Preface: REST API has similar vulnerabilities as a web application. The possibilities will be from various threats, such as Man-in-the-Middle attacks, lack of XML encryptions, insecure endpoints, API URL parameters, ..etc.
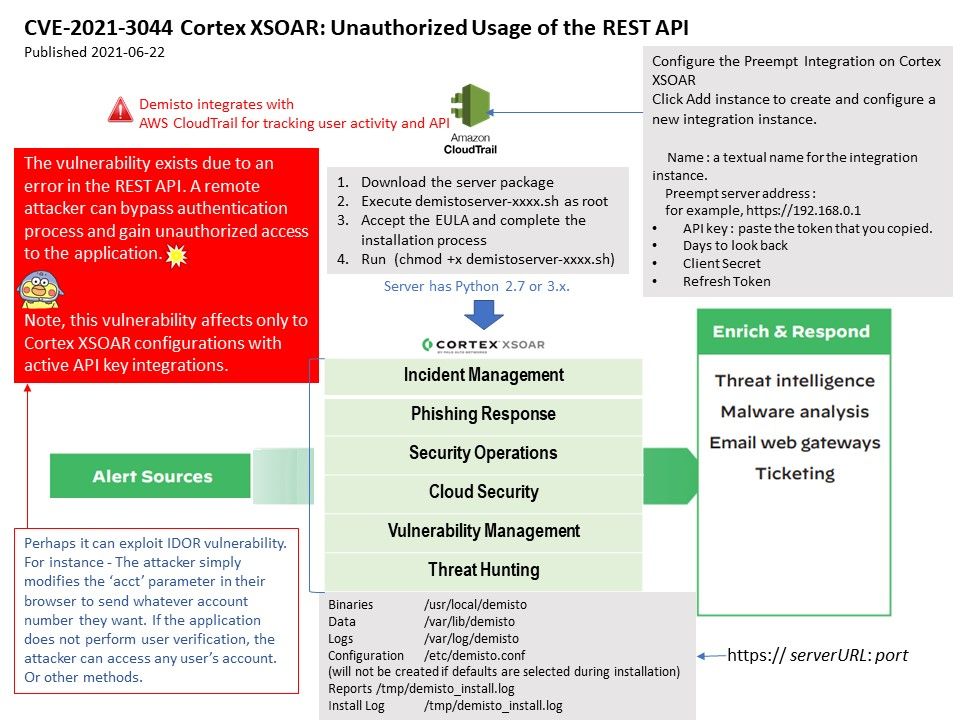
Technical background: Cortex XSOAR is the Security Orchestration, Automation and Response (SOAR) solution from Palo AltoNetworks. Cortex XSOAR (formerly Demisto) is able to configuration with active API Key integrations. In Cortex XSOAR Server, you can add Integration.
1. Go to Cortex XSOAR, then to Settings -> Integrations, search for iLert integration and click on the Add instance button.
2. On the modal window, name the instance, paste the iLert API Key that that you generated in iLert and click on the Save & exit button.
Vulnerability details: The vulnerability exists due to an error in the REST API. A remote attacker can bypass authentication process and gain unauthorized access to the application.
Note: This vulnerability affects only to Cortex XSOAR configurations with active API key integrations.
Ref: Perhaps it can exploit IDOR vulnerability. For instance – The attacker simply modifies the ‘acct’ parameter in their browser to send whatever account number they want. If the application does not perform user verification, the attacker can access any user’s account or other methods.
Official announcements and remedies – https://security.paloaltonetworks.com/CVE-2021-3044