Preface: The OAuth 2.0 Authorization Framework (RFC 6749, October 2012)
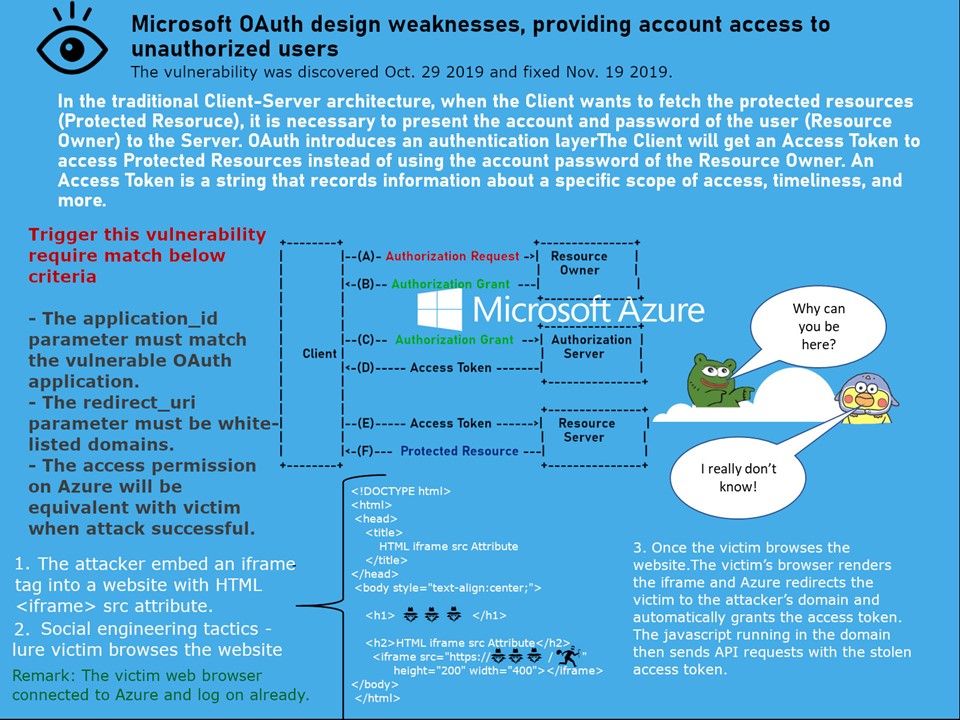
Technical background: In the traditional Client-Server architecture, when the Client wants to fetch the protected resources (Protected Resoruce), it is necessary to present the account and password of the user (Resource Owner) to the Server. OAuth introduces an authentication layerThe Client will get an Access Token to access Protected Resources instead of using the account password of the Resource Owner. An Access Token is a string that records information about a specific scope of access, timeliness, and more.
Vulnerability details: The details of the vulnerability shown on attached diagram. But the root cause of this design weakness perhaps not limited to CyberArk researchers discovery. Azure trust certain third-party domains and sub-domains. Can you imagine that the problem may be involved wildcard domain included in whitelist?
Focus: Heard that Microsoft didn’t issue a CVE because the bug is located only in their Online Service. Strange!
Nice blog here! Also your site loads up very fast! What host are you
using? Can I get your affiliate link to your host?
I wish my website loaded up as quickly as yours lol
I simply could not go away your website before suggesting that I actually loved the standard info a person provide in your
visitors? Is going to be again ceaselessly to inspect new
posts
Terrific work! That is the kind of info that are meant to be shared around the net.
Shame on Google for no longer positioning this post higher!
Come on over and consult with my website . Thanks =)
For newest news you have to go to see world-wide-web and on web I found this web page as a most excellent web page for hottest updates.