Preface: Microsoft products cover a wide range. Perhaps quite a lot of people queries design weakness of their products. But they have capabilities to protect it own.
Background: The cyber criminal exploit Microsoft official domain name to made phishing email and goal to increase the possibility to open the email. Meanwhile the malicious infection technique has proprietary evading antivirus technique.
Remark: According to my observation, the evolution of this cyber attack technique found in 2013. Perhaps we remember HWP (Hangul Word Processor). HWP files are similar to MS Word’s DOCX files, except that they can contain Korean written language, making it one of the standard document formats used by the South Korean government. Should you have interested to review the details, plese refer to following URL: http://www.antihackingonline.com/network-protocol-topology-standard/vulnerabilities-in-the-old-ole2-based-hwp-file-format-engages-apt-attacks-to-south-korea/
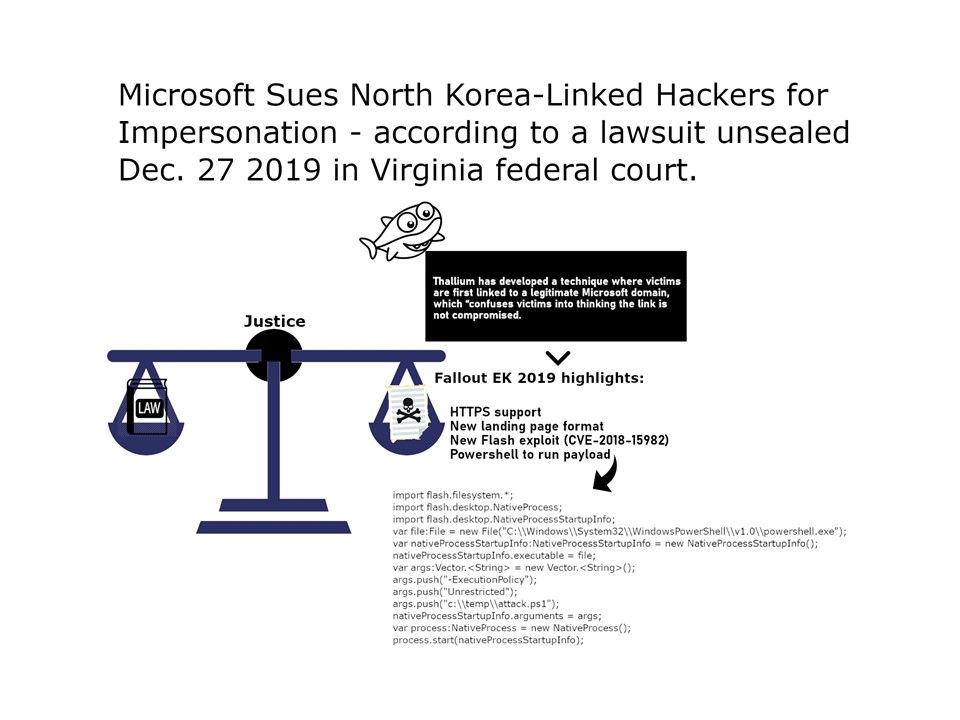
Cyber security focus: Such matter reminds cybersecurity world of cyber criminal infiltration technique. Expert found that the North Korea cyber attack suspect make a new way. Attack mainly using the API hooking technique to hide the behaviors of the first-stage backdoor which is the second payload in this operation. Since this attack landing page most likely is a MS document. The Fallout Exploit Kit is Back with adobe Vulnerabilities and Payloads (see attached diagram) So, it generate a interference to business and government sector.
Reference: Microsoft Sues North Korea-Linked Hackers for Impersonation (1) – https://news.bloomberglaw.com/ip-law/microsoft-sues-north-korea-linked-hackers-for-targeting-users