Preface:
Timothy 6:10: “For the love of money is the root of all [kinds of?] evil”
Before we jump into discussion see the bitcoin market status today
Ethereum briefly crashed from $319 to 10 cents , said Thursday (22nd June 2017) CNBC News.
The CoinDesk Bitcoin Price Index provides the latest and most accurate bitcoin price using an average from the world’s leading exchanges.
As of today (22nd June 2017) ,1 Bitcoin equals 2716.06 US Dollar
How does Finance sector think about it?
On 26th May 2017, Bank of America Corp, SBI Holdings Inc, HSBC Holdings Plc, Intel Corp and Temasek Holdings have invested $107 million in R3 CEV. The R3 is made up of financial industry veterans, technologists, new tech entrepreneurs and subject matter experts. This group of people goal to building the next generation of global financial services technology. Sound amazing that finance sector are keen to involves the blockchain or bitcoin technologies.
Perhaps bitcoin or blockchain are in mature stage now. It looks that it lack of acceptability. Even though banking industry treat the new payment concept with respect. But technically did not potentially replace the traditional payment gateway especially SWIFT payment system. Since different have different official financial policies and guideline.
How does criminal think about it?
When we talk about blockchain technology, most of the time we will think about hacking. How to jail break the encryption algorithm. Few expertise opinion. The break point of the blockchain technology not focus on break though the encryption. Seems it is not easy to do. But bitcoin technology concerns of “double spend” of electronic coins. In the sense that bitcoins technology itself is aware of it. Are you interested of this information. Be my guest, take a short journey to dig out a little bit. Ok, are you ready. Our train is leaving the platform now.

World more complex, a new technology appears, it is Hyperledger?
Hyperledger is an open source collaborative effort created to advance cross-industry blockchain technologies. It is a global collaboration, hosted by The Linux Foundation, including leaders in finance, banking, IoT, supply chain, manufacturing and technology.
Remark: Hyperledger compared to traditional interbank settlement , the overall completion need time will be shorten compared to traditional process. Meanwhile the hyperledger transaction of volume will be higher. Therefore the expert claimed that this is a speedy area like a motorway.
From technical point of view, Blockchain and Hyperledger technologies are located in services layer (see below).
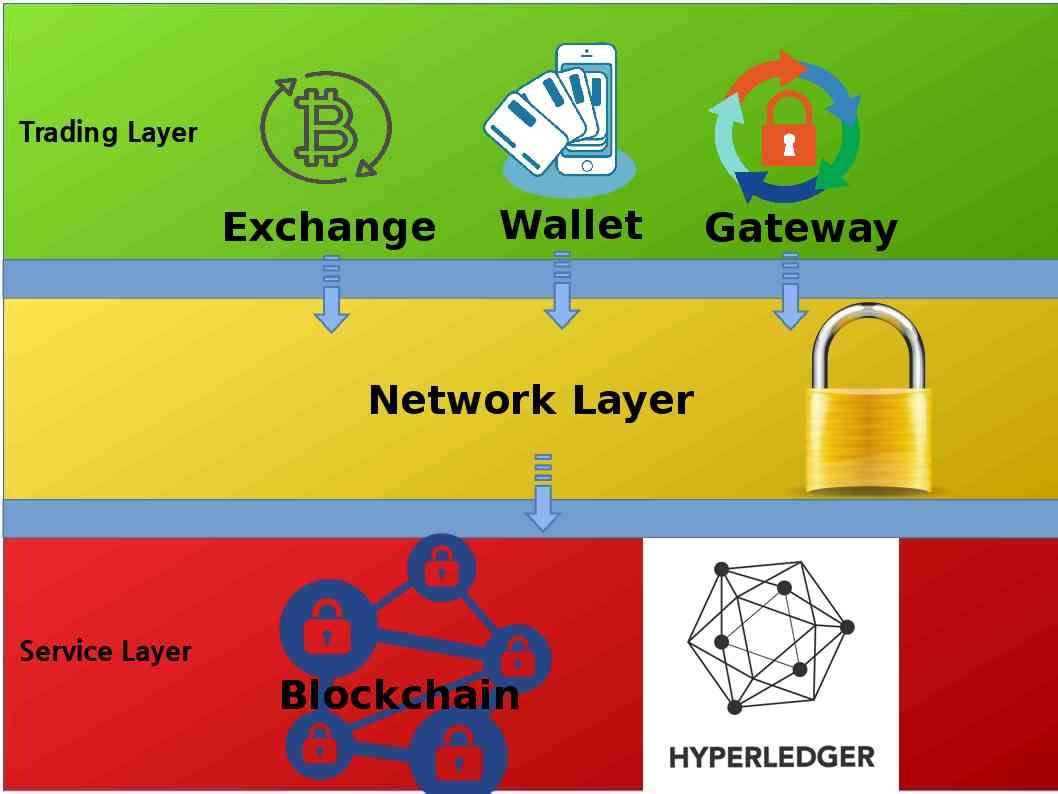
No matter how the technology renovation in future, double spend might have possibility happens. Before we discuss the double spend attack technique concept. Let’s use a simple way to understand the feature of both new and traditional technology elements. On this article, we found 2 units of element shown in Service layer. That is blockchain and hyperledger. Hyperledger benefits for cross-industry blockchain technologies. We can say it will be run in properaitery private network. Blockchain technology are open for public usage. You and me can enjoy the benefits (no transaction fees). May be you can dig out more. But above criteria is easy for your identification. Below is the hyperledger blockchain platforms for your reference.
