Preface: President Biden’s Executive Order is modernizing the Federal Government defenses and improving the security of widely-used technology. On March 2022, he urged U.S. companies operating critical infrastructure, including in the energy sector, to harden their digital defenses.
Background: CODESYS, formerly known as CoDeSys, is an acronym for Controller Development System, an Integrated Development Environment for Programmable Logic Controller applications, compliant with the IEC 61131-3 standard, a hardware and manufacturer-independent integrated development environment . IEC 61131-3:2013 specifies the syntax and semantics of a unified suite of programming languages for programmable controllers (PCs).The product CODESYS Control RTE SL is a real-time software PLC for PC-based industrial controllers under Windows. The CODESYS Control RTE SL product is a real-time soft PLC used to develop industrial controllers under the Windows operating system on the PC side. The runtime system has its own real-time kernel: in the absence of other hardware components or OS extensions, the system jitter value can remain in the μs range.
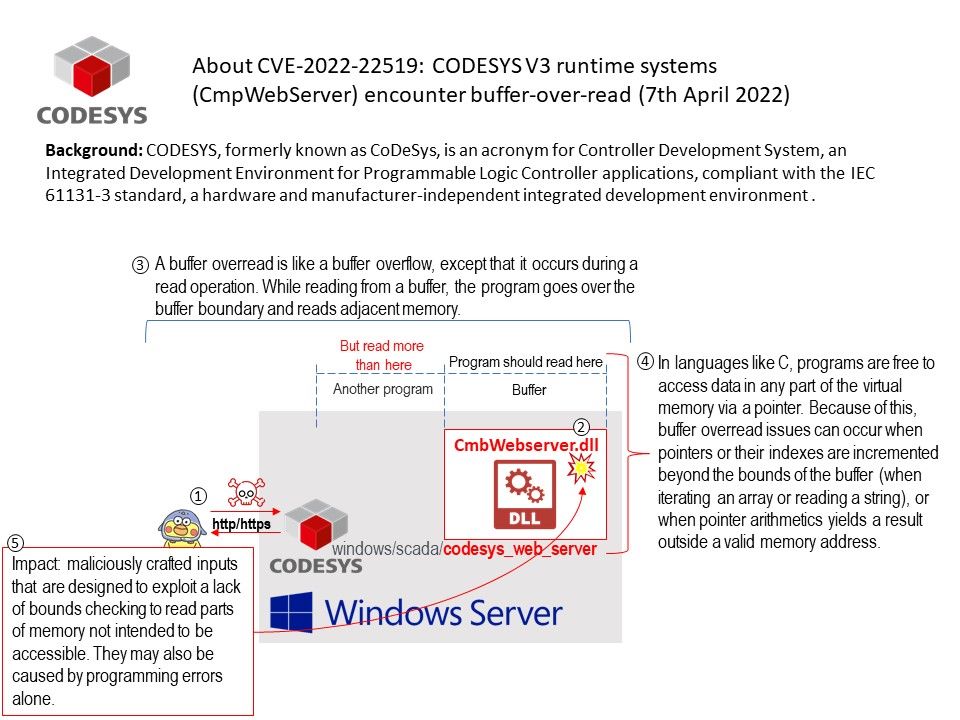
Vulnerability details: A remote, authenticated attacker can send a specific crafted HTTP or HTTPS requests causing CODESYS V3 runtime systems (CmpWebServer) encounter buffer-over-read.
A buffer overread is like a buffer overflow, except that it occurs during a read operation. While reading from a buffer, the program goes over the buffer boundary and reads adjacent memory.
In languages like C, programs are free to access data in any part of the virtual memory via a pointer. Because of this, buffer overread issues can occur when pointers or their indexes are incremented beyond the bounds of the buffer (when iterating an array or reading a string), or when pointer arithmetics yields a result outside a valid memory address.
Impact: maliciously crafted inputs that are designed to exploit a lack of bounds checking to read parts of memory not intended to be accessible. They may also be caused by programming errors alone.
Official announcement: For details, please refer to the link – https://customers.codesys.com/index.php?eID=dumpFile&t=f&f=17094&token=2fb188e2213c74194e81ba61ff99f1c68602ba4d&download=