Background: Remote Procedure Call (RPC) TCP port 135 is used for client-server communications by Microsoft Message Queuing (MSMQ) as well as other Microsoft Windows/Windows Server software.Allowing unrestricted RPC access on TCP port 135 can increase opportunities for malicious activities such as hacking (backdoor command shell).
Recent RCP-related vulnerabilities in software product:
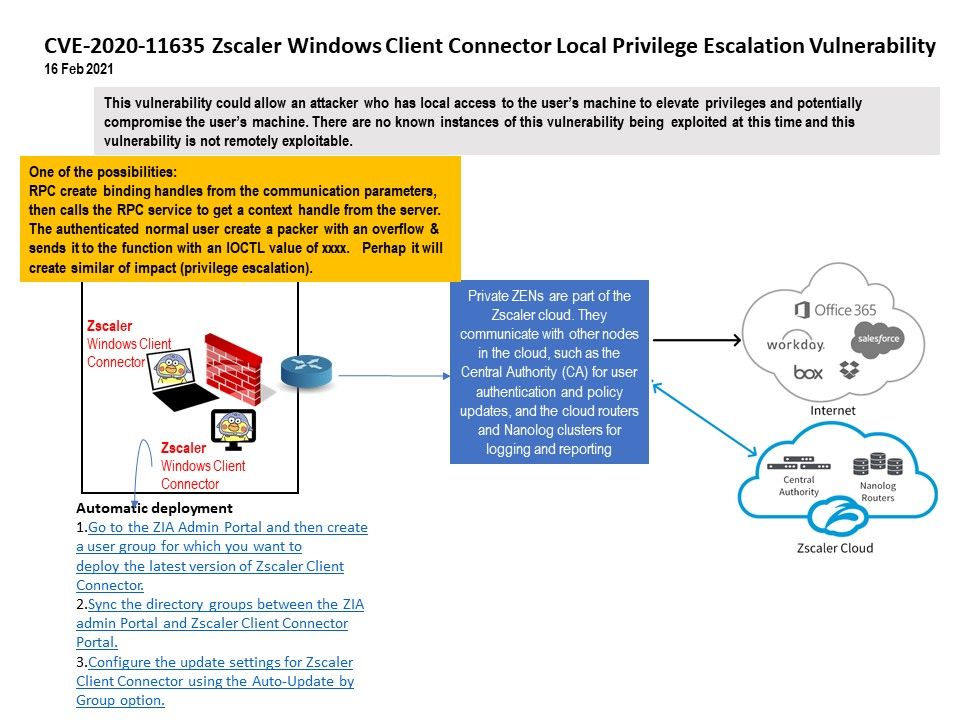
CVE-2020-11635: The Zscaler Client Connector prior to 3.1.0 did not sufficiently validate RPC clients, which allows a local adversary to execute code with system privileges or perform limited actions for which they did not have privileges.
Current status: This vulnerability could allow an attacker who has local access to the user’s machine to elevate privileges and potentially compromise the user’s machine. There are no known instances of this vulnerability being exploited at this time and this vulnerability is not remotely exploitable.
Official announcement and remedy solution – https://trust.zscaler.com/posts/7316