The availablility of Hyperledger blockchain platforms today.
Hyperledger Burrow – Burrow is a blockchain client including a built-to-specification Ethereum Virtual Machine. Contributed by Monax and sponsored by Monax and Intel.
Hyperledger Fabric – Contributed by IBM.
Hyperledger Iroha – Based on Hyperledger Fabric, with a focus on mobile applications. Contributed by Soramitsu.
Hyperledger Sawtooth – Contributed by Intel
We can go to cyber attack concept now, let’s move on.
Double-spend Attacks
Double-spending is the result of successfully spending some money more than once. It means that a suspicious transactions spend from the same inputs as the first set of transactions. The transactions conflict and are thus double spends. In order to avoid to this problem occurs. Only one transaction out of a set of double spends will be able to confirm. The rest of the transactions become invalid.
The one we consider of this attack does only work for fast payment scenarios. Oops….we known that hyperledger claim that he is work in fast payment scenarios? Are you kidding?
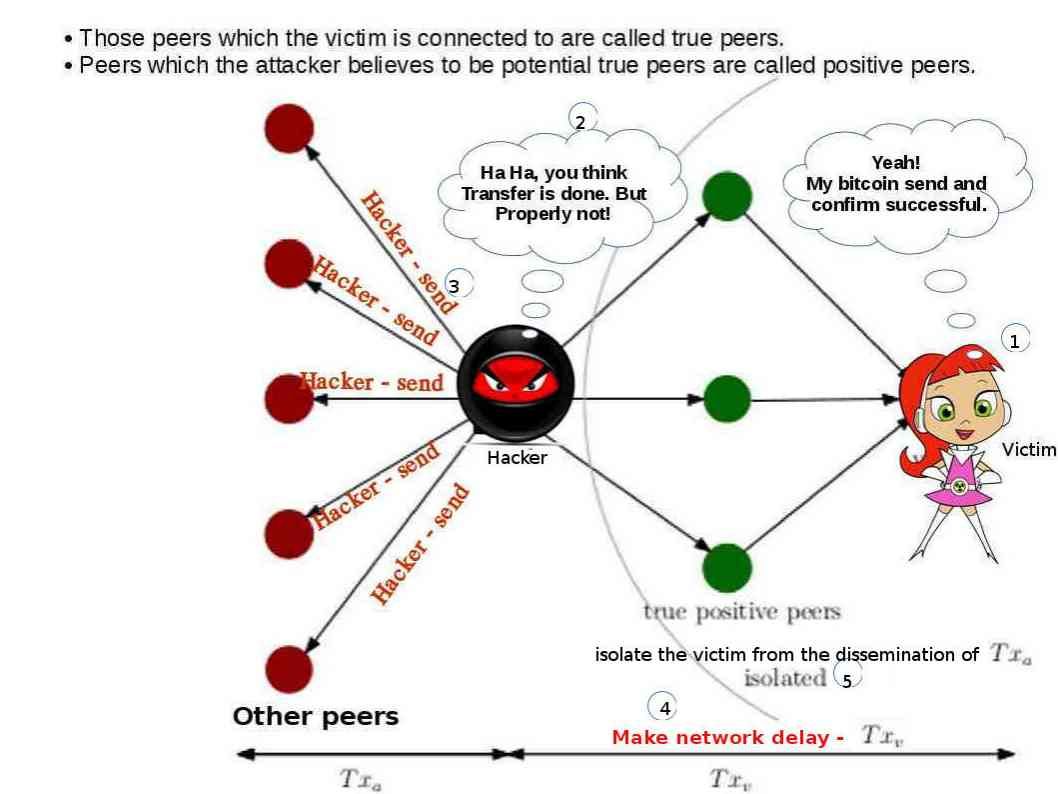
Actually a technical report issued by ETH Zurich did a proof of concept on the possibility of double-spend attack on blockchain instead of hyperledger. Below informative diagram can provide an idea to you in this regard. The test shown that make network traffic delay on Txv. And avoid the acknowledge issued by Txa go to victim. The test found factual issue occurred in this circumstances.
