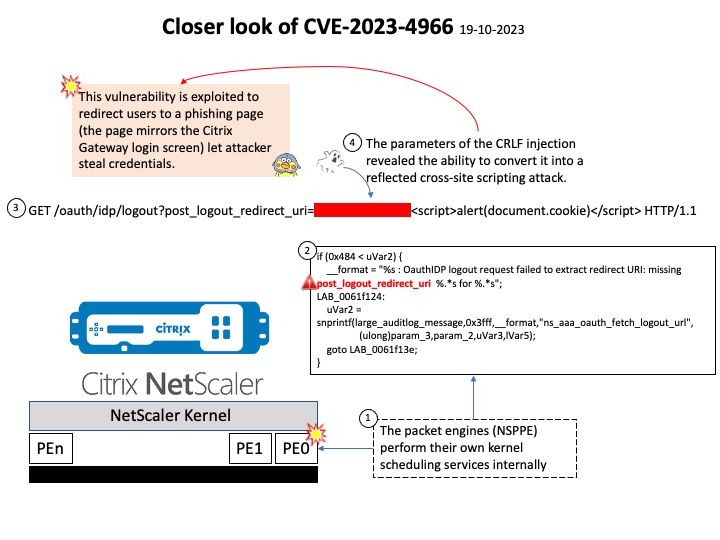
Preface: On October 10, 2023, Citrix released a security advisory regarding a sensitive information disclosure vulnerability (CVE-2023-4966) affecting NetScaler ADC and NetScaler Gateway appliances.
Background: Citrix NetScaler improves performance by using HTTP compression and data caching. The workload is shared over multiple servers and networks to ensure that there is not one point of failure or that one server is not overloaded, causing a slow or inefficient performance.
The Citrix ADC (formerly NetScaler) appliance instantiates the number of PEs based on the number of vCPUs, memory, and licenses.
The packet engine is created to perform TCP/IP processing, optimization tasks and acceleration of packages. This is a continues process of grabbing packets, handling them accordingly and putting the packets in place again, the packet engine is designed to run an entire instance of NetScaler’s packet engine on each processor core (nCore technology) and runs as a kernel component on the NetScaler.
Vulnerability details: Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
Official announcement: Please refer to the link for details –