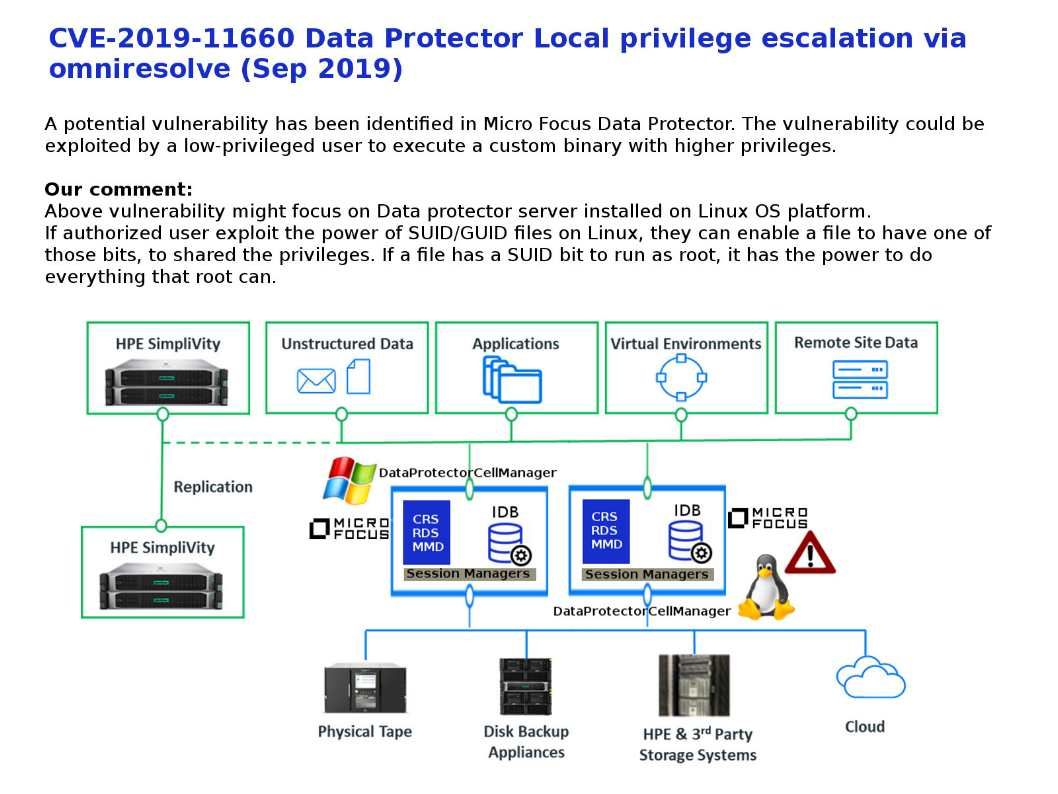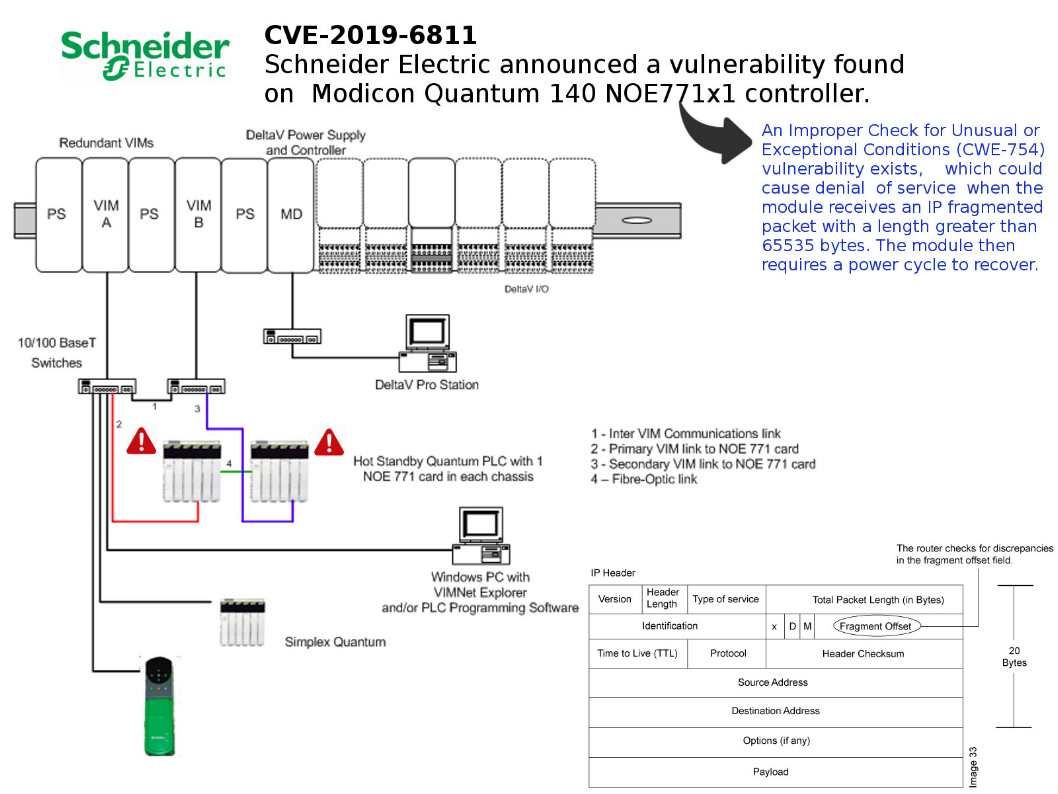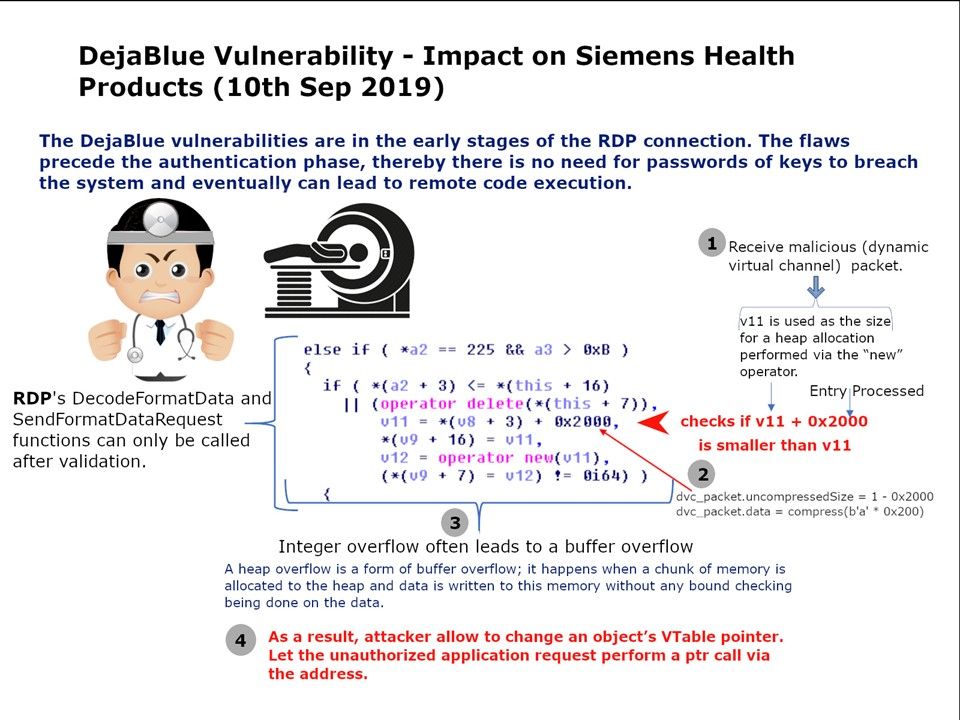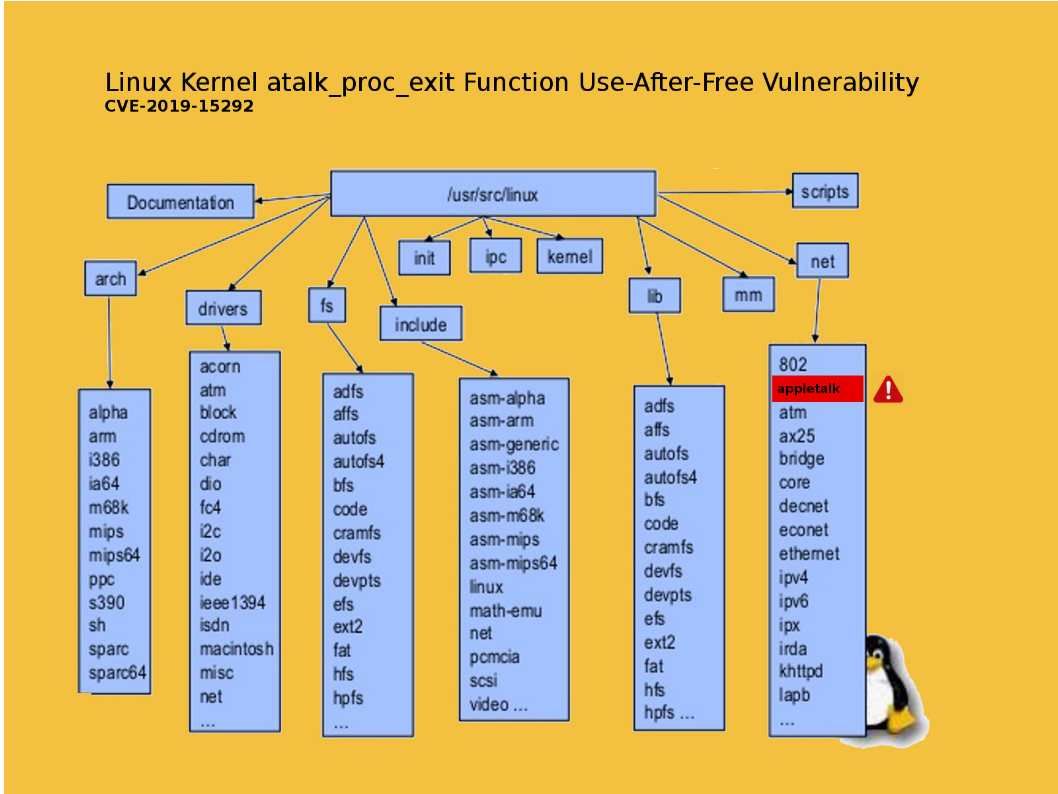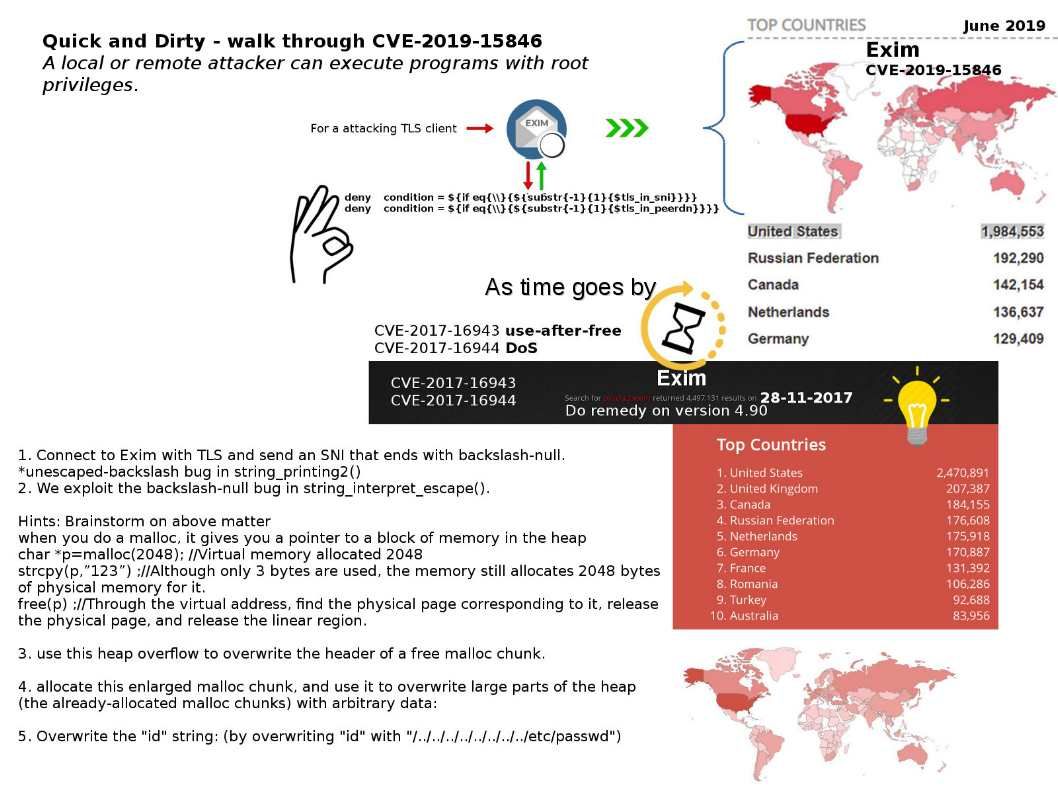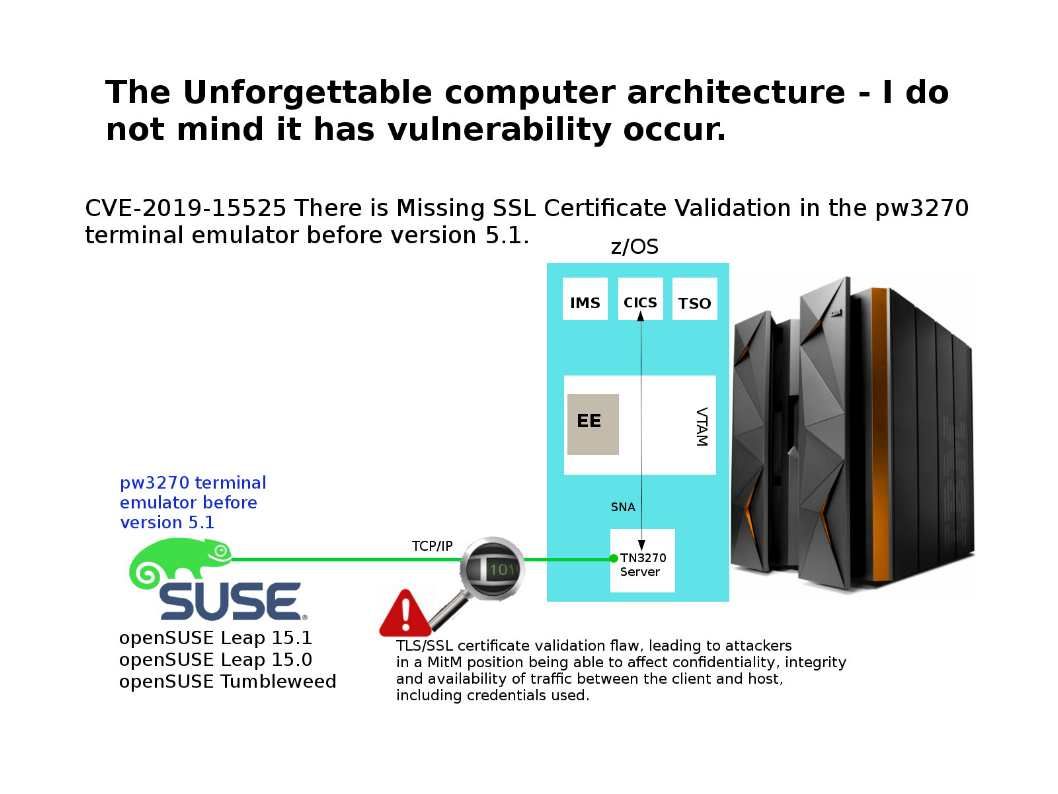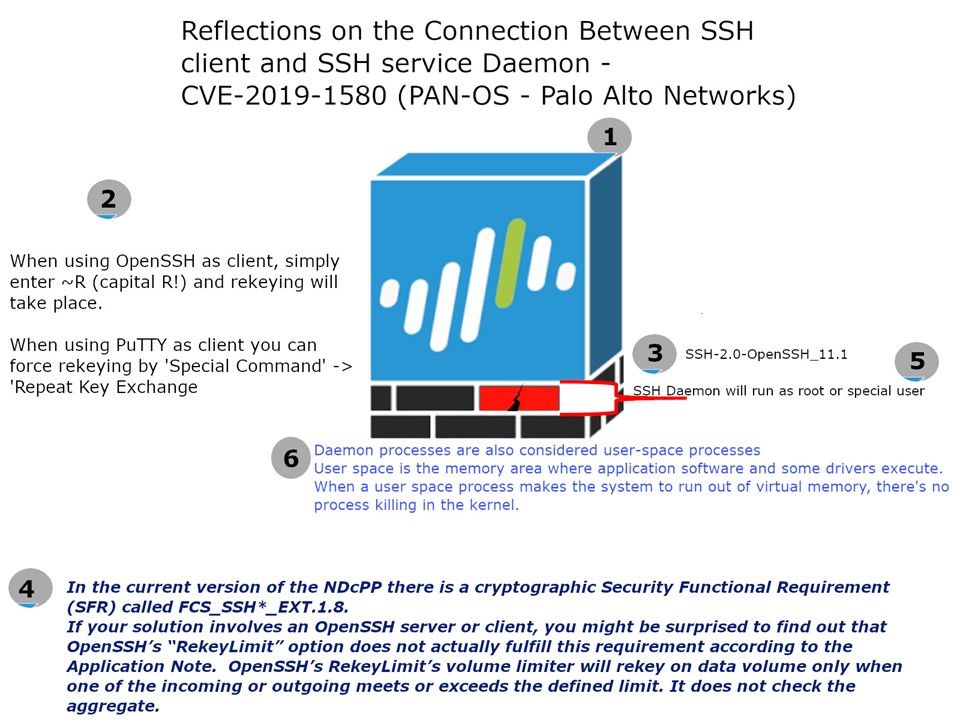
Preface: Traditionally, only big country can have military weapon. Computer technology especially IoT devices not only replace human power. As we seen, IoT 4.0 is going to replace routine man power resources. Perhaps IoT technology also infiltrate in military arsenal .
