Preface: Quick comparison of Windows (IoRing) and Linux (io_uring):
Windows: The kernel fully initializes the new ring, including the creation of both queues and creating a shared view in the application’s user-mode address space, using an MDL (memory descriptor list).
Linux: In the Linux io_uring implementation, the system creates the requested ring and the queues but does not map them into user space. The application is expected to call mmap(2) using the appropriate file descriptors to map both queues into its address space, as well as the SQE array, which is separate from the main queue.
Background: A potential performance benefit of io_uring for network I/O is reducing the number of syscalls.
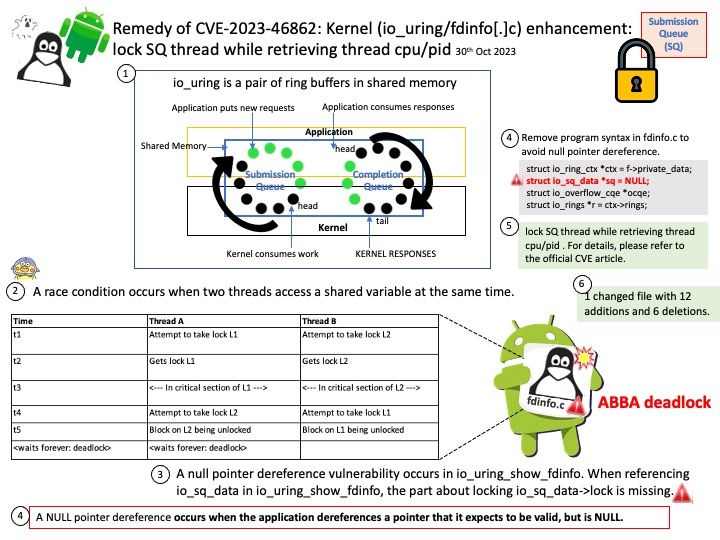
Vulnerability details: An issue was discovered in the Linux kernel through 6.5.9. During a race with SQ thread exit, an io_uring/fdinfo[.]c io_uring_show_fdinfo NULL pointer dereference can occur.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-46862
Observation: Most null pointer issues result in general software reliability problems, but if an attacker can intentionally trigger a null pointer dereference, the attacker might be able to use the resulting exception to bypass security logic.
Many io_uring features are available in Red Hat Enterprise Linux 9.3, which is distributed with kernel version 5.14.
Since the CVSS score has not yet been defined. But we know the vulnerability will occur during a proof-of-concept exercise. Maybe, a local attack (rather than a remote attack). But we should fix this design flaw immediately.