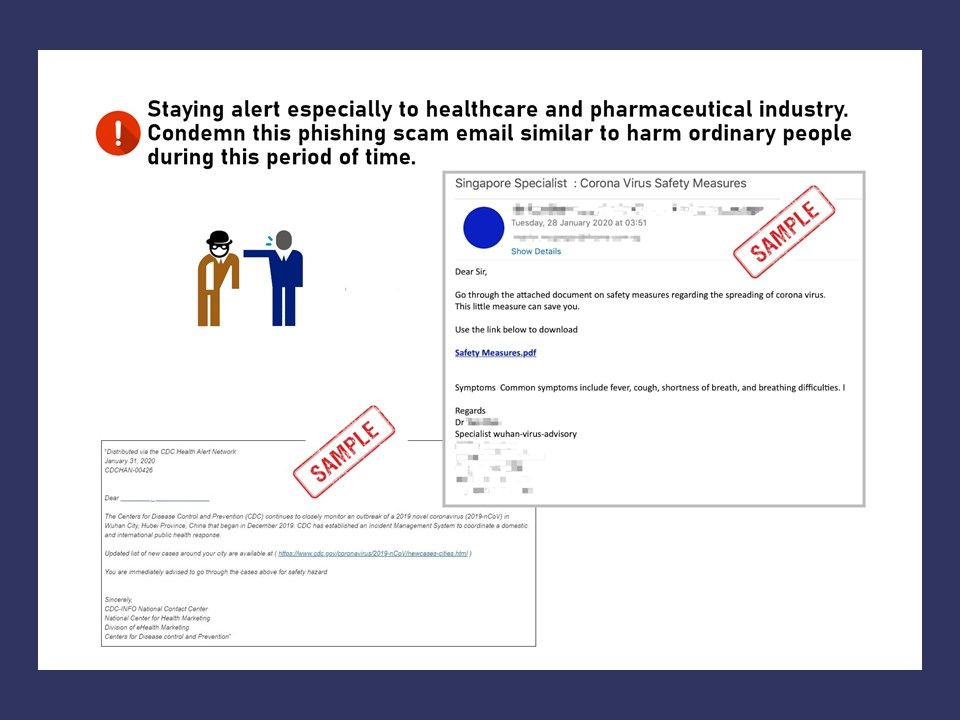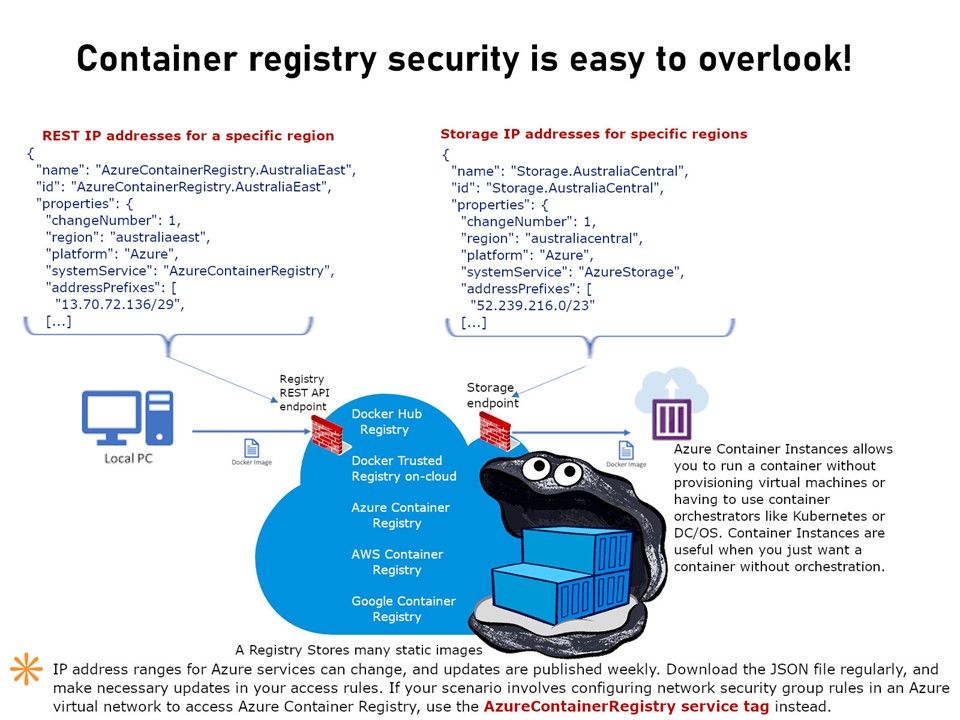
Preface: Sysadmin may unintentionally expose a Docker registry service without enforcing proper access control, said Palo Alto Networks.
Background: Easy to deploy, one of the goal of container-based technology. Docker storing image in a managed collection, with standardized methods of identifying, committing, and pulling individual images. With this feature it is equivalent as a image Repositories. It makes Docker so useful is how easy it is to pull ready-to-use images from a Docker’s Central Registry. Meanwhile you can’t share your repository with other because it contains proprietary code or confidential information.
Technical details: Docker-Registry is a simple Python app. Your Registry can develop as a Private Registries. Besides, in some environments, sysadmin can setup the Registry SRV on port 443 and make it accessible on internet (Registry-dot-com). Such services are popular on AWS S3 or Azure.
Key areas of concern: Compromised Containers, mis-configuration & access control.
What we can do? Perhaps we can reference to NIST SP 800-190 application container security guide. URL display as below: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-190.pdf