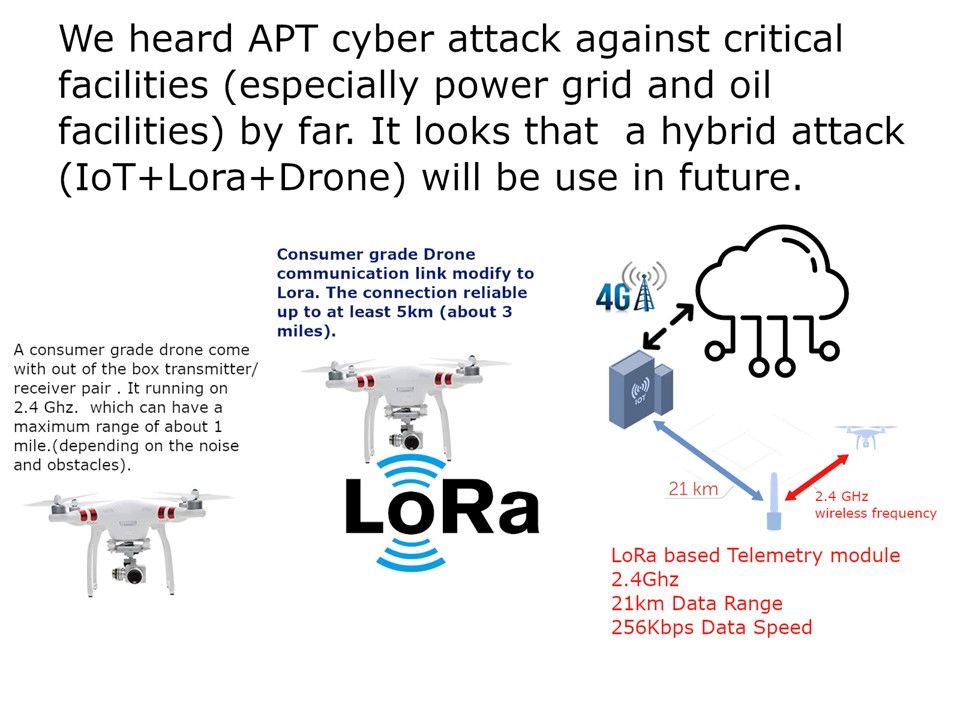
Details: On Sep, 2019. Drone attacks have set alight two major oil facilities run by the state-owned company Aramco in Saudi Arabia. Refer to diagram, Drone integrate with Lora can increasing the control effective distance. If trouble maker is going to attack improtant facilties, they have more choices today. In last decade, APT cyber attack is the major channel to detroy the critical facilities. But APT attack rare to destroy the infrastructure. If enemy insists to destory the infrastructure. The setup of IoT, Lora and Drone can do it.
Can Drones be Detected by Radar? All newer radars are equipped and have the ability to locate even the smallest drones in the air. May be in future, all the critical facilities especially oil facilitiy, Power grid require to install Radar system.
Prediction: We heard APT cyber attack against critical facilities (especially power grid and oil facilities) by far. It looks that a hybrid attack (IoT+Lora+Drone) will be use in future.