Preface: Network security experts may hesitate to answer a question. What is it? Which programming language is easy to write. But there are no loopholes.
CIS Center for Internet security announcement: Multiple Vulnerabilities in PHP Could Allow for Arbitrary Code Execution
For more information, please refer URL – https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-php-could-allow-for-arbitrary-code-execution_2019-087/
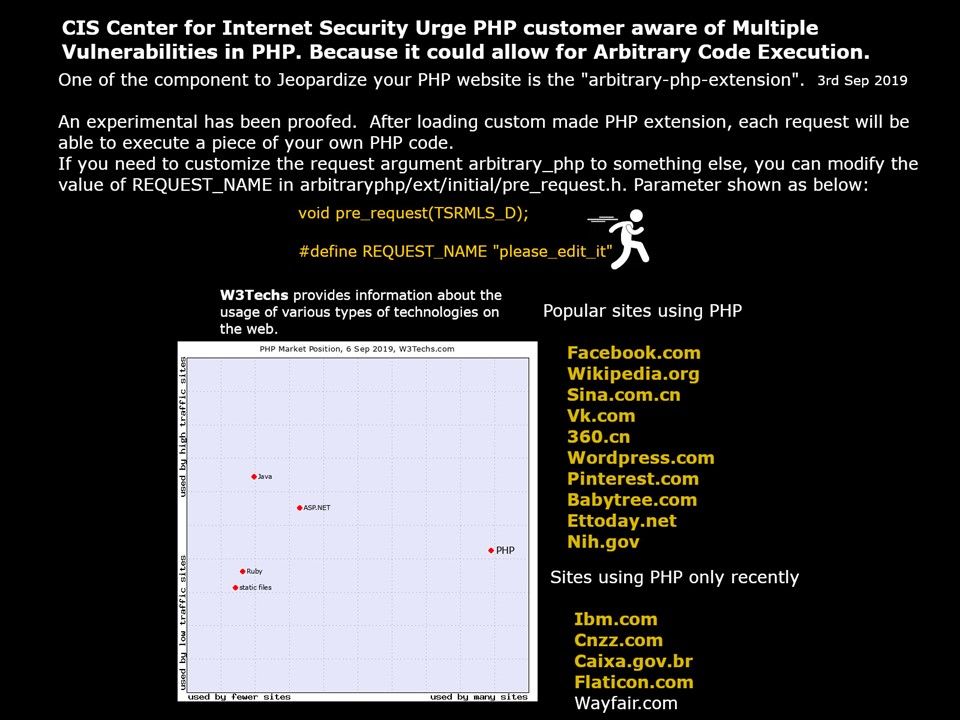
Our Observation: One of the component to Jeopardize your PHP website is the “arbitrary-php-extension”. An experimental has been proofed. After loading custom made PHP extension, each request will be able to execute a piece of your own PHP code. If you need to customize the request argument arbitrary_php to something else, you can modify the value of REQUEST_NAME in (arbitraryphp/extinitial/pre_request.h). Parameter can be find on attached picture.