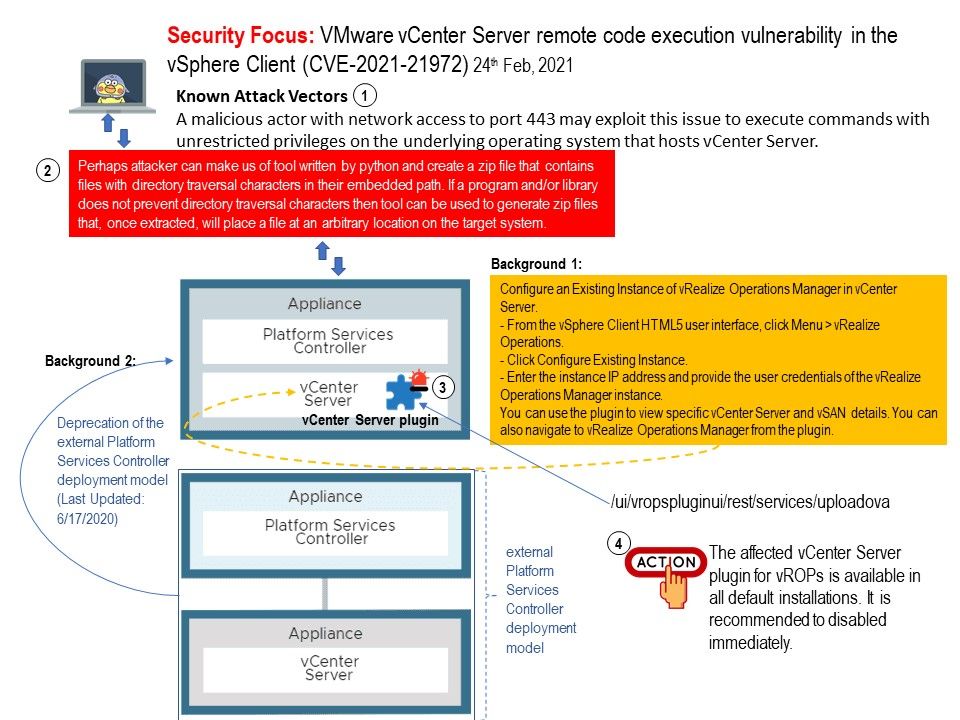
Background: The earlier release of vRealize Operations Manager with vCenter Server was shipped with the NGC plugin. The new vRealize Operations Manager plugin in vCenter Server, provides a mechanism to provide specific metrics and high-level information about data centers, datastores, VMs, and hosts, for the vCenter Server and vSAN. The plugin is supported only in the HTML5 version of the vSphere Client.
Reminder: If an administrator installs a plug-in in an instance of the vSphere Web Client, the plug-in can execute arbitrary commands with the privilege level of that administrator.
Vulnerability details: The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin.
Scenario: Perhaps attacker can make us of tool written by python and create a zip file that contains files with directory traversal characters in their embedded path. If a program and/or library does not prevent directory traversal characters then tool can be used to generate zip files that, once extracted, will place a file at an arbitrary location on the target system.
Workaround: The affected vCenter Server plugin for vROPs is available in all default installations. It is recommended to disabled immediately. Official recommendation: https://kb.vmware.com/s/article/82374
Remediation: To remediate CVE-2021-21972 apply the updates. Please refer to link – https://www.vmware.com/security/advisories/VMSA-2021-0002.html