Preface: Heap overflows are exploitable in a different manner to that of stack-based overflows. Memory on the heap is dynamically allocated at runtime and typically contains program data.
Product background: F-Secure Internet Gatekeeper for Linux, aim to serve for small and medium business cyber security protection services. It capable to scanning incoming and outgoing including SMTP, HTTP, FTP and POP3 traffic for all types of malware.
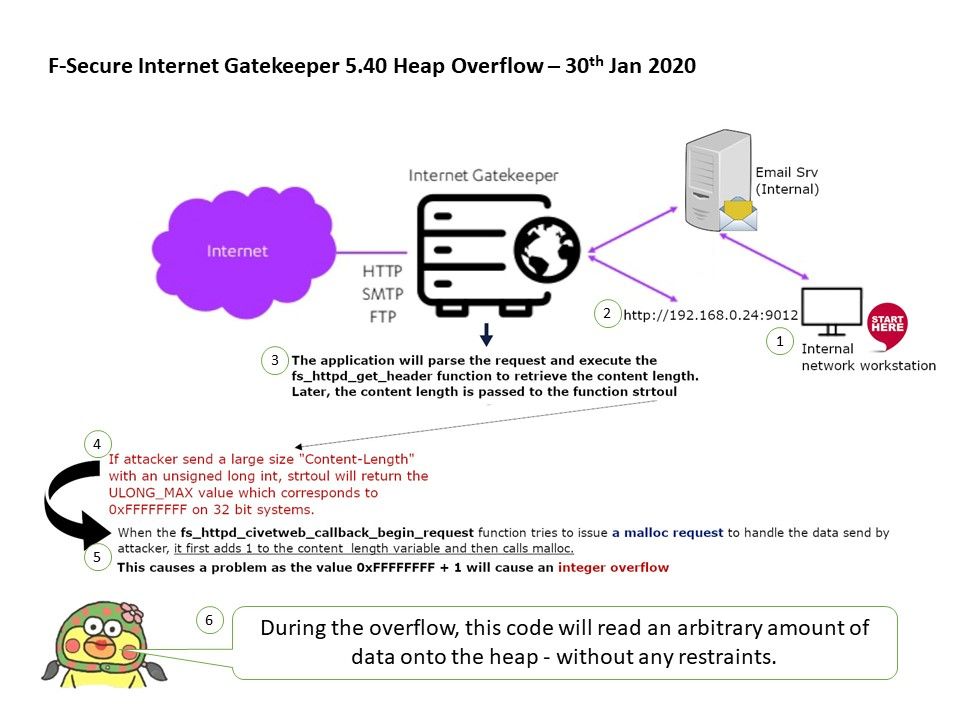
Vulnerability details: F-Secure Internet Gatekeeper contains an admin panel that runs on port 9012/tcp. If attacker send a large size “Content-Length” with an unsigned long int through user administration process.
It will causes strtoul return the ULONG_MAX value which corresponds to 0xFFFFFFFF on 32 bit systems.
Adopt to above circumstances, when the fs_httpd_civetweb_callback_begin_request function tries to issue a malloc request to handle the data send by attacker, it first adds 1 to the content_length variable and then calls malloc. This causes a problem as the value 0xFFFFFFFF + 1 will cause an integer overflow. During the overflow, this code will read an arbitrary amount of data onto the heap – without any restraints.
Remedy: This critical issue was tracked as FSC-2019-3 and fixed in F-Secure Internet Gatekeeper versions 5.40 – 5.50 hotfix 8 (2019-07-11).