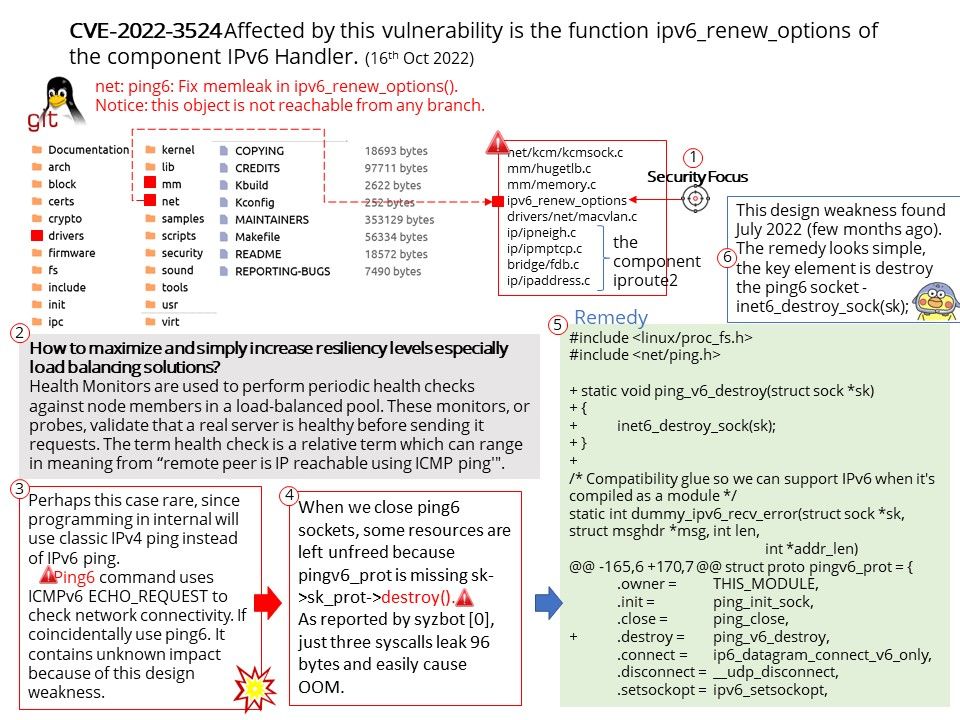
Preface: Ping6 command uses ICMPv6 ECHO_REQUEST to check network connectivity. This design weakness found July 2022 (few months ago). The remedy looks simple, the key element is destroy the ping6 socket – inet6_destroy_sock(sk);
Background: In computing, a system call (commonly abbreviated to syscall) is the programmatic way in which a computer program requests a service from the kernel of the operating system on which it is executed.
Since the ping command does ICMP. To find out the syscalls involved, you can strace that command (under root).
$ strace -e trace=network ping 127[.]0[.]0[.]1 -c 1 -4
During the process, you can see a bunch of setsockopt system calls, but they are all on the first socket that was created.
i.e. for IPPROTO_ICMP with the file descriptor, 3.
Finally, we have the call to, sendto and recvmsg system calls which are used to send the IP packet (with the ICMP packet embedded in it) to the destination host and then receive the reply from the destination host respectively.
Remark:The special aspect of file descriptor 3 is that it will usually be the first file descriptor returned from a system call that allocates a new file descriptor, given that 0, 1 and 2 are usually set up for stdin, stdout and stderr.
This means that if any library function you have called allocates a file descriptor for its own internal purposes in order to perform its functions, it will get fd 3.
Vulnerability details: A vulnerability was found in Linux Kernel. It has been declared as problematic. Affected by this vulnerability is the function ipv6_renew_options of the component IPv6 Handler. The manipulation leads to memory leak. The attack can be launched remotely. It is recommended to apply a patch to fix this issue. The identifier VDB-211021 was assigned to this vulnerability.
Remark: When we close ping6 sockets, some resources are left unfreed because pingv6_prot is missing sk->sk_prot->destroy().
As reported by syzbot [0], just three syscalls leak 96 bytes and easily cause OOM.
Technical details can be found at the following link – https://nvd.nist.gov/vuln/detail/CVE-2022-3524