Preface
I’m smart brain, gave me lazy….
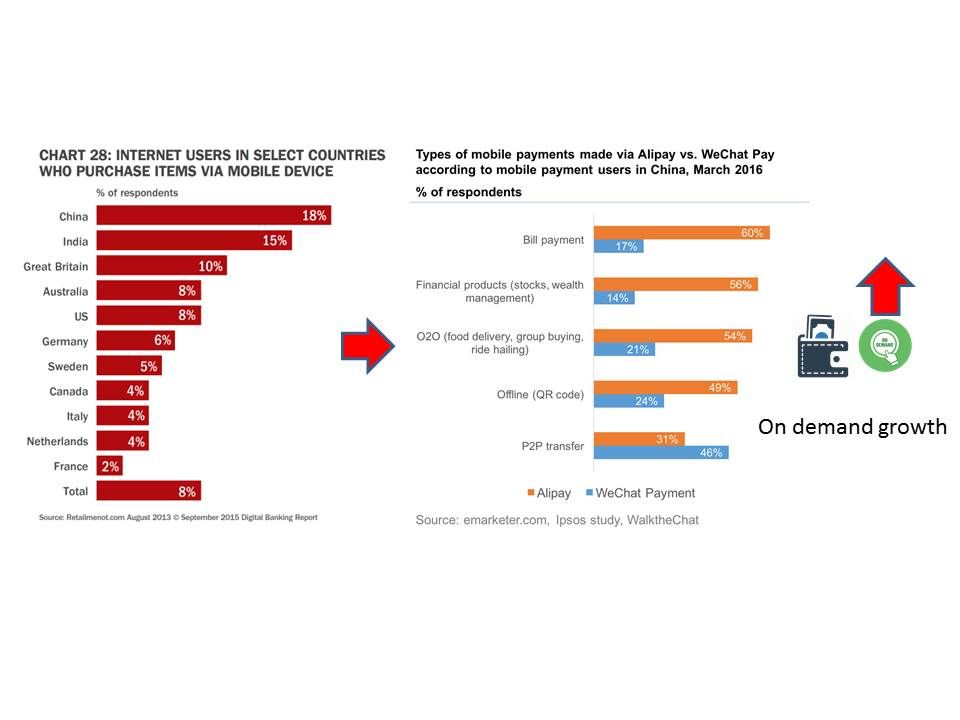
The implementation of the smart phone change people life style. Any time any where you can get in touch with the world. It break follow the sun operation concept. Why? Both online shopping and settlement simultaneously because of electronic payment function. Below bar chart on left hand side shown internet users in select countries who purchase items via mobile device in 2013. Less than 3 years time, a significant usage of mobile payment has been growth in Greater China (see below picture right hand side).
Cyber attack is a never ending story. Malware infection technique take the advantage of computer users negligence. Even though Bank did not have expection. The headline news shocked the world includes The Bangladesh Bank robbery. It was so called the Bangladesh Bank heist, took place in February 2016, when SWIFT instructions to steal US$951 million from Bangladesh Bank.
In order to avoid cyber incident happen on electronic payment transaction. Financial industry especially payment gateway services provider find perfection of authentication method goal enhance the reliability of payment. For instance 2 factor authentication, a second random generation of pass code go through SMS forward to you mobile phone.
