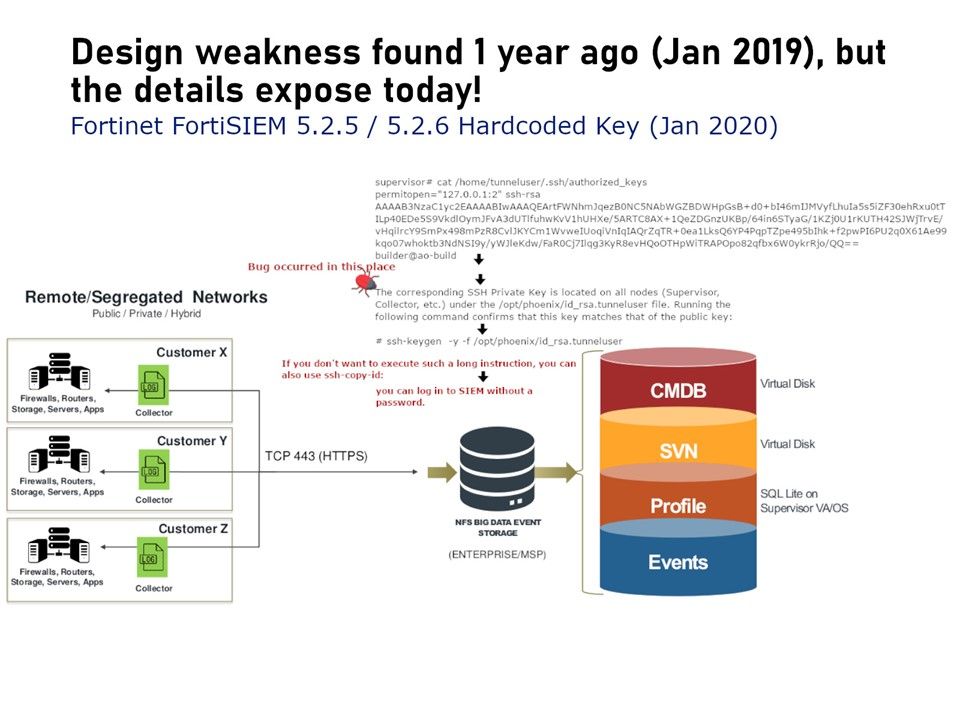
Preface: Stupid Solutions to Stupid Problems: Hardcoding Your SSH Key in the system.
Vulnerability background: FortiSIEM 5.2.5 / 5.2.6 could use the hardcoded password to log in to the underlying system via Secure Shell (SSH). This means that anyone with access to any FortiSIEM image (to copy the SSH private key) can authenticate successfully via SSH to the FortiSIEM. Supervisor on port 19999/tcp as tunneluser. They will be limited to the /opt/phoenix/phscripts/bin/tunnelshell script, but if this is bypassed then full shell access can be obtained.
Impact: While the user’s shell is limited to running the /opt/phoenix/phscripts/bin/tunnelshell script, SSH authentication still succeeds. Versions 5.2.5 and 5.2.6 have been verified as vulnerable.