Preface: You can configure the nginx ingress controller in various ways. To use the Openstack load balancer Octavia with ssl offloading you will need to configure the ingress controller with the proxy protocol. The alternative would be to use the Openstack service barbican to store your ssl certificate. Which is currently not directly supported by Kubernetes.
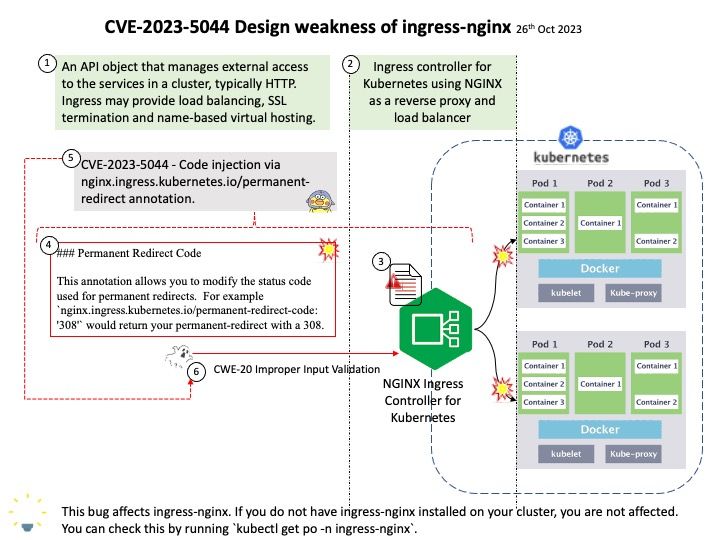
Background: The Ingress exposes HTTP and HTTPS routes from outside the cluster to services within the cluster. Traffic routing is controlled by rules defined on the Ingress resource. An Ingress may be configured to give Services externally-reachable URLs, load balance traffic, terminate SSL / TLS, and offer name-based virtual hosting.
Vulnerability details: A security issue was identified in ingress-nginx where the nginx[.]ingress[.]Kubernetes[.]io/permanent-redirect annotation on an Ingress object (in the networking[.]k8s[.]io or extensions API group) can be used to inject arbitrary commands, and obtain the credentials of the ingress-nginx controller. In the default configuration, that credential has access to all secrets in the cluster.
Affected Versions : <v1.9.0
Versions allowing mitigation: v1.9.0
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-5044