Electronic wallet upside down to the world
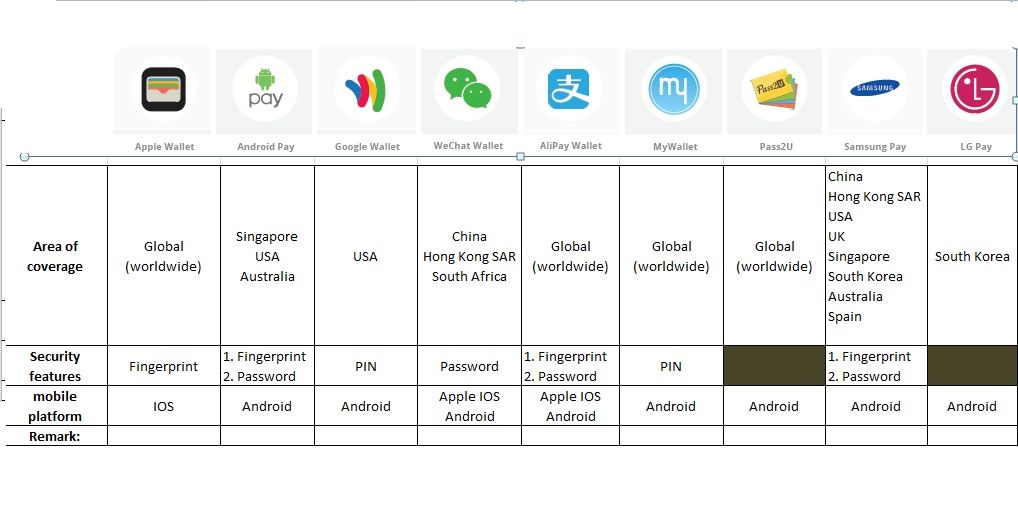
A third-party online payment platform was launched in China in 2004 by Alibaba Group. As times goes by, now the biggest market share in China with 400 million users. The coverage near 50% of China’s online payment market in October 2016. As of today electronic wallet looks like flooding went to different countries in the