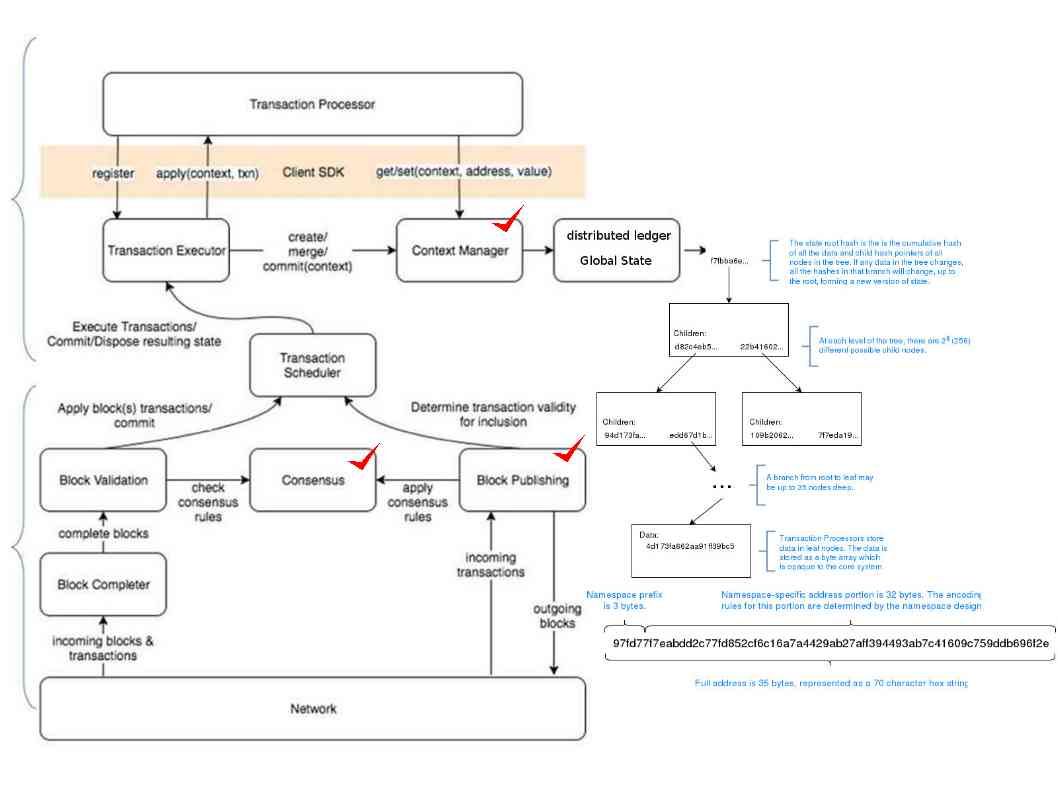
Since developers and blockchain investors understand the weakness of current blockchain technology. A group of financial investor build the next generation of technology goal to enhance the current technology design weakness. That is the hyperledger today. The features enhancement area includes Message handling, Block Publishing/validation, Consensus, Global State Management. Below informative diagram display the overall operation infrastructure. A segregates transaction payload definition, validation and stat management logic to improve overall security.
Observation: In this secure environment, how does hacker do?
Regarding to the authorization check on hyperledger design (see below informative diagram) it provide a comprehensive monitor feature to prevent incorrect and suspicious transaction. Hacker will take a another way round even through you have good authorization check system.
