Preface: Public Key Infrastructure is the proven solution for authentication, encryption and data integrity. DigiCert PKI solutions are built on trust. Public trust. Private trust. And the world’s most trusted roots. XenMobile Server GPKI support includes DigiCert Managed PKI, also referred to as MPKI.
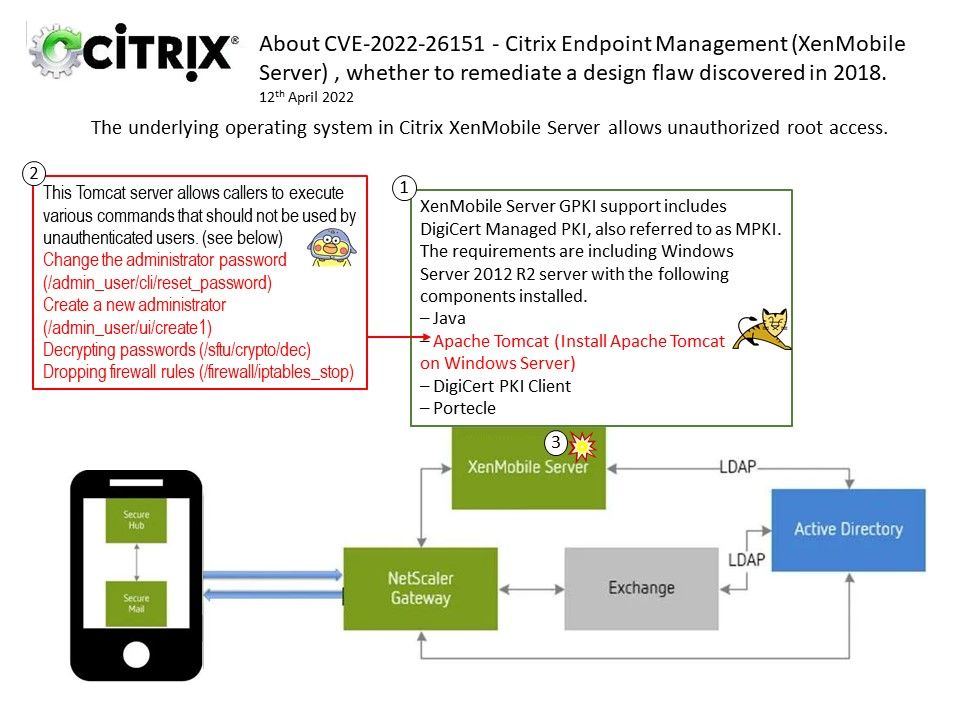
Background: XenMobile Server GPKI support includes DigiCert Managed PKI, also referred to as MPKI. The requirements are including Windows Server 2012 R2 server with the following components installed.
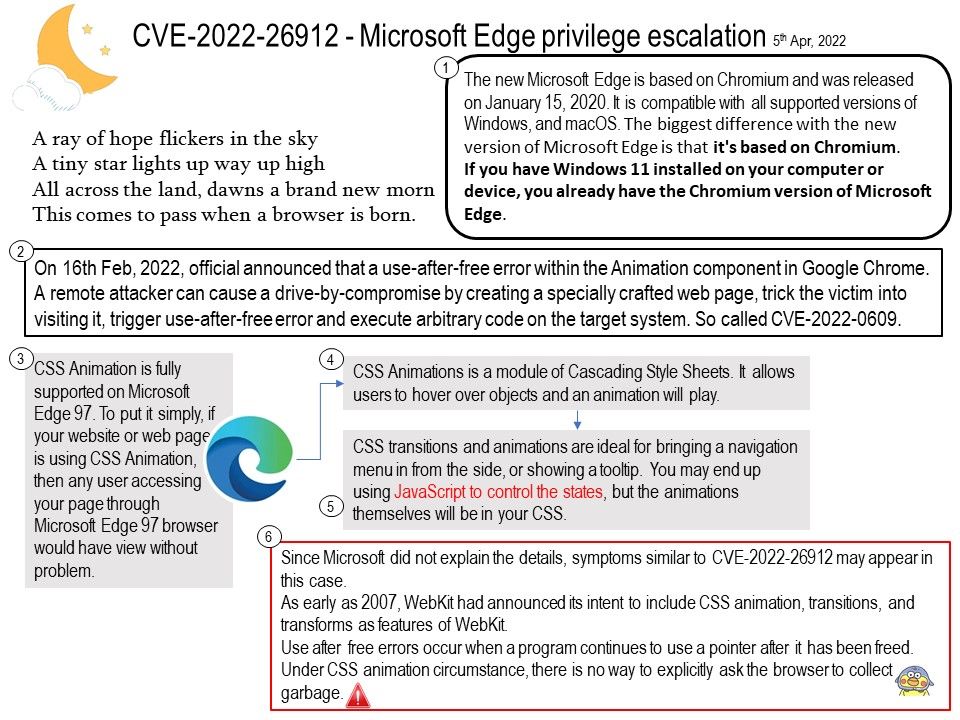
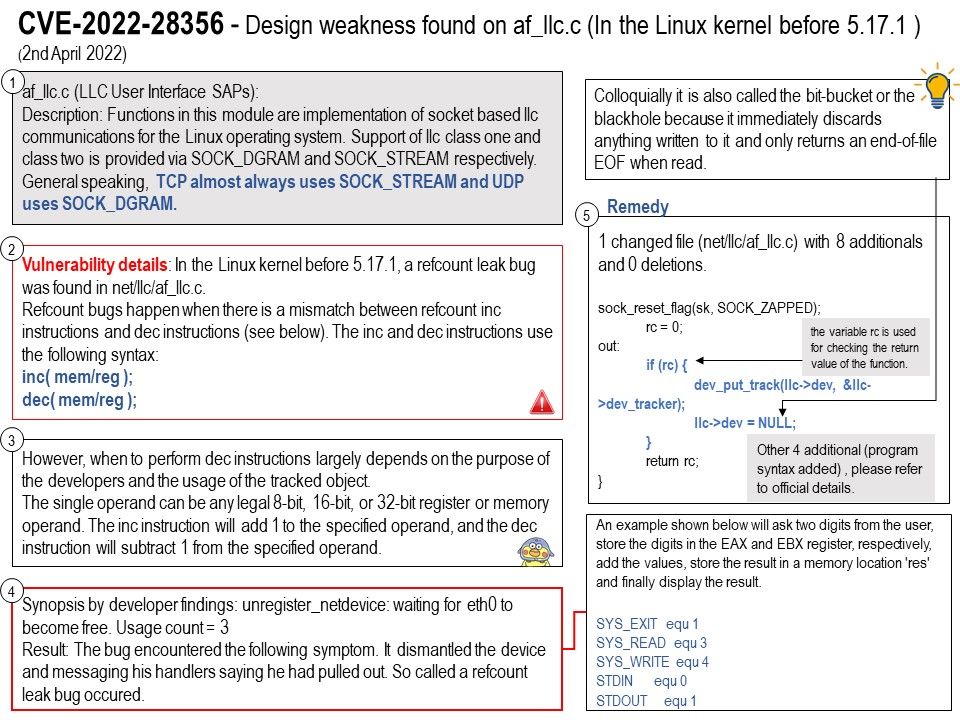
– Java
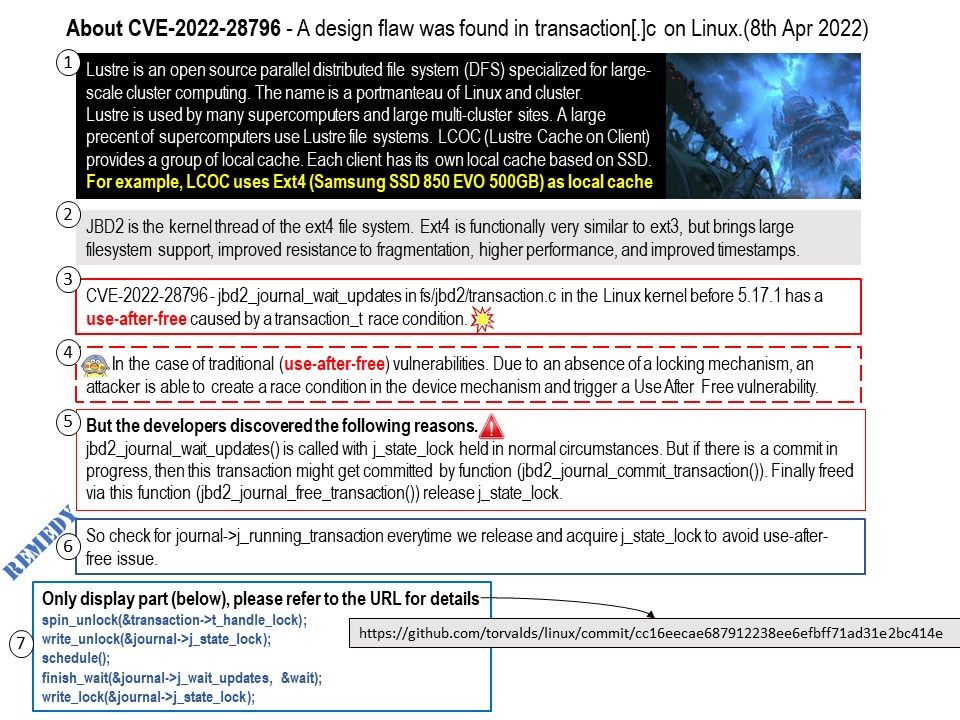
– Apache Tomcat (Install Apache Tomcat on Windows Server)
– DigiCert PKI Client
– Portecle
Vulnerability details: CVE-2022-26151 – The underlying operating system in Citrix XenMobile Server allows unauthorized root access. For official announcement of details, please refer to Citrix Endpoint Management (XenMobile Server) Security Bulletin for CVE-2021-44519, CVE-2021-44520, and CVE-2022-26151. The url is shown as below:
https://support.citrix.com/article/CTX370551
| CVE-2022-26151 | Unauthorized root access to the underlying OS | CWE-20: Improper Input Validation | Admin access to XenMobile Server CLI |
Speculation: Vendor did not provide vulnerability details. But the problem can happen in the following area:
XenMobile server (that is, localhost).
This Tomcat server allows callers to execute a variety of commands that should not be available to unauthenticated users. For example:
- Change the administrator password (/admin_user/cli/reset_password)
- Create a new administrator (/admin_user/ui/create1)
- Decrypting passwords (/sftu/crypto/dec)
- Dropping firewall rules (/firewall/iptables_stop)
Workaround: Mitigated by the internal firewall that limits access to configuration services to localhost.
Remedy:
CVE-2021-44519, CVE-2021-44520 – Medium severity:
XenMobile Server 10.14.0 rolling patch 4 and later releases of 10.14.0
XenMobile Server 10.13.0 rolling patch 7 and later releases of 10.13.0
CVE-2022-26151 – Low severity:
XenMobile Server 10.14.0 rolling patch 5 and later releases of 10.14.0
XenMobile Server 10.13.0 rolling patch 8 and later releases of 10.13.0
.jpg)