world especially China. Electronic wallet initiate by mobile phone. Below table can provide an hints to you in this regard.
Background
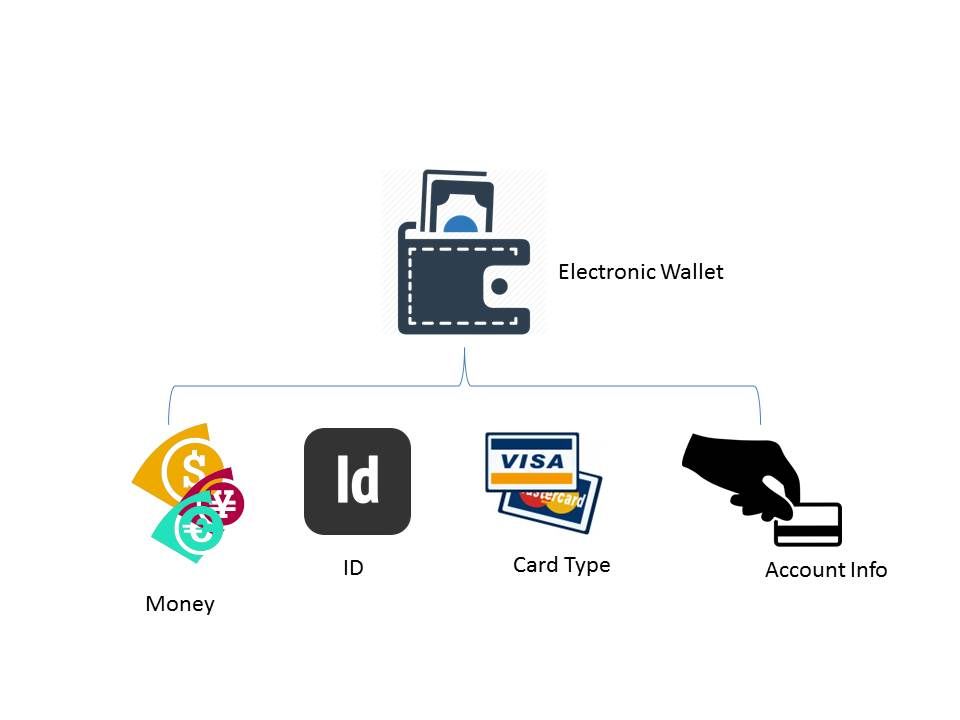
A digital wallet refers to an electronic device that allows an individual to make electronic transactions
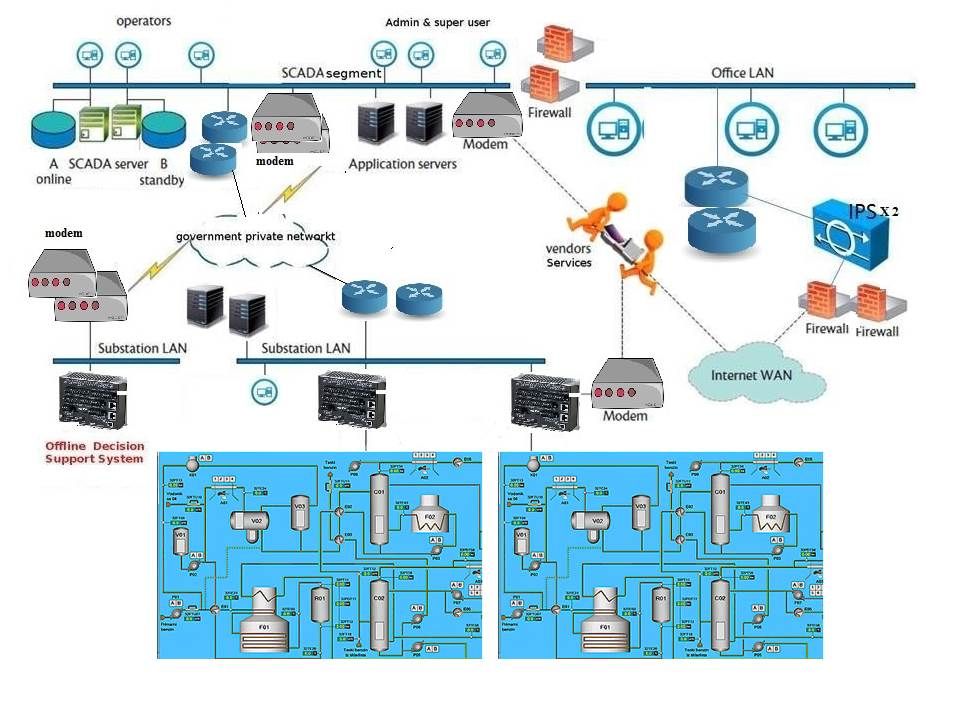
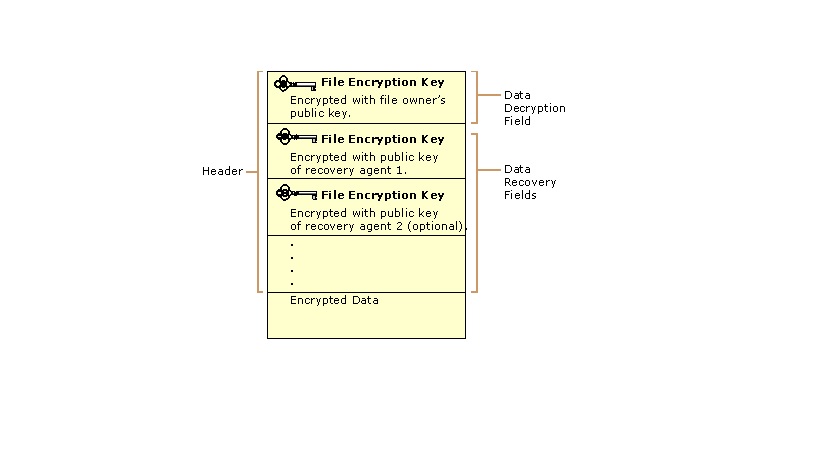
Digital wallet infrastructure elements
.
