Preface: BPF introduced two big innovations in packet filtering:
- A new virtual machine (VM) designed to work efficiently with register-based CPUs.
- The usage of per-application buffers that could filter packets without copying all the packet information. This minimized the amount of data BPF required to make decisions.
Background: BPF programs are designed to run in the linux kernel which is written in C, hence BPF defines instruction set compatible with two most used architectures x64 and arm64.
BPF allows a user-space program to attach a filter onto any socket and allow or disallow certain types of data to come through the socket. LSF follows exactly the same filter code structure as BSD’s BPF, so referring to the BSD bpf.4 manpage is very helpful in creating filters.
New generation of IoT security framework implements a packet filtering mechanism on the gateway side in order to mitigate DoS network attacks. The packet filtering module can cover all the networking stack layers, focusing on the Message Queuing Telemetry Transport (MQTT) / MQTT for Sensor Networks (MQTT-SN) and CoAP application layer protocols. The network filter layer consists of two sub-modules: the packet filter mechanism in the kernel side and the userspace filter component. The packet filtering on the kernel side will be implemented the Berkeley Packet Filter or Extended Berkeley Packet Filter (eBPF) technology.
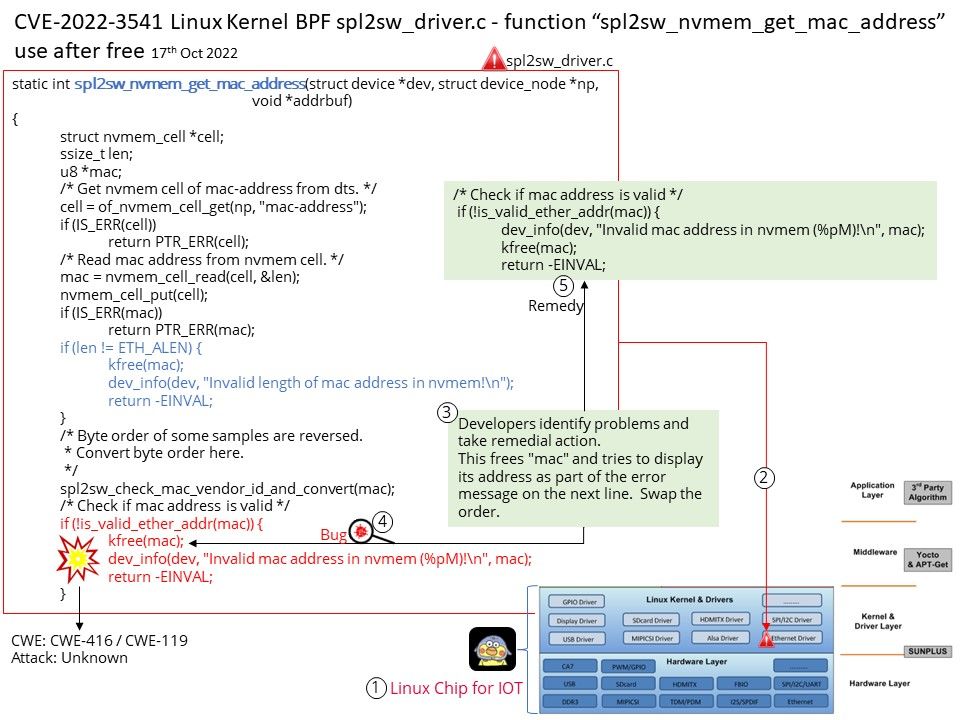
An SoC that has the power of a Linux-grade chip and the integration simplicity of a micro-controller. So called IoT Linux chips. CVE-2022-3541 has impact on IoT Linux chips and should be upgraded with firmware.
Vulnerability Details: CVE-2022-3541 A vulnerability classified as critical has been found in Linux Kernel. This affects the function spl2sw_nvmem_get_mac_address of the file drivers/net/ethernet/sunplus/spl2sw_driver[.]c of the component BPF. The manipulation leads to use after free. It is recommended to apply a patch to fix this issue.
For official announcement, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2022-3541