Preface: Apache Solr is an application based on J2EE and uses Lucene libraries internally to provide user-friendly search as well as to generate the indexes.
Background: Apache Solr powers the search and navigation features of many of the world’s largest internet sites.
Vulnerability details: When an attacker can directly access the Solr console, he can make changes to the node’s configuration file by sending a POST request like /nodename/config.
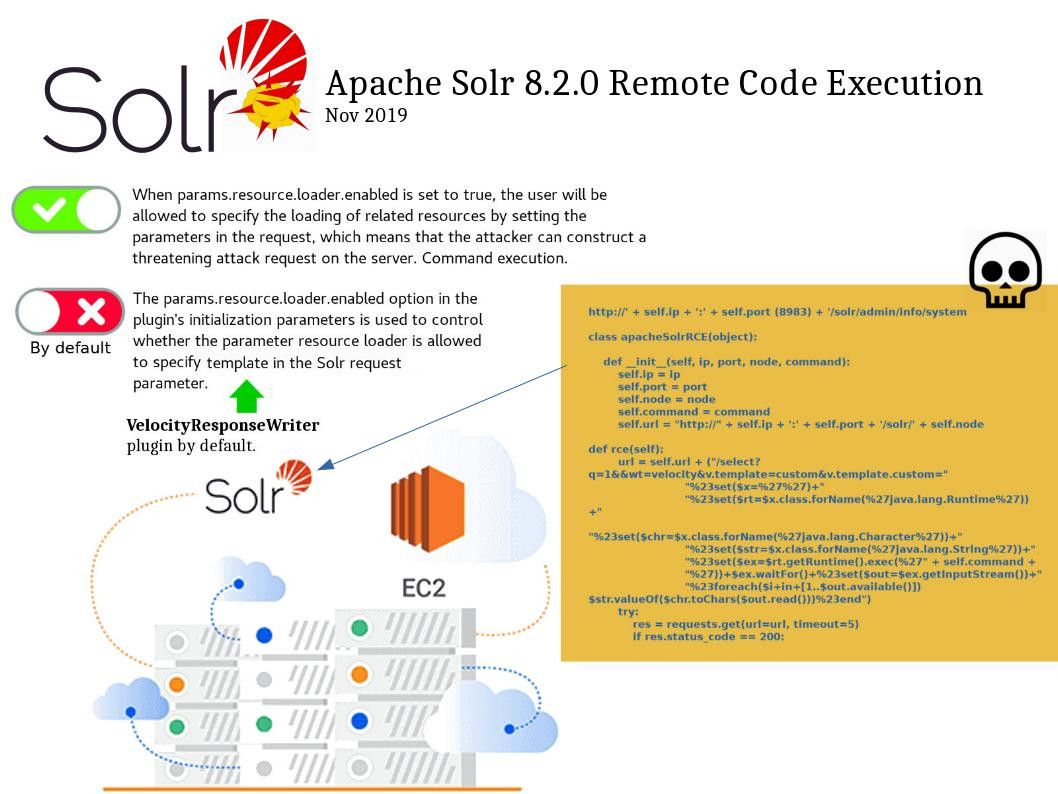
Apache Solr integrates the “VelocityResponseWriter” plugin by default. The “params.resource.loader.enabled” option in the plugin’s initialization parameters is used to control whether the parameter resource loader is allowed to specify template in the Solr request parameter. This option default setting is false. When “params.resource.loader.enabled” is set to true, the user will be allowed to specify the loading of related resources by setting the parameters in the request, which means that the attacker can construct a threatening attack request on the server. A remote code execution will be occurred.
Current status: waiting for CVE reference number