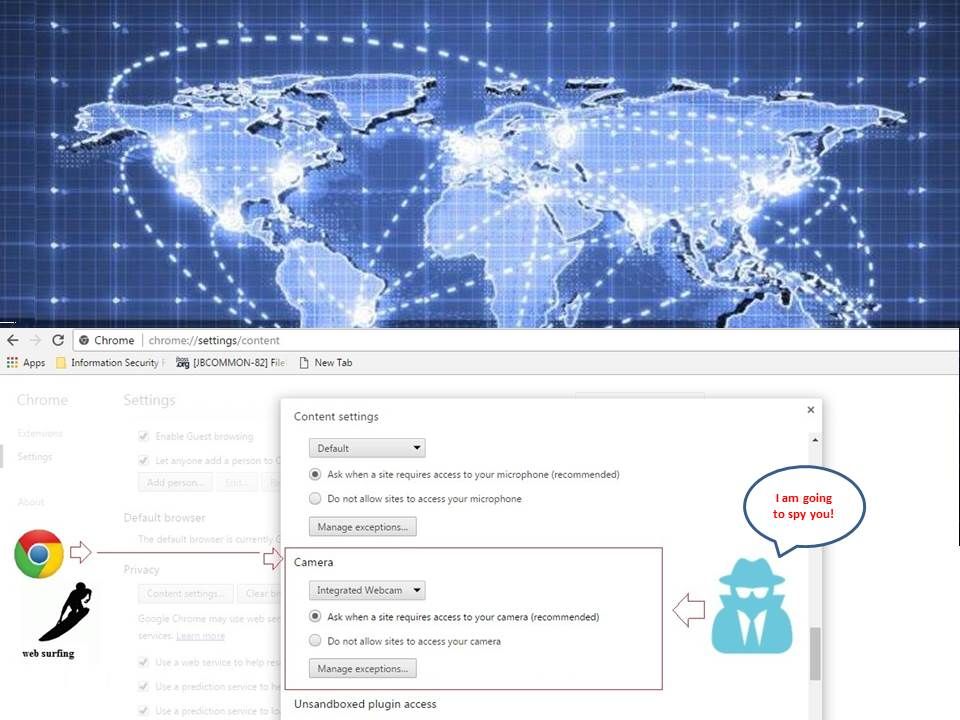
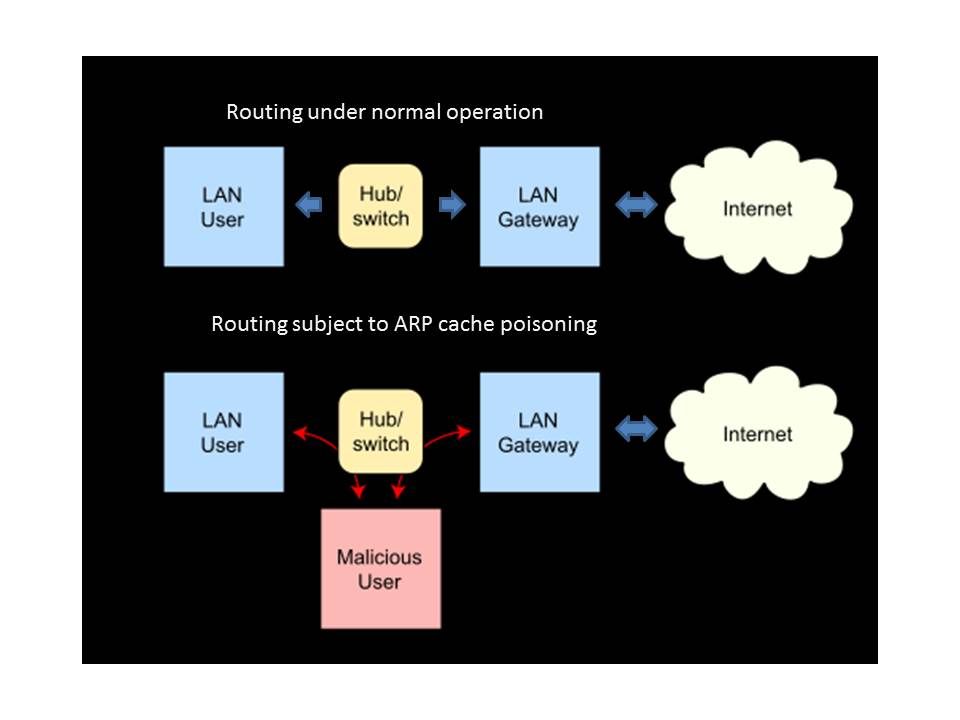
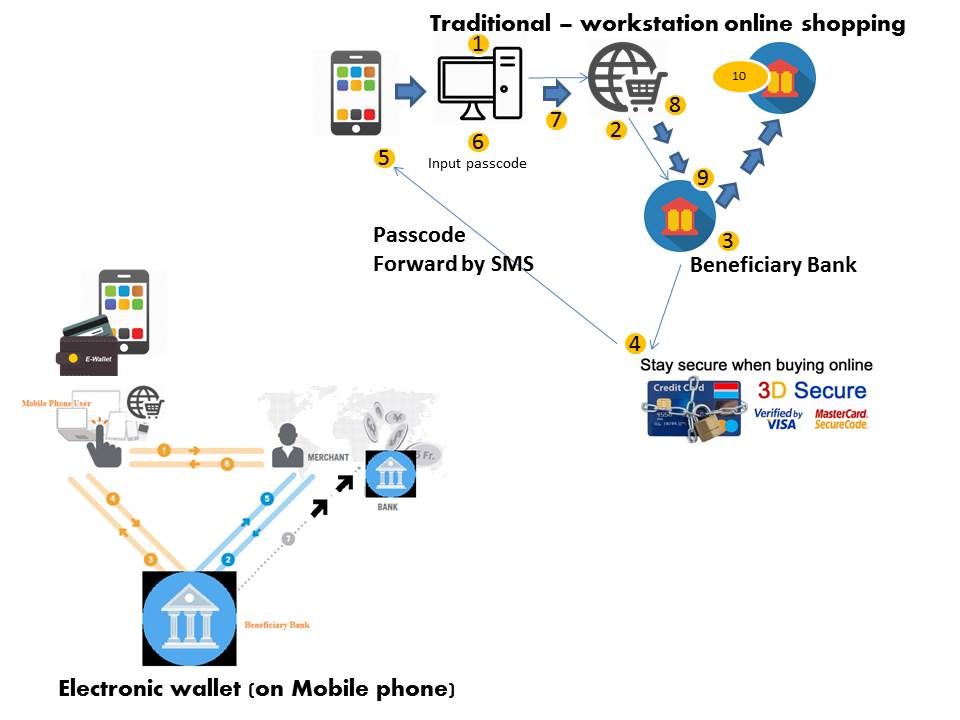
The account information and Card type lure the interest of criminals. But are you aware that there are difference in between mobile computing (electronic wallet) and traditional internet payment function (without electronic wallet). See below informatic diagram. Even though how precise and advanced encryption technology are deployed. But it is difficult to avoid a single device facing compromise. Personally I am not suggest my friend to use electronic wallet on his mobile phone. My friend was told even though money lost because of malware, it only lost the charge money value. Yes, from technical point of view it is correct. But reminded you that mobile OS is fragile. Why does it say mobile OS is fragile?
Why does it say mobile OS is fragile?
Android phone
(Memory)
