remote Ethereum node, using a HTTP or IPC connection. Java application encounter vulnerabilities caused end user encounter cyber attack is not a news. Above informative diagram shown the integer overflow vulnerability of Ethereum case study involves java applet on the client side. As a front end application, Java application may not aware that he is the accomplice with the cryptocurrency cyber security incident.
Definition of integer underflow – If a uint is made to be less than zero, it will cause an underflow and get set to its maximum value. C-like underflow might affect Solidity storage. It can arbitrarily allow malicious changes to constant variables. Below is the example of uint overflow and underflow.
Remark: What is the largest value you can represent using a 256-bit unsigned integer?
The 256-bit unsigned int (uint) data type can hold integer values in the range of 0 to 11579208923731619542357098500868790785326998466564 0564039457584007913129639935
contract C {
// (2**256 - 1) + 1 = 0
function overflow() returns (uint256 _overflow) {
uint256 max = 2**256 - 1;
return max + 1;
}
// 0 - 1 = 2**256 - 1
function underflow() returns (uint256 _underflow) {
uint256 min = 0;
return min - 1;
}
}
A vulnerability in the Parity Wallet library contract of the standard multi-sig contract has been found.
In June 2016, users exploited a vulnerability in the DAO code to enable them to siphon off one third of The DAO’s funds to a subsidiary account. On 20 July 2016 01:20:40 PM +UTC at Block 1920000, the Ethereum community decided to hard-fork the Ethereum blockchain to restore virtually all funds to the original contract.
All dependent multi-sig wallets that were deployed after 20th July. No funds can be moved out of the multi-sig wallets afterwards. For more details, please see below:
contract Wallet {
function () payable {
Deposit(...)
}
}
CVE-2018-10666
CVE-2018-10666 – The vulnerability allows attackers to acquire contract ownership because the setOwner function is declared as public. A new owner can subsequently modify variables (see below diagram for reference).

Status update on 22nd May 2018
CVE-2018-11239 – An integer overflow in the _transfer function of a smart contract implementation for Hexagon (HXG), an Ethereum ERC20 token, allows attackers to accomplish an unauthorized increase of digital assets by providing a _to argument in conjunction with a large _value argument, as exploited in the wild in May 2018, aka the “burnOverflow” issue.
CVE-2018-10944 – The request_dividend function of a smart contract implementation for ROC (aka Rasputin Online Coin), an Ethereum ERC20 token, allows attackers to steal all of the contract’s Ether.
Observation:
In regards to the cyber security incident happened in past, the Ethereum system looks did not shown they are capable to protect himself.
Their functionaility may have improvement comparing with traditional bitcoin technology (see below):
|
Hyperledge |
Ethereum |
Bitcoin |
| Association |
Linux Foundation |
Ethereum Developers |
Bitcoin Developers |
| Currency |
N/A |
Ether |
BTC |
| Mining Reward |
N/A |
Yes |
Yes |
| Network |
Design goal – Private |
Design goal – Public |
Public only |
| Privacy |
Private |
Open |
Open |
| Smart Contracts |
Multiple-programming language |
C++,Rust and Go |
i. Bitcoin Core, is written primarily in C++
ii. Lightweight clients like MultiBit and Bitcoin Wallet written in Java |
Next step : How to Protecting Yourself and Your Funds
1. One of the safest & easiest ways to store your ETH is use a hardware wallets.
2. Activate 2FA (duh) on any exchanges or online wallet you use.
3. Move your ether off exchanges, into a hardware wallet or paper wallet.
How to view your account balance, look up transaction and explore smart contracts?
Etherchain is an Explorer for the Ethereum blockchain. It allows you to view your account balance, look up transactions and explore smart contracts.
Browse all Ethereum Transactions – https://www.etherchain.org/txs
In God We Trust.
— End —
News update on 14th Aug 2018: An critical vulnerability was found in EETHER.An integer overflow occurs in unprotected distributeToken function. See below details for reference.
https://github.com/rootclay/Audit-of-smart-contracts/blob/master/0x00a0cbe98e4d110b0fa82646152d77babf2951d0/README.md