Preface: SaltStack was acquired by VMware on October 13, 2020. All SaltStack commercial information can be found on VMware.com. For the Salt open source project, visit saltproject.io
Background: SaltStack is a configuration management and orchestration tool. It uses a central repository to configure new servers and other IT infrastructure in Cloud computing environment. It can make changes to existing servers and computing devices and install software in the system environment. It allow to manage and scale cloud infrastructure with no downtime or interruptions.
There are 139 companies reportedly use Salt in their tech stacks, including Robinhood, Lyft, and LinkedIn.
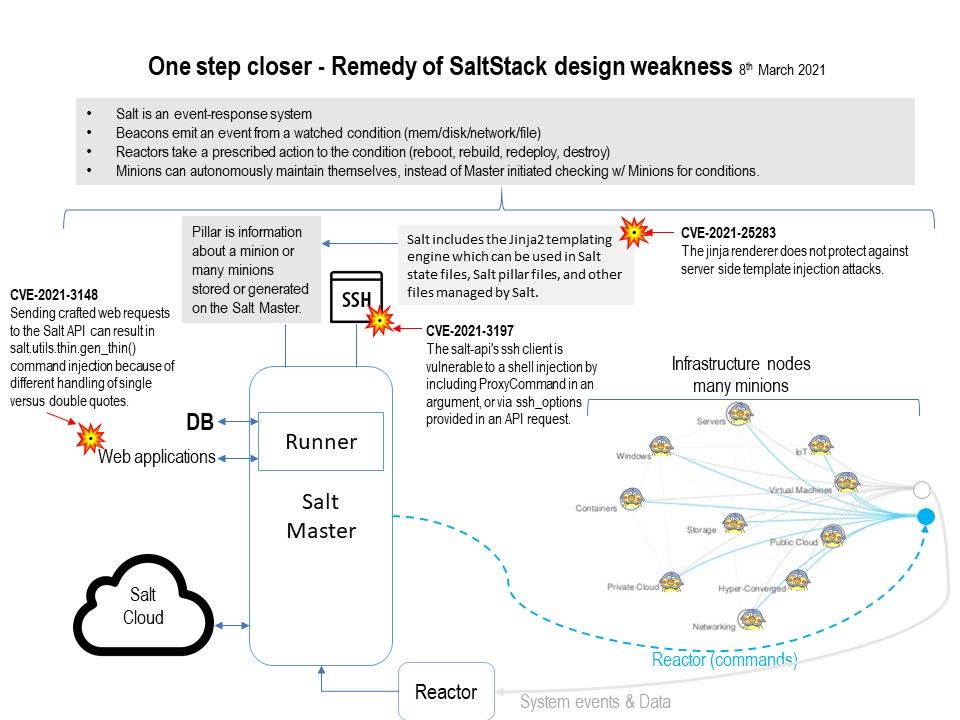
Official announcement: All related vulnerabilities and remediation can be found in this link – https://saltproject.io/security_announcements/active-saltstack-cve-release-2021-feb-25/
Security Focus: Modern system architecture design will simplifies the synchronization process in order to update the whole system infrastructure. For example: Blockchain will relies on Atomic Broadcast update all the network. Furthermore, SaltStack can be synchronizing all (minions) of this command (salt * saltutil.sync_all). If access control not in correct way. It will impact by vulnerability found on this time. CVE-2021-25281 – salt-api does not honor eauth credentials for the wheel_async client. Thus, an attacker can remotely run any wheel modules on the master. So we must staying alert!