Both the Android Runtime (ART) and Dalvik virtual machine perform routine garbage collection, this does not mean you can ignore when and where your app allocates and releases memory. Software designer need to avoid introducing memory leaks, usually caused by holding onto object references in static memory variables, and release any Reference objects at the appropriate time as defined by lifecycle callbacks.
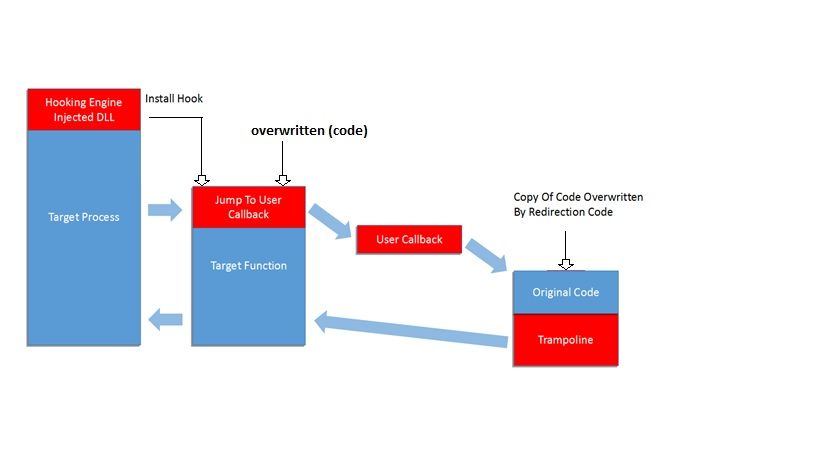
Side effect of above defect – The easiest way to leak an Activity is by defining a static variable inside the class definition of the Activity and then setting it to the running instance of that Activity. If this reference is not cleared before the Activity’s lifecycle completes, the Activity will be leaked. So all depends on mobile apps developer design. It is hard to avoid memory leak. As you know, what is the defect of memory leak? Hacker relies on this error can implant malware.
If you would like to know more details, please refer below articles.
Heard that Android operating not secure anymore, but it is properly not.
How about IOS?
Design weakness:
Every WebKit object is RefCountedBase object
Mobile Safari and most of WebKit Apps leak address – Fill in another object and use the JS pointer of the old object to read information of the new object.
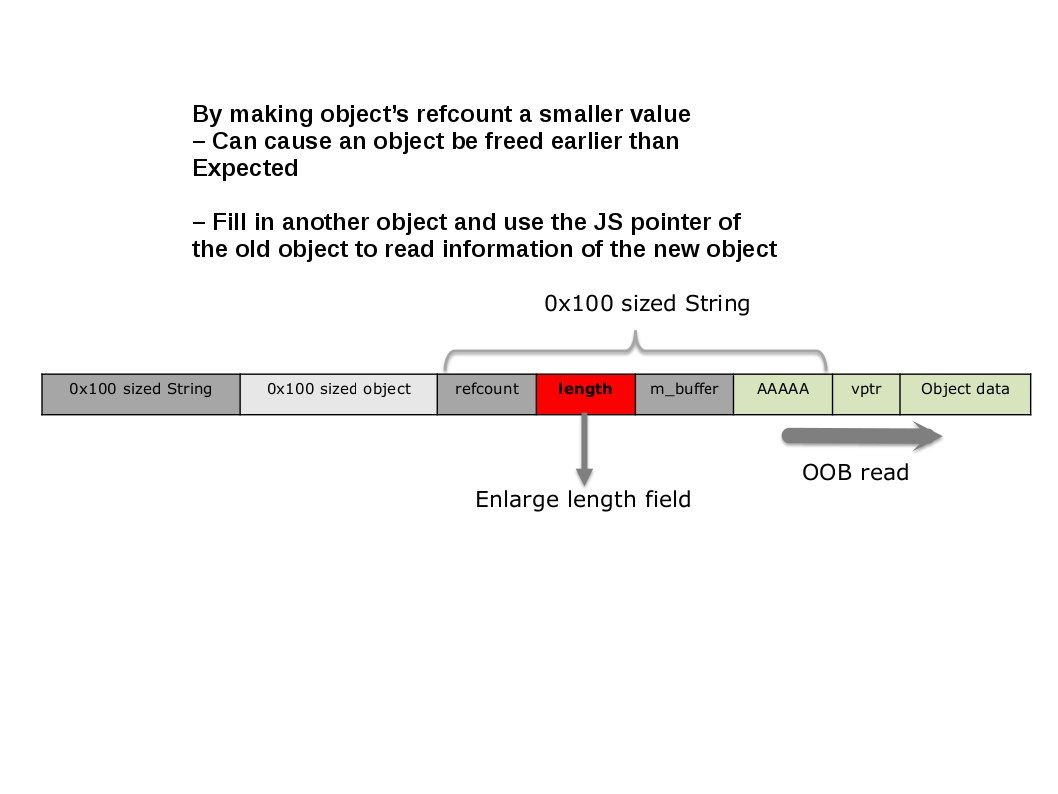
Should you have interest know the details on above matter, please refer below:
Checkpoint : If above 2 technical articles make you feeling confused. Tired, you are not able to read. No problem we can jump to summary of this discussion. The information will stay here, anytime you have interest you are free to read.
Summary:
IT & cyber security technologies due to limit development life cycle. OS claim itself is safe today but is it hard to guarantee next 6 months. The most fundamental weakness in mobile device security is that the security decision process is dependent on yourself. You are allow anywhere play online games & watch on-line TV program. Because of the web browser extend feature, uncountable plug-In drivers will install to your mobile phone. How about your personal information includes your personal account information. Do you think only relies on your local antivirus. The so called malware detection program can aviod the cyber attack?
My personal suggestion is that think it over before install or make use of electronic wallet on your mobile phone.
Have a nice day, Good Bye!