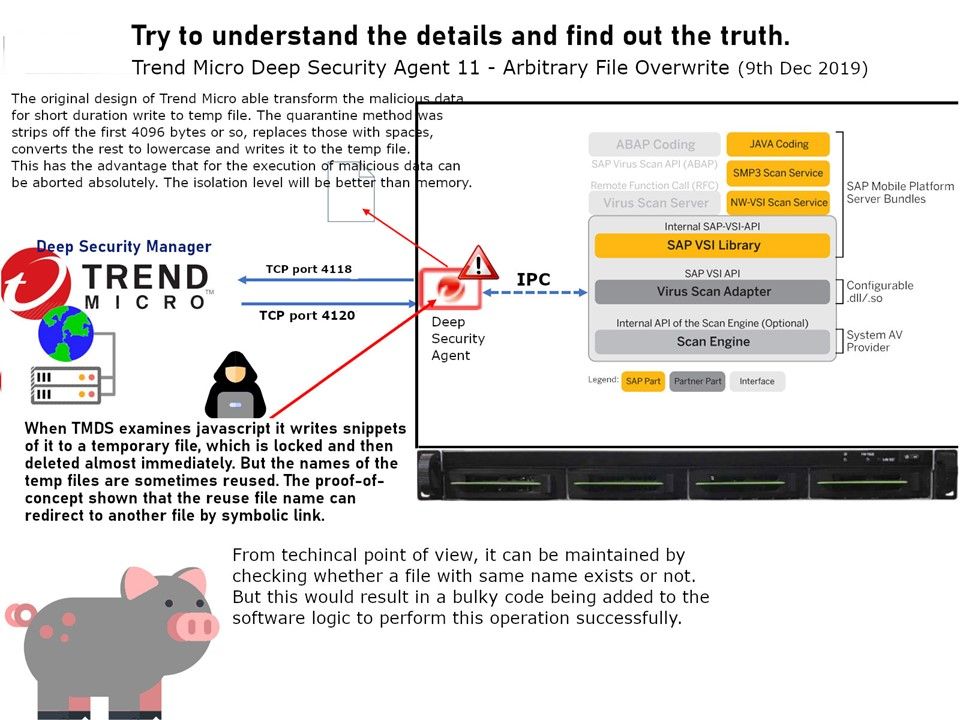
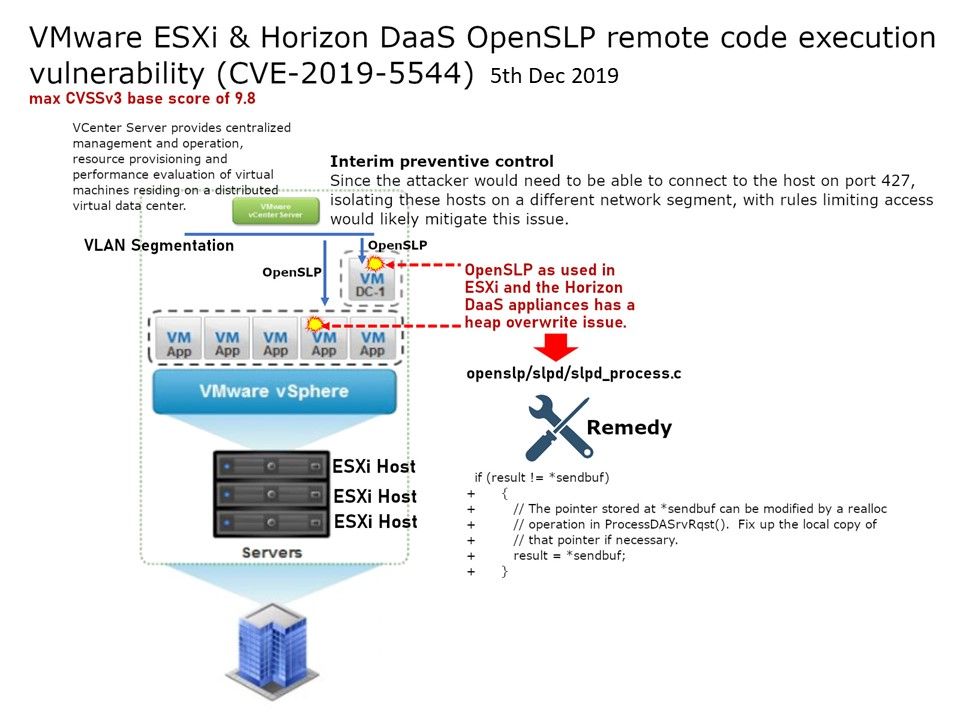
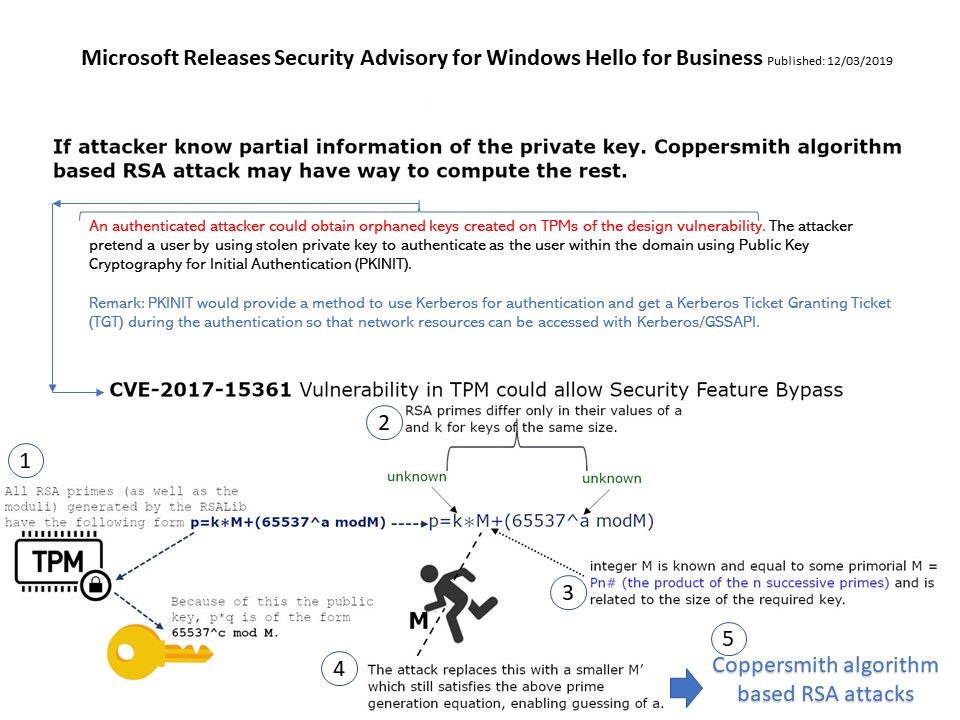
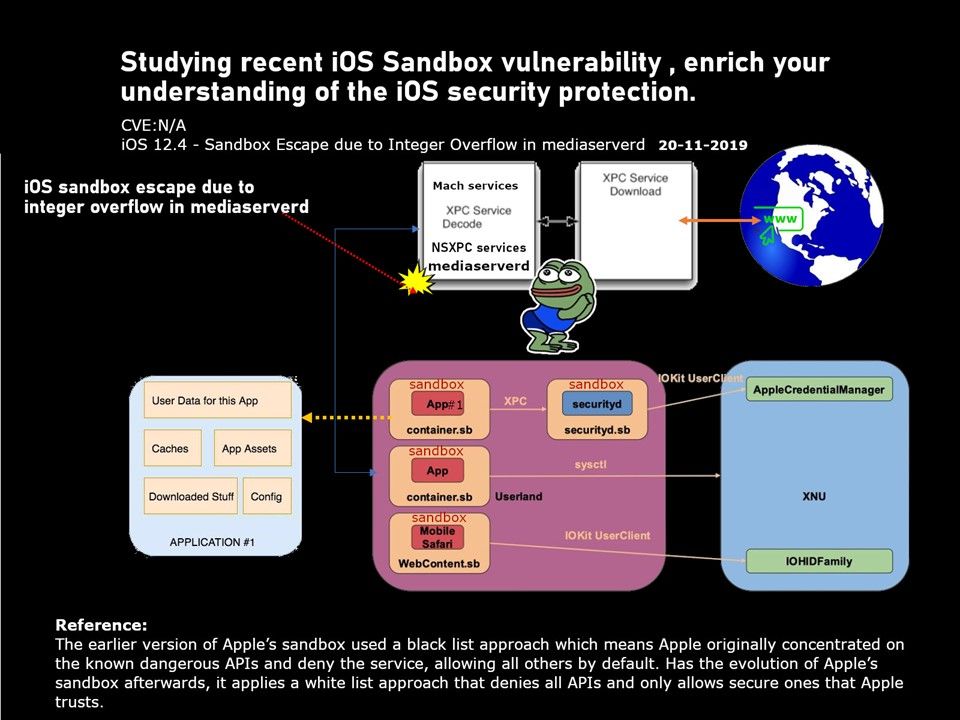
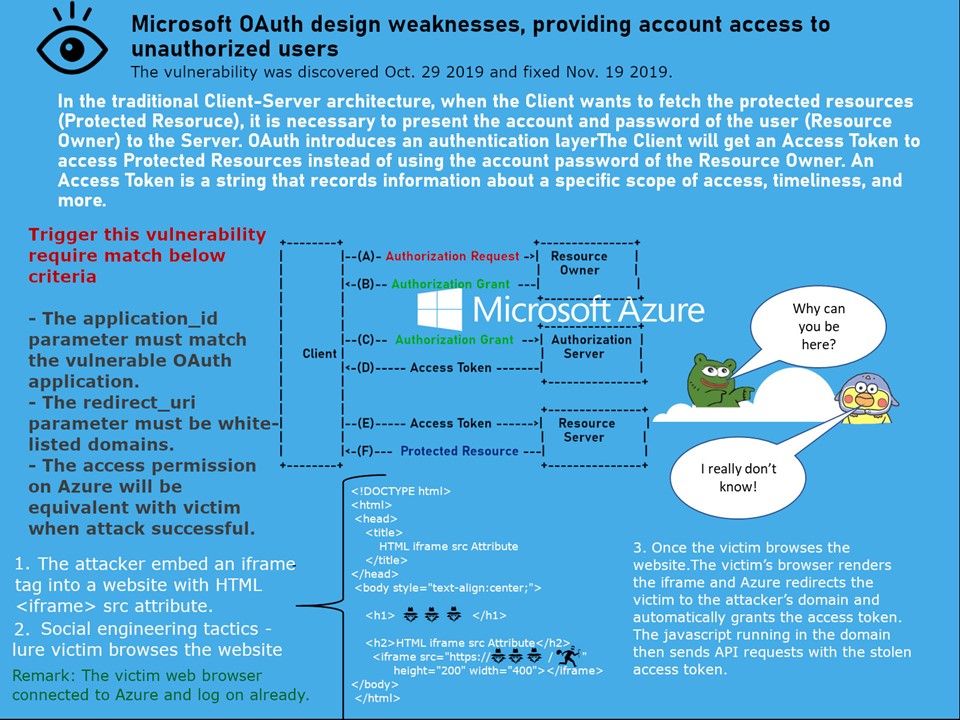
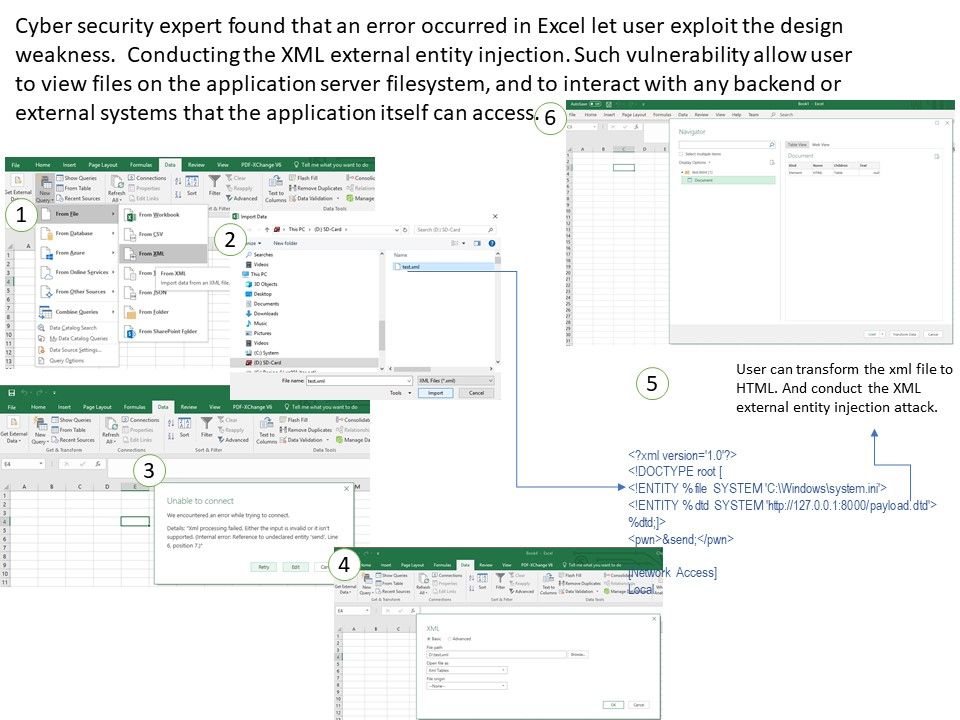
Preface: When Meltdown and Spectre discovered, the tech community questioned chip security.
Security Focus: A new class of unprivileged speculative execution attacks to leak arbitrary data across address spaces and privilege boundaries (e.g., process, kernel, SGX, and even CPU-internal operations). Who is he?
Side-channel attack targeting Intel chips, allowing hackers to effectively exploit design flaws rather than injecting malicious code. For instance, hacker can use WebAssembly in both Firefox and Chrome to generate machine code which he can use to perform this attacks. If you are interested in learning more, please refer to the attached picture.
Intel has released security updates to address vulnerability in multiple products. The official announcement can be found at this link – https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00317.html
HP urge the customer that it should be acted upon as soon as possible. The “HP Security Update” can be found at this link – https://support.hp.com/us-en/document/c06502052