Preface: If you still remember more than ten years ago, a snowhttp attack target web server especially Apache web server. Slow HTTP attacks are denial-of-service (DoS) attacks in which the attacker sends HTTP requests piece by piece at a slow pace to a web server. If an HTTP request is not complete, or if the transfer rate is very low, the server keeps its resources busy waiting for the rest of the data.
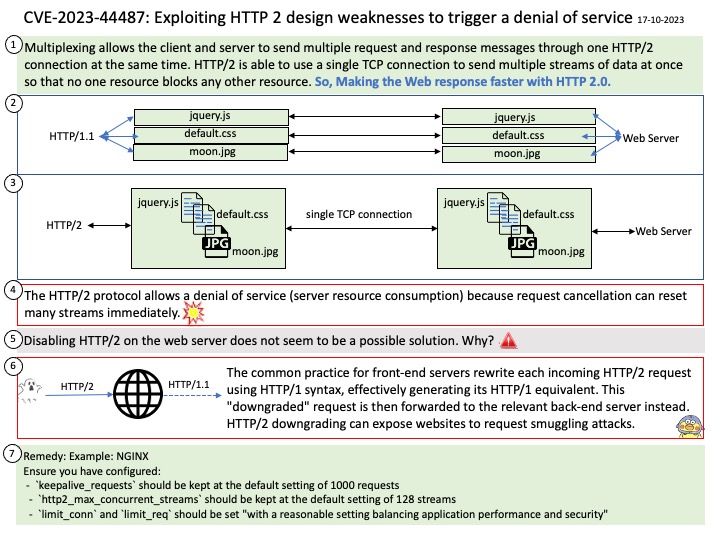
Background: HTTP 2.0 uses a binary, length-prefixed framing layer, which offers more compact representation than the newline-delimited plaintext HTTP 1.x protocol and is both easier and more efficient to process.
HTTP/2 makes web pages load faster and more efficiently by simplifying communication between the browser and the server. Accessing a website using the HTTP/2 protocol is as follows: the browser requests a TCP connection. The server establishes a TCP connection. The browser requests the website’s index HTML file.
Vulnerability details: The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
Additional: Because of CVE-2023-44487, HTTP/2 enabled web servers are vulnerable to a DDoS attack. It so called “Rapid Reset Attack”.
The HTTP/2 protocol allows clients to indicate to the server that a previous stream should be canceled by sending a RST_STREAM frame. The protocol does not require the client and server to coordinate the cancellation in any way, the client may do it unilaterally.
The ability for an endpoint to send a RST_STREAM frame immediately after sending a request frame, which makes the other endpoint start working and then rapidly resets the request. The request is canceled, but leaves the HTTP/2 connection open. As a result, the server keeps its resources in heavy load status.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-44487