Preface: The SD-WAN is a specific application of software-defined networking (SDN) technology applied to WAN connections such as broadband internet, 4G, LTE, or MPLS.The technology deployment consists of QoS and network resiliance.
Product background: EdgeConnect has following features:
- Extend the micro-segmentation of specific application traffic from the data center to the entire WAN to help maintain security compliance requirements.
- Tunnel Bonding
- Identifying applications on the first packet is especially important when branches are deployed behind Network Address Translation (NAT); the correct path must be selected based on the first packet to avoid session interruption.
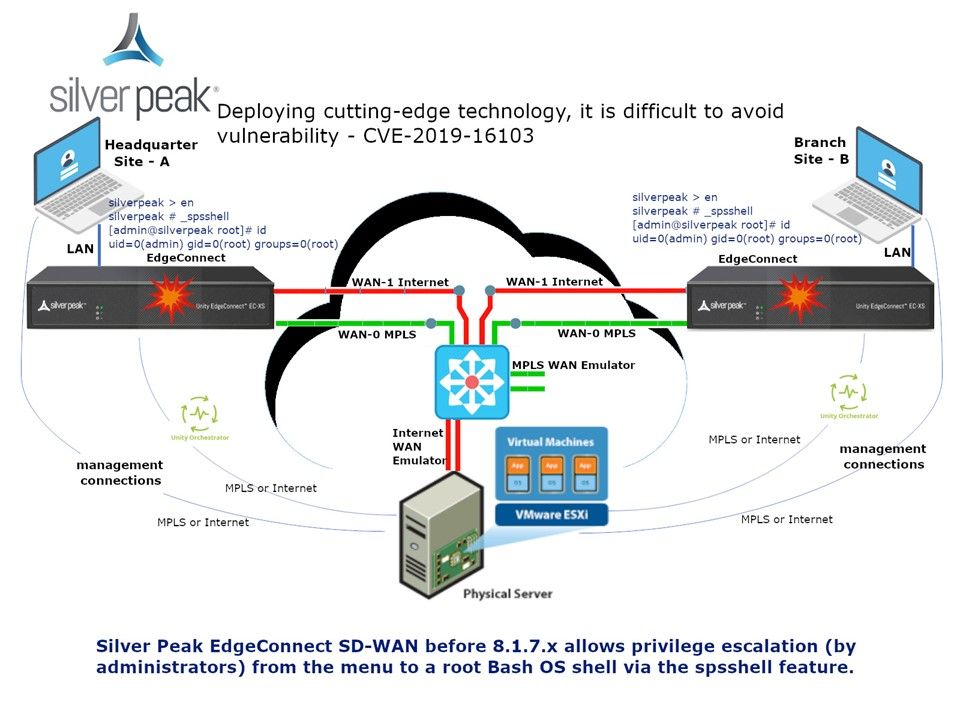
Vulnerability details: An administrative user with access to the enable menu of the login subshell may enter a hardcoded string to obtain a bash shell on the operation system. The spsadmin and admin accounts have root privileges. The system cli and web service works under root accounts which can be used for privilege escalation.
Observation: Perhaps this vulnerability might let people ignore. But do not contempt this issue because it shown that the user privileges not define well.
Remedy: Fixed in version 8.1.6.x – 8.1.7.x