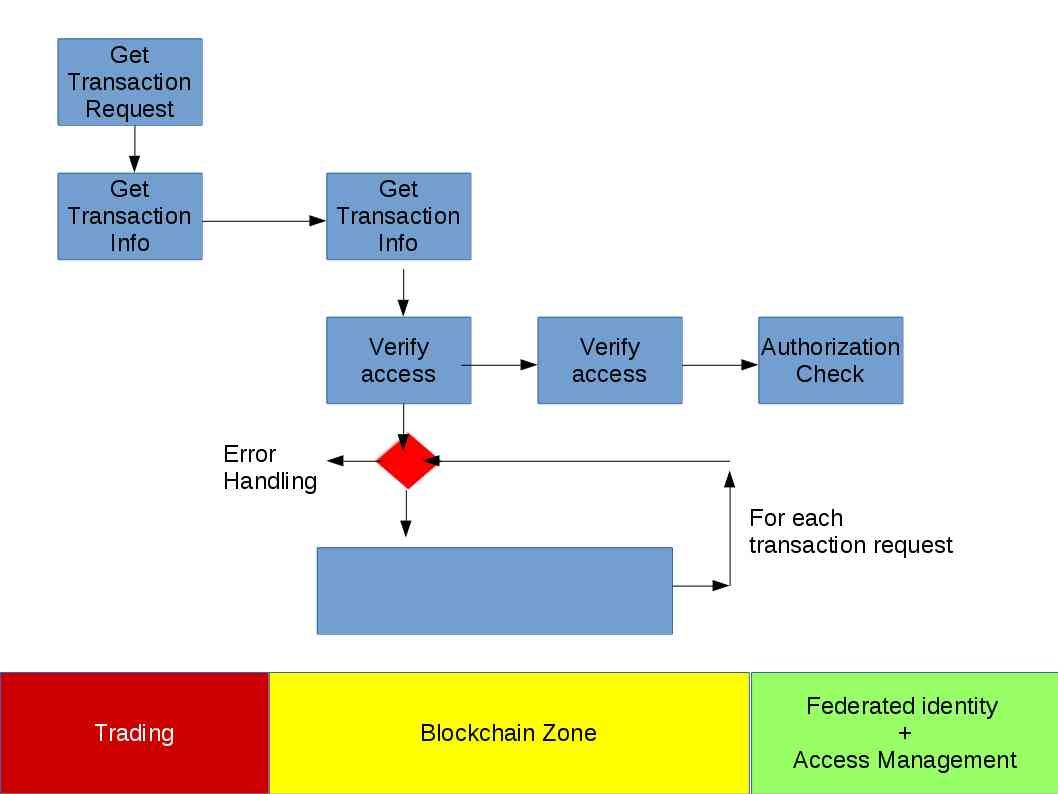
Since decryption of data not a easy way. It is time consuming and do not guarantee the successful rate. From technical point of view, hacker is not possible to spend on such afford. The possible and easy way is that hacker relies on the spear phishing technique. Then counterfeit messages appear to come from a trusted source fooling user in negligence. A misleading message lets user activate a internet link (url) which trigger malware infection. The hyperledger technique run in multi-layer architecture might expose more surface for attack. A insider threat might create a break point and causes the system compromised finally. As we know, ransomware is a hybrid architecture which coexists with malware and ransome features. Hacker can implant malware to a internal workstation then execute the ransomware attack afterwards.
The smart contract ID is unique reference number. No body else can help once the repository encrypt by hacker.
Is there any remediation solution on above matter?
Per my observation from past. Even though you have comprehensive detective and preventive security control. It is hard to avoid the incorrect business decision. In short, what is the drawback on above matters in regards to business decision. The business shake holder intend provide more flexibility on the system function. For instance customization of the application to fulfill business objective.
For corrective control solution. We can do the following to recover the system after ransomware infection.
- Increase the backup SNAPShot schedule. Since the delta improved. It reduce the overall loss of data percentage after system restore.
- Not allow critical host have access internet function. Perhaps you say, it is inconvenient to do the zero-day patch, critical patch and anti-virus signature update? But this is a important factor.
If you can use a simple way to move a mountain, why do you choose a heavy machine? Ok, let’s stop discussion here. Please take off the train.
But I will provide more interest topics